1.6 Typical Ways to Use the Identity Applications
Here are some examples of how people typically use the identity applications within an organization.
1.6.1 How Identity Self-Service Works
-
Ella (an end user) recovers her forgotten password through the identity self-service features when logging in.
By default, Identity Manager uses Self Service Password Reset (SSPR) to allow users to modify their passwords. However, the identity applications can use other methods for managing forgotten passwords.
-
Erik (an end user) performs a search for all employees who speak German at his location.
-
Eduardo (an end user) browses the organization chart, finds Ella, and clicks the e-mail icon to send a message to her.
1.6.2 How Roles and Resources Work
Following is an example that explains the flow of roles and resources request in the system:
Figure 1-3 Example Scenario of Role Assignment
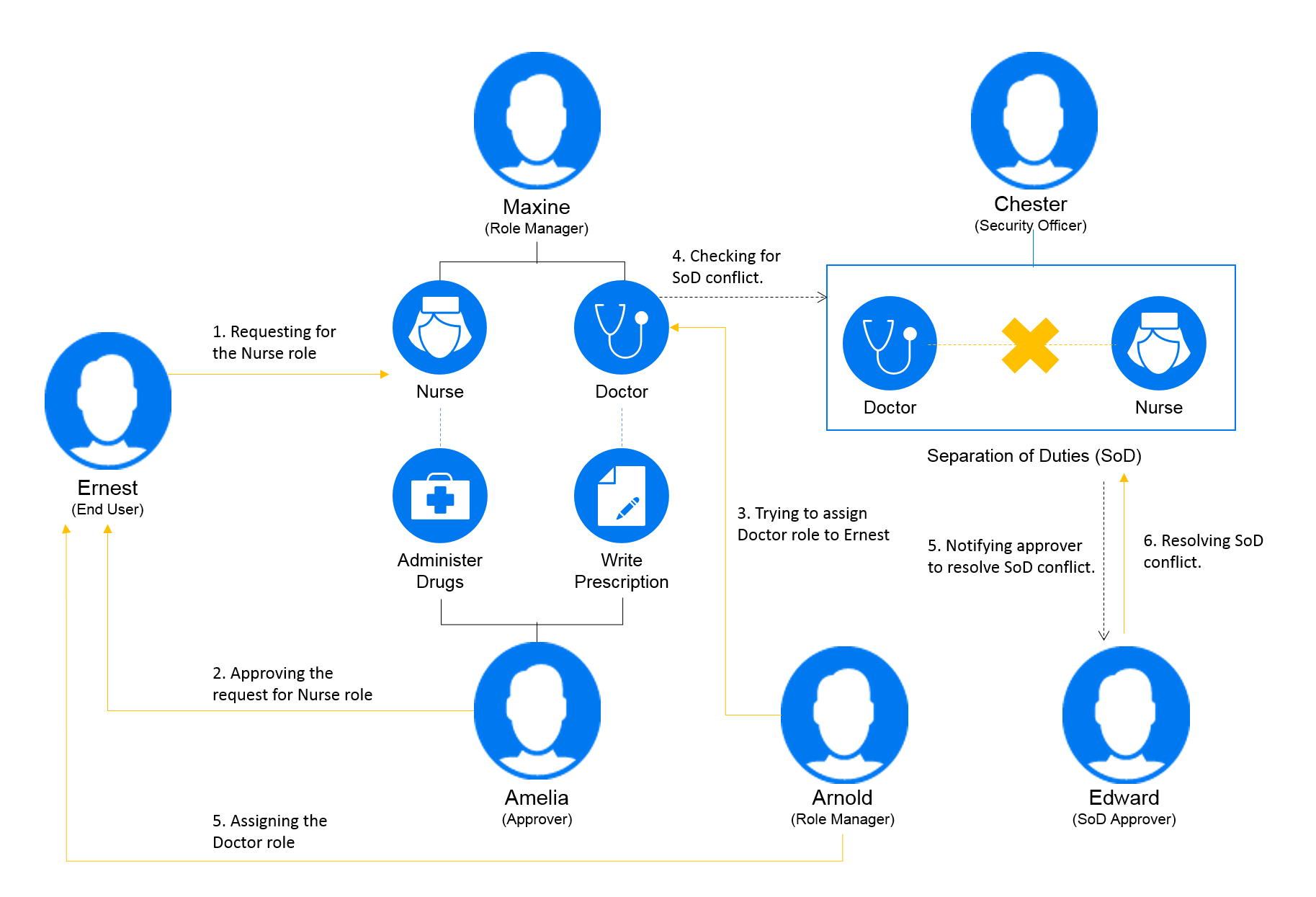
-
Maxine (a Role Manager) creates the Nurse and Doctor business roles and the Administer Drugs and Write Prescriptions IT roles. Maxine creates several resources that are needed for these roles, and associates the resources with the roles.
-
Maxine (a Role Manager) defines a relationship between the Nurse and Administer Drugs roles, specifying that the Nurse role contains the Administer Drugs role. Max also defines a relationship between the Write Prescriptions and Doctor roles, specifying that the Doctor role contains the Write Prescriptions role.
-
Chester (a Security Officer) defines a separation of duties constraint that specifies that a potential conflict exists between the Doctor and Nurse roles. This means that ordinarily the same user should be not assigned to both roles at the same time. In some circumstances, an individual who requests a role assignment may want to override this constraint. To define a separation of duties exception, the individual who requests the assignment must provide a justification.
-
Ernest (an end user) browses a list of roles available to him, and requests assignment to the Nurse role.
-
Amelia (an approver) receives notification of an approval request via e-mail (which contains an URL). She clicks the link, is presented with an approval form, and approves it.
-
Arnold (a Role Manager) requests that Ernest be assigned to the Doctor role. He is notified that a potential conflict exists between the Doctor role and Nurse role, to which Ernest has already been assigned. He provides a justification for making an exception to the separation of duties constraint.
-
Edward (a separation of duties approver) receives notification of a separation of duties conflict via e-mail. He approves Arnold’s request to override the separation of duties constraint.
-
Amelia (an approver) receives notification of an approval request for the Doctor role via e-mail. She approves the Arnold’s request to assign Ernest to the Doctor role.
-
Bill (a Role Auditor) looks at the SoD Violations and Exceptions Report and sees that Ernest has been assigned to both the Doctor and Nurse roles. In addition, he sees that Ernest has been assigned the resources associated with these roles.
1.6.3 How Process Requests Work
-
Ernie (an end user) browses a list of resources available to him, and requests access to the Siebel* system.
-
Amy (an approver) receives notification of an approval request via e-mail (which contains an URL). She clicks the link, is presented with an approval form, and approves it.
-
Ernie checks on the status of his previous request for Siebel access (which has now gone to a second person for approval). He sees that it is still in progress.
-
Amy is going on vacation, so she indicates that she is temporarily unavailable. No new approval tasks are assigned to her while she is unavailable.
-
Amy opens her approval task list, sees that there are too many for her to respond to in a timely manner, and reassigns several to co-workers.
-
Pat (an administrative assistant, acting as a proxy user for Amy) opens Amy’s task list and performs an approval task for her.
-
Max (a manager) views the task lists of people in his department. He knows that Amy is on vacation, so he reassigns tasks to others in his department.
-
Max initiates a request for a database account for someone in his department who reports directly to him.
-
Max assigns Dan to be an authorized delegate for Amy.
-
Dan (now a delegated approver) receives Amy’s tasks when she is unavailable.
-
Max engages an unpaid intern, who should not be entered into the HR system. The system administrator creates the user record for this intern and requests that he be given access to Notes, Active Directory*, and Oracle*.
1.6.4 How Helpdesk Works?
Following is an example that explains the flow of helpdesk ticket in the system:
Figure 1-4 Example for Helpdesk
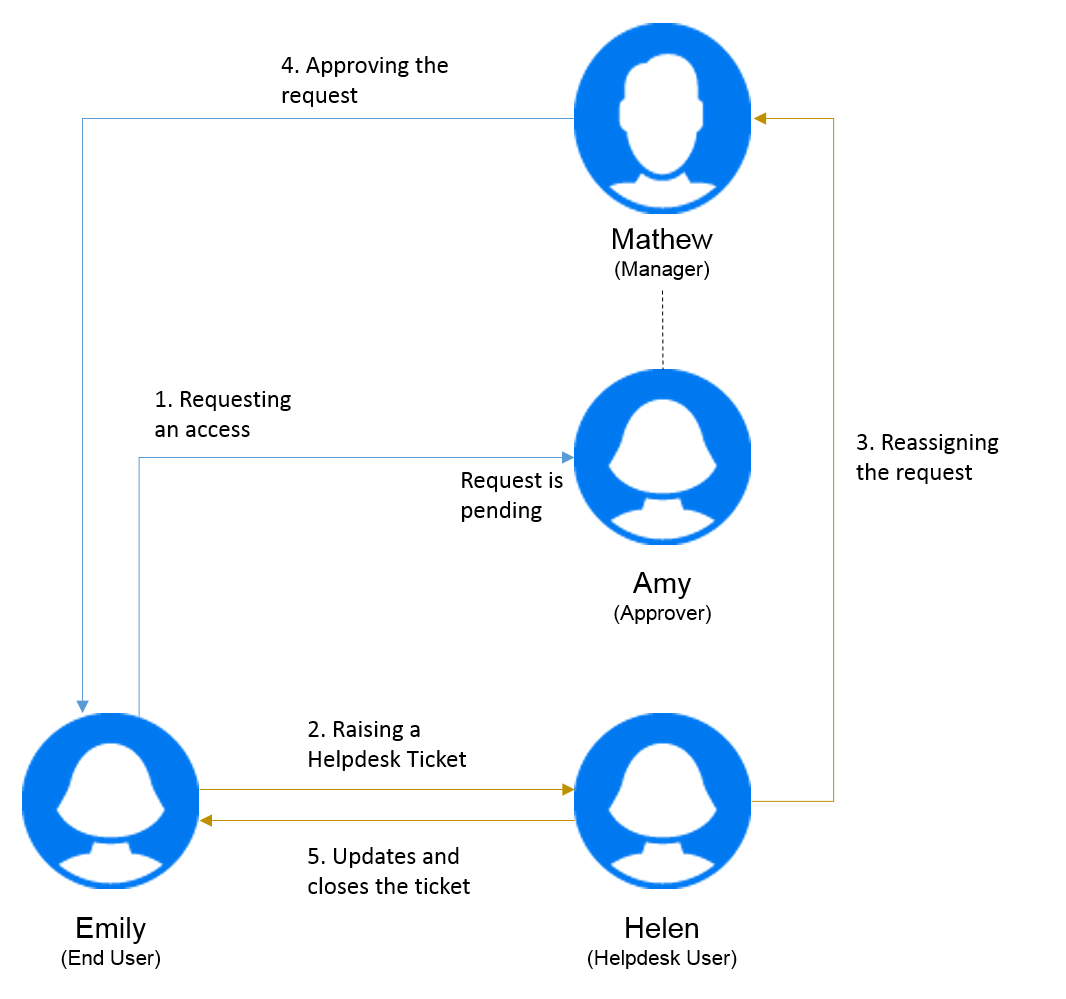
-
Emily (an end user) has requested for an office printer access. This request was pending for a long time. Therefore, she raised a helpdesk ticket.
-
Helen (a helpdesk user) receives a notification of the helpdesk ticket in her list of tasks.
-
Helen analyzes the issue and finds out that request is assigned to Amy (an approver).
-
This request is pending in the system because Amy is out of office.
-
Helen has a permission to reassign task requests. She reassigns this request to Mathew (Amy’s manager).
-
Mathew reviews the request and approves it. Emily can access the office printer.
-
Helen updates and closes the helpdesk ticket.