14.2 Understanding Business Roles
The workflow shows the business role process in Identity Governance.
Figure 14-2 Business Role Workflow
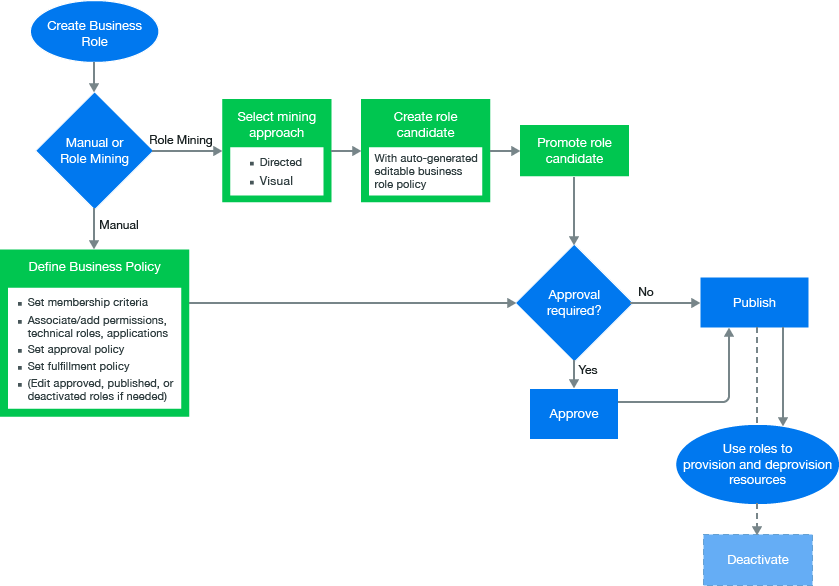
The primary purpose of business roles is to specify a set of applications, roles, and permissions that each member of a business role is authorized to access. The set of authorized resources is defined by each business role’s authorization policy. A business role authorizes resources and generates requests, but does not assign resources.
14.2.1 Understanding Business Role Access Authorizations
The Business Role or Global administrator creates, modifies, and defines business roles and manages business role policies. The Business Role or Global administrator can delegate administrative actions by specifying a Role Owner or a Role Manager for each business role. The Role Owners can view and approve business roles but cannot edit business roles. The Role Managers can edit business role membership and resource authorizations, submit business role for approval, promote role candidates, publish roles, and deactivate roles. If the administrator did not specify Role Owners in the business role definition, then Identity Governance automatically assigns the Business Role or Global administrator who created the role as the Role Owner. For more information about access authorizations, see Section 1.1, Understanding Authorizations in Identity Governance.
14.2.2 Understanding Business Role Mining
Identity Governance uses advanced analytics to mine business data and identify role candidates. This process of discovering and analyzing business data in order to group multiple users and access rights under one business role candidate is called Business Role Mining or Role Discovery. The Global or Business Role administrators can use role mining to reduce complexity in defining roles, and easily select role candidates with authorized users, permissions, technical roles, and applications to create business roles as well as technical roles with common permissions. Identity Governance uses two approaches to business role mining to identify business role candidates.
-
Directed Role Mining enables administrators to direct the mining based on user attributes they specify. If administrators are not sure which attribute to select, they can search for recommended attributes, and select an attribute from the recommended bar graph which displays the strength of attributes that have data. Additionally, directed role mining also enables them to specify minimum membership and coverage percentage to identify role candidates. For example, when an administrator selects “Department” as the attribute to group candidates by, the mining results displays the list of items consisting of department name with the associated users, permissions, roles, and application as role candidates.
-
Visual Role Mining enables administrators to select role candidates from a visual representation of the user attributes. The attribute circle’s width displays the strength of the recommendation, and the width and darkness of the lines indicate the affinity of the attribute to other user attributes. Administrations can customize the mining results by modifying the default maximum number of results, minimum potential members, and number of automatic recommendations.
NOTE:Role recommendations are dependent on your data and role mining settings. To optimize search results, administrators can modify default role mining settings in Configuration > Analytics and Role Mining Settings. For more information see, Configuring Analytics and Role Mining Settings.
After previewing users and their associated permissions, technical roles, and applications, administrators can select one or more items from the list to create either role candidates for each selected item in the list or a single candidate for all of them. Additionally, Identity Governance could group common permissions under a technical role, and generate technical role candidate for each application.
NOTE:Identity Governance creates the mined business or technical roles in a candidate state. Administrators can edit and save role candidates, but they must promote candidates before they can approve or publish the candidate as a role. Administrators can also select multiple role candidates and submit them for approval, publish them, or delete them using the Actions options.
14.2.3 Understanding Business Role States
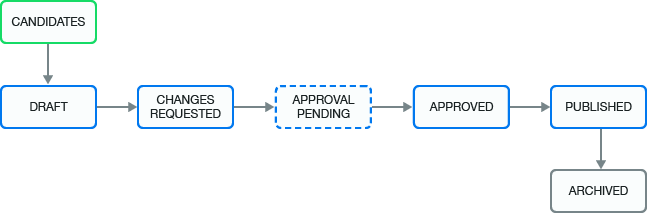
After you create or Identity Governance mines a business role, it contains many states during its life cycle. From beginning to end, the business role goes through the states in Figure 14-3. For detailed description of the states see the following table.
Figure 14-3 Business Role States
|
Business Role State |
Description |
|---|---|
|
CANDIDATES |
The mining process created the business role and the administrators must promote it before they or others can approve (depending on the approval policy) and publish it. This state corresponds to the internal state called MINED. |
|
DRAFT |
The assigned approval policy requires approval and the administrator has not submitted the changes for approval. |
|
CHANGES REQUESTED |
The approver denies approval of a business role. This state corresponds to the internal state called REJECTED. |
|
APPROVAL PENDING |
Pending changes are ready for approval by the approver specified in the approval policy. This state corresponds to the internal state called PENDING_APPROVAL. |
|
APPROVED |
The approver approved the business role, but the business role has not yet been published. |
|
PUBLISHED |
Business role is approved and the administrator has published the role. |
|
ARCHIVED |
An administrator deletes the policy or creates a new version. Identity Governance archives the policy for history and reporting. Identity Governance never displays archived business roles in the application. |