2.1 Preparing for Installation
This section provides the prerequisites, considerations, and system setup needed to install the driver:
2.1.1 Prerequisites for Driver
The driver requires the following applications:
-
Identity Manager 4.6 or later
-
Identity Manager Designer 4.6 or later
-
Identity Manager REST driver 1.0.0.1 or later
2.1.2 Prerequisites for Identity Manager Exchange Service
-
Microsoft Windows Server 2008 R2, Microsoft Windows Server 2012, Microsoft Windows Server 2012 R2, or Microsoft Windows Server 2016
-
Microsoft Windows Management Framework 4.0 (required for Windows Server 2008 R2)
-
Microsoft .NET Framework Version 4.5 or later
NOTE:You need to additionally install Microsoft .NET Framework 4.5 on Windows Server 2008 R2.
-
Microsoft Visual C++ 2012 Redistributable packages
For installing instructions, visit the Microsoft download page.
-
Microsoft Online Services Sign-In Assistant version 7.250.4556.0 and later
-
Windows Azure AD Module for Windows PowerShell on the computer where you will install Windows Powershell service. Click Windows Azure Active Directory Module for Windows PowerShell (64-bit version) from this page.
Identity Manager Exchange Service can be run on a user configured port. However, the service cannot be used with any other REST client tools.
2.1.3 Prerequisites for OAuth 2.0
The driver uses OAuth 2.0 protocol to authenticate to Azure AD. To support this protocol for authentication, you need to have a proxy application for the Azure AD driver on Azure AD. The Client ID and Client Secret allotted to the application will be later used in the Azure AD driver configuration. For more information about Azure Active Directory Application Proxy, see Microsoft Azure documentation.
Creating a Proxy Application on Azure AD
-
Log in to the Azure portal.
For example, https://manage.windowsazure.com or https://portal.azure.com. In this section, we have used https://manage.windowsazure.com as an example.
-
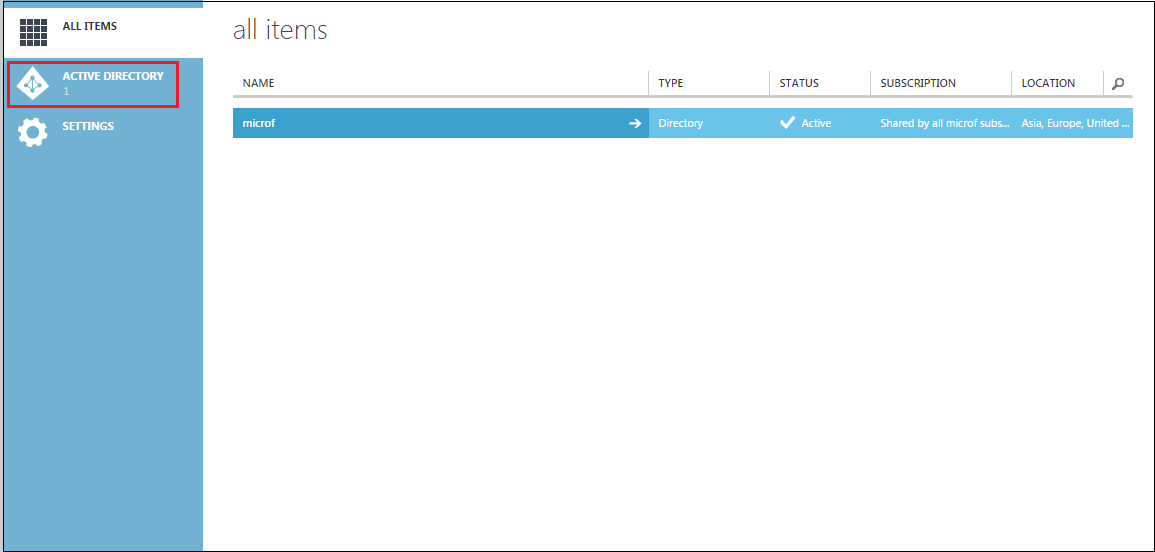
Select Active Directory from the left pane of the portal.
-
Select the default Active Directory from the right pane of the portal.
-
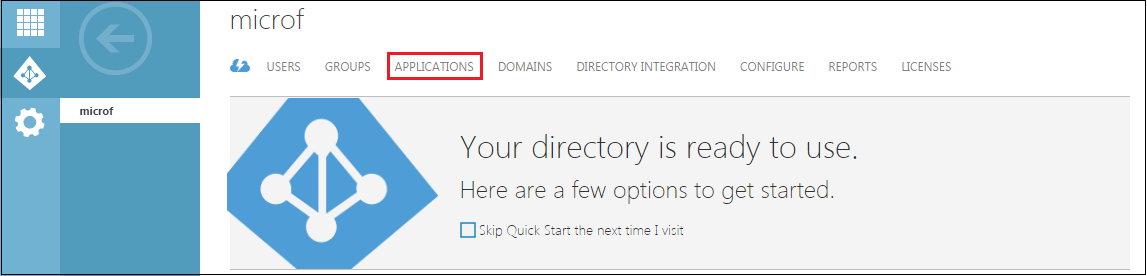
Click Applications.
-
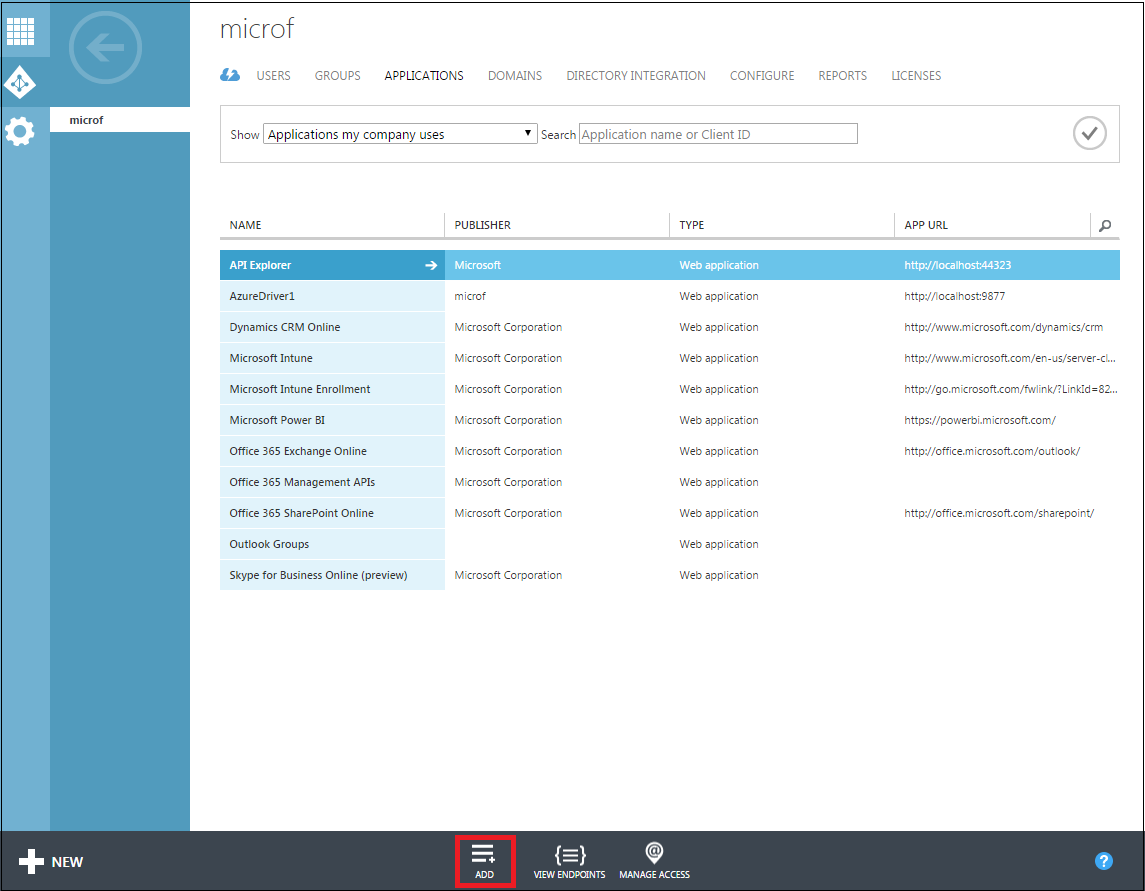
Click Add.
-
On the What you want to do page, click Add an application my organization is developing.
-
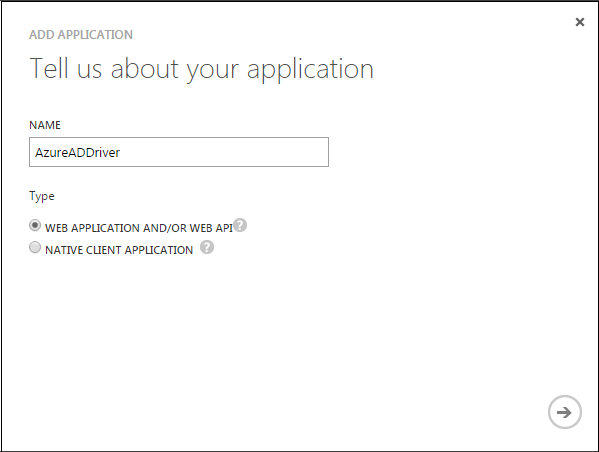
On the Add Application page, specify a name for your application and select Web Application And/Or Web API. For example, AzureADDriver
-
Specify the following in the Add Application page:
-
Sign-on URL: Specify a URL for the users to sign in and use the application. For example, http://localhost.
-
App ID URI: Specify a URI that Azure AD can use for the application you created. For example, http://localhost.
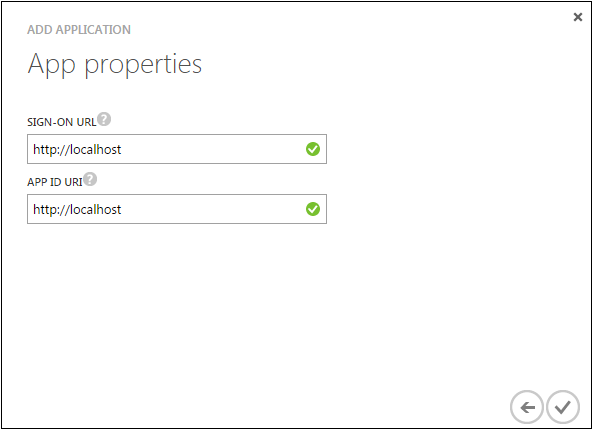
Now your application is created.
-
-
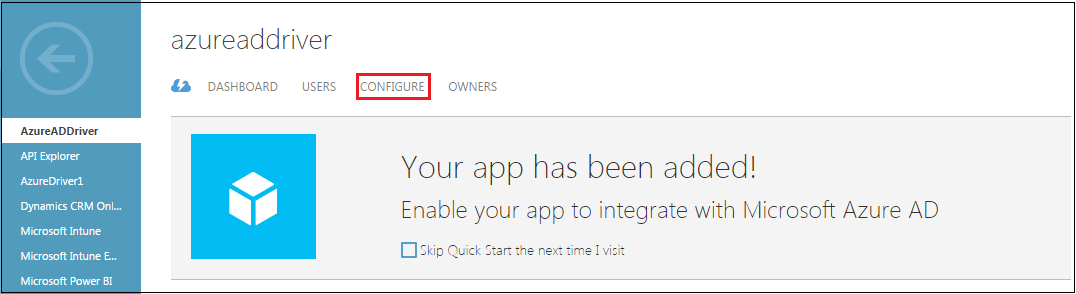
Click Configure.
-
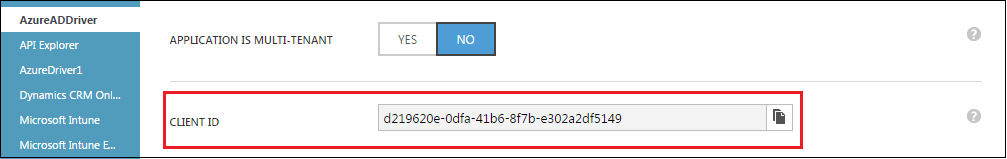
Copy and take a note of the Client ID for your application. You will need this value later for configuring the driver.
For information about configuring the Client ID, see Step 9 of Installing the Driver Packages section.
-
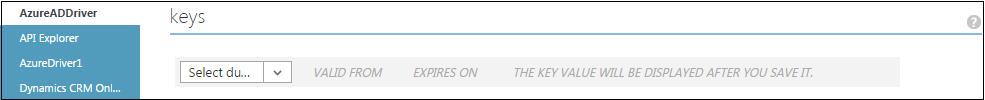
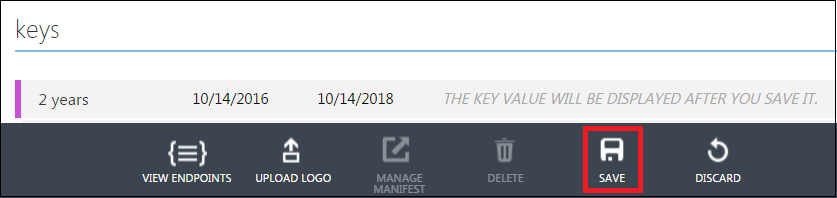
Under the Keys section, select a duration for the validity of your password.
-
Click Save to create the key for your application.
The key is Client Secret for your application. For information about configuring the Client Secret, see Step 9 of Installing the Driver Packages section.
IMPORTANT:Copy and take a note of the Client Secret. You cannot retrieve the Client Secret at a later point.
Assigning the Rights to the Application
-
Log in to PowerShell and connect to the Office 365 Exchange Online service by using the following command:
Connect-MSolService
-
To obtain the Client ID for your application, replace <AppPrincipalId> with the Client ID that you obtained in Step 10 from Creating a Proxy Application on Azure AD and run the following commands in PowerShell.
Get-MsolServicePrincipal | ft DisplayName, <AppPrincipalId> -AutoSize $ClientIdWebApp = ’<AppPrincipalId>’ $webApp = Get-MsolServicePrincipal –AppPrincipalId $ClientIdWebApp
-
Assign the Company Administrator rights to your application using the Client ID obtained in Step 2 by running the following command:
Add-MsolRoleMember -RoleName "Company Administrator" -RoleMemberType ServicePrincipal -RoleMemberObjectId $webApp.ObjectID
The Company Administrator role will give you rights to delete the directory objects.