16.1 Using Secure Thin Client Services
The secure thin client provides secure access to thin-client server applications through the iChain Proxy server. iChain provides a secure gatekeeper functionality that protects HTTP applications. By enabling you to move all Web resources out of a demilitarized zone (DMZ) from your secure network to the Internet, iChain effectively removes users' direct access to Web applications and directory information.
As you deploy Web-based solutions to your users, one of the common services is thin client application delivery from vendors such as Citrix (terminal server based on ICA protocol). Using iChain to extend security to these thin client applications requires an iChain authentication before access is granted to the thin client server.
The advantages of using iChain to secure your Citrix thin-client applications include the following:
-
Authentication is performed by iChain before any access is allowed to the MetaFrame server or its published applications.
-
You don't need to open port 1494 (the MetaFrame server's well-known port) on the external firewall.
-
iChain user credentials are not exposed and do not get passed on the wire.
-
A one-time iChain token is encrypted and is time-sensitive.
-
Single sign-on to MetaFrame servers can be done either with or without Nfuse*.
-
You can handle multiple back-end MetaFrame servers through a single secure iChain tunnel.
-
Private IP addresses or domain names of back-end MetaFrame servers are not exposed on the wire or in the ICA session file.
The following sections are included:
16.1.1 Secure Access to Citrix Thin Clients
iChain provides secure access to Citrix-based thin-client services that use the Citrix ICA protocol. This includes single sign-on to Citrix Nfuse and iChain-authenticated access to Citrix MetaFrame servers.
Before a session can be established through iChain to a protected Citrix MetaFrame server, the user must have an iChain authentication token. The only way for the user to receive this token is to be authenticated to iChain at the time the Citrix client attempts to connect to the MetaFrame server.
iChain's secure access for the Citrix thin client also provides the additional benefit of supporting Citrix client connections over standard port:80 (client to iChain proxy).
NOTE:If you are running the Citrix Secure Gateway (CSG) solution, you do not need to enable all of the Citrix-related iChain settings. You only need to configure iChain to accelerate the Citrix CSG server in tunnel mode. Tunnel mode is required since unlike HTTP, Secure Gateway ICA connections cannot have their SSL layer terminated and recreated by a proxy server inserted between the ICA Client and the secure gateway server.
16.1.2 Configuring iChain to Accelerate Citrix MetaFrame Servers with Nfuse
To enable a secure iChain tunnel:
-
Create an accelerator (for example, www.metaframe.com).
This will be the accelerator used for the ICA tunnel.
If there are multiple MetaFrame servers, you must include all of the IP addresses for all of the MetaFrame servers in the Web server addresses field. Do not enable authentication on this accelerator, because this will be a special MetaFrame accelerator. Do not select Act as a Tunnel. Because this is a special MetaFrame accelerator, refer to Step 3 on how to enable the ICA tunnel.
-
The ICA tunnel accelerator (for example, www.metaframe.com) is a special type of Citrix tunnel that requires a forward proxy authentication between the client and iChain. It acts as a tunnel from iChain to the backend MetaFrame server. You can configure it at the iChain Proxy console. Enter the following command to enable the ICA thin client tunnel:
set accelerator accelerator name tunnelauthforica = yes
This command is only used on the ICA tunnel accelerator (www.metaframe.com) and not on the Nfuse accelerator (www.nfuse.com).
-
Create another accelerator (for example, www.nfuse.com) that secures the Nfuse Web server. Enable authentication or any of iChain's other advanced features.
-
Configure Form Fill rules for single sign-on to the Nfuse Web server so that Form Fill can fill the redirect information and one-time token into an ICA file. A Citrix client will use this rendered ICA file to launch a session to the iChain accelerator you created in Step 1 (for example, www.metaframe.com).
The following section is an example of how you can configure the Form Fill rules for single sign-on to the Nfuse Web server (www.nfuse.com) and rewrite the ICA file so that the client connects to the ICA tunnel accelerator (www.metaframe.com).
IMPORTANT:Form Fill tags are case sensitive. If you disregard the case with your tags (for example, if you use <icafill> instead of <icaFill>), single sign-on to your back-end applications might fail.
Sample Form Fill Configuration File for Citrix MetaFrame Server with Nfuse
<!-- Nfuse Single Sign-On login -->
<urlPolicy>
<name>MyNfuseLogin</name>
<url>www.Nfuse.com/Citrix/Metaframe/login.asp</url>
<actions>
<fill>
<input name=”user” value=”~”>
<input name=”password” value=”~”>
<input name=”domain” value=”~”>
</fill>
<post/>
</actions>
</urlPolicy>
<!- end of Nfuse login -->
<!-- Nfuse Single Sign-On logout -->
<urlPolicy>
<name>MyNfuseLogout</name>
<url>www.Nfuse.com/Citrix/Metaframe/logout.asp</url>
<actions>
<redirect>/cmd/BM-Logout.html</redirect>
</actions>
</urlPolicy>
<!- end of Nfuse logout -->
<!- secure tunnel to MetaFrame with Nfuse -->
<urlPolicy>
<name>NfuseTest</name>
<url>www.Nfuse.com/Citrix/MetaFrame/launch.asp*</url>
<actions>
<icaFill>
<icaOriginal>
[WFClient]
</icaOriginal>
<icaReplace>
[WFClient]
ProxyHost=www.metaframe.com:80
ICHAIN-TOKEN
</icaReplace>
<icaMetaPrivateAddress>
Address=1.1.1.1
</icaMetaPrivateAddress>
<icaMetaPublicAddress>
Address=www.metaframe.com
</icaMetaPublicAddress>
</icaFill>
</actions>
</urlPolicy>
<!- end of secure tunnel to MetaFrame through Nfuse -->
WARNING:This Form Fill example does not work for the newer 9.x ICA clients. See TID 3663363
Understanding the ICA Form Fill Policy
The above-listed NfuseTest Form Fill policy rewrites the ICA file that is generated and sent to the client. When the client connects to the url within the <url> tags, Form Fill will perform the actions listed under the <actions> tag:
<url>www.Nfuse.com/Citrix/MetaFrame/launch.asp*</url>
The ICA Form Fill begins with the following tag value:
<icaFill>
The lines following the <icaFill> tag tell Form Fill to find and replace part of the ICA file. This inserts an encrypted one-time, time-sensitive (for example, 60 seconds) iChain token and redirects Citrix clients to www.metaframe.com port 80:
<icaOriginal>
[WFClient]
</icaOriginal>
<icaReplace>
[WFClient]
ProxyHost=www.metaframe.com:80
ICHAIN-TOKEN=60
</icaReplace>
Form Fill parses the ICA file, looking for the [WFClient] keyword, and replaces it with everything in the <icaReplace> section.
The following line is used to redirect a Citrix client to the ICA tunnel accelerator (www.metaframe.com) on port 80:
ProxyHost=www.metaframe.com:80
The following ICHAIN-TOKEN keyword instructs Form Fill to inject an encrypted one-time iChain token in seconds, where the default is 180 seconds (the minimum is 60 seconds, and the maximum is 600 seconds). This amount of time is configured by including an =<value> after ICHAIN-TOKEN. This ICHAIN-TOKEN is what the ICA client uses to authenticate to the ICA tunnel accelerator on www.metaframe.com. For example:
ICHAIN-TOKEN=60
The next part of the ICA Form Fill policy tells Form Fill to hide the private metaframe server IP address or the domain name with an iChain accelerator name. All of the <icaMetaPrivateAddress> Address= lines are replaced with the Address= line in the <icaMetaPublicAddress>.
<icaMetaPrivateAddress>
Address=1.1.1.1
</icaMetaPrivateAddress>
<icaMetaPublicAddress>
Address=www.metaframe.com
</icaMetaPublicAddress>
For 1.1.1.1 above, specify the domain name or IP address of the MetaFrame server from the ICA file.
<icaMetaPrivateAddress>
Address=1.1.1.1
</icaMetaPrivateAddress>
If there are multiple MetaFrame servers, you can add multiple entries within the <icaMetaPrivateAddress> field:
<icaMetaPrivateAddress>
Address=1.1.1.1
Address=2.2.2.2
</icaMetaPrivateAddress>
The <icaMetaPublicAddress> field is the ICA tunnel accelerator. Specify the domain name.
For example, in the www.metaframe.com above, enter the accelerator name that secures the ICA tunnel.
<icaMetaPublicAddress> Address=www.metaframe.com </icaMetaPublicAddress>
For troubleshooting information on configuring iChain to accelerate Citrix Metaframe servers, see the Appnote: setting up and troubleshooting the iChain/Citrix integration.
16.1.3 Configuring iChain to Accelerate Citrix MetaFrame Servers without Nfuse
If you configure iChain to accelerate Citrix Metaframe servers without Nfuse by making use of a static ICA file, be aware that load balancing/failover does not work in this scenario. The controlling entity for load balancing/failover becomes Citrix, which as part of this process, dynamically adds the IP address to connect to in the ICA file. On the Citrix side there is a check on what is the least busy and active server and based on the outcome, the IP address of that server is passed over to be injected in the ICA file. In case of a static ICA file, there are no dynamic updates to the file, so there is no load balancing/failover.
When Nfuse is not deployed, the following steps describe how you can configure iChain in order to accelerate sessions to your MetaFrame servers or applications on your MetaFrame servers.
On the MetaFrame server side:
-
Go to the MetaFrame servers where you want your applications to be secured by iChain.
-
Launch the Citrix Management Console on those servers.
-
Click Applications to display applications currently being published on the server.
-
Right-click the application or the desktop icons that you want iChain to secure and select Create ICA File.
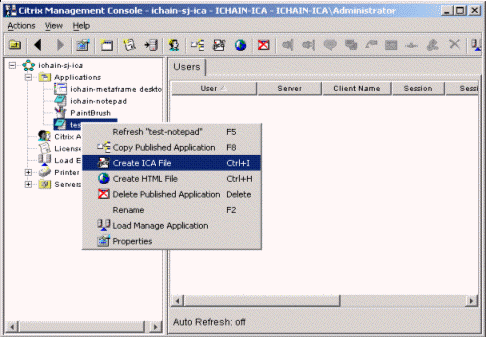
The ICA File Wizard launches.
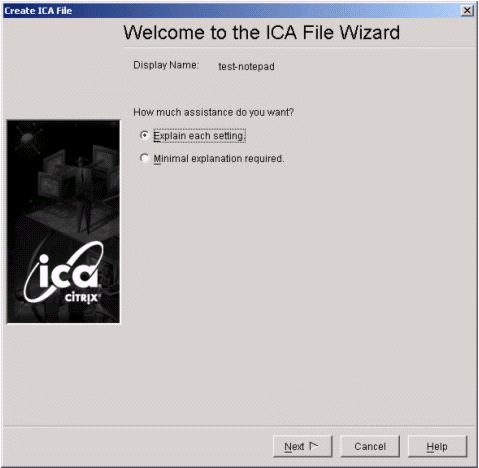
-
Complete the following options in the ICA File Wizard:
-
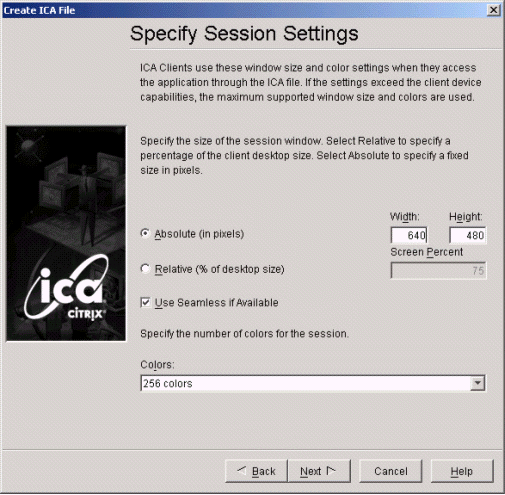
Specify the session settings.
-
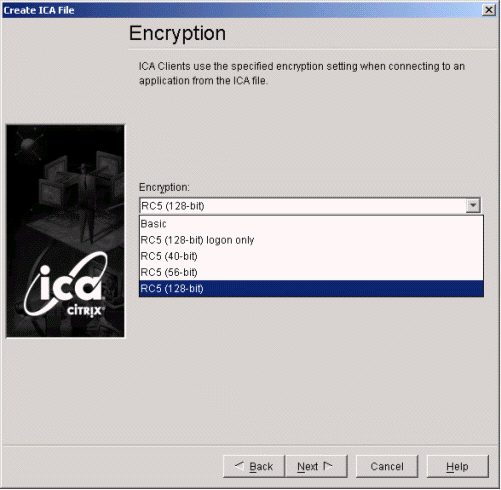
At the Encryption page, select RC5(128-bit).
-
Select Compress ICA data stream.
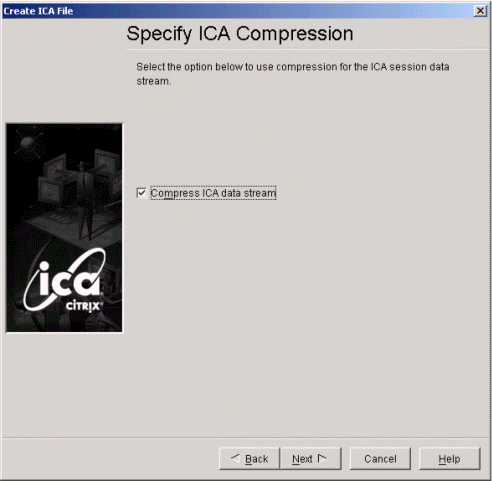
-
Select the audio setting.
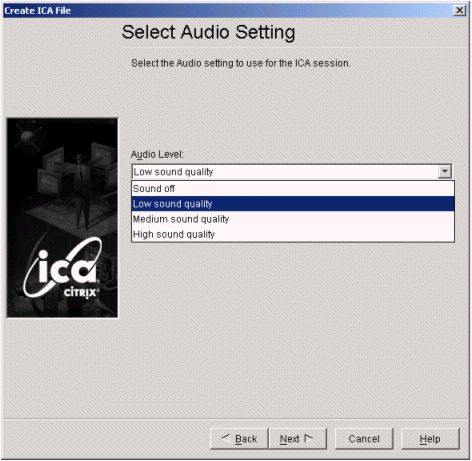
-
On the TCP/IP+HTTP Server page, do not check Use TCP/IP+HTTP Browsing.
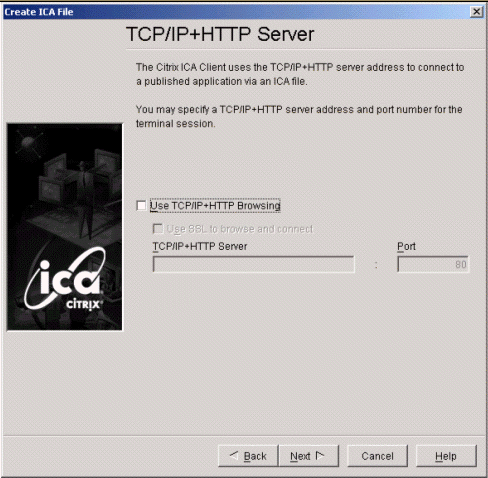
-
On the Specify ICA File Name page, specify the path where you want this file to be saved. Make note of the path that you enter.
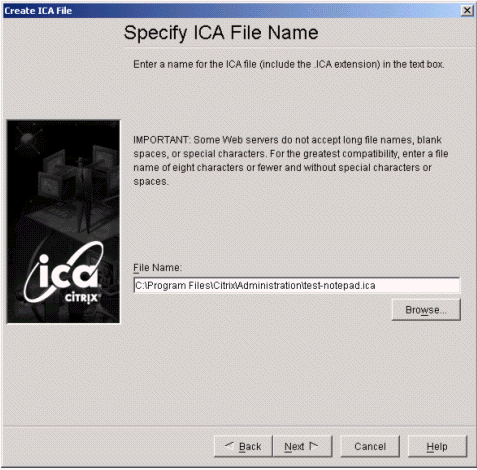
-
On the Create HTML File page, select No.
-
On the ICA File Summary page, click Finish.
-
-
Edit the file you created in Step 5.f:
In section [test-notepad], replace the Address=test-notepad with the IP address or domain name from section [WFClient] TCPBrowserAddress=1.2.3.4. Delete the TCPBrowserAddress=1.2.3.4 after forwards.
For example, a test-notepad.ica file is created with the following content:
[WFClient] Version=2 TCPBrowserAddress=1.2.3.4 [ApplicationServers] test-notepad= [test-notepad] Address=test-notepad
With the above sample ICA file, you would change it to:
[WFClient] Version=2 [ApplicationServers] test-notepad= [test-notepad] Address=1.2.3.4
-
Edit the file again by adding the following section of code before [WFClient] section. The added code is to make browser launch the Citrix’s plug-in accordingly.
<%@Language=VBScript%> <% Response.ContentType=”application/x-ica” %> [WFClient]
-
Save the modified file with an .asp extension and copy it to the Web server that you want iChain to secure.
The .asp file extension is necessary so that browser does not cache the page. This ensures that the browser asks for a new ICA file from iChain if a user clicks the same application again.
On the Web server:
-
Create your own custom HTML page by putting the above .asp file as a reference link.
-
Set up your ACL rules for the custom HTML page you created (including the ACL rules for your .asp file).
-
Configure the Form Fill rules when the .asp file in the HTML page is accessed.
In ConsoleOne®:
<!-- MetaFrame login -->
<urlPolicy>
<name>loginWithoutNfuse</name>
<url>www.native.com/ica/icalogin.html</url>
<formCriteria>
<title>CitrixNativeLogin</title>
</formCriteria>
<actions>
<fill>
<input name=”Username” value=”~cn”>
<input name=”ClearPassword” value=”~password”>
</fill>
</actions>
</urlPolicy>
<!- end of MetaFrame login -->
<!- secure tunnel to MetaFrame without Nfuse -->
<urlPolicy>
<name>NativeMFTest</name>
<url>www.native.com/ica/c-*</url>
<actions>
<icaFill>
<icaOriginal>
[WFClient]
</icaOriginal>
<icaReplace>
[WFClient]
ProxyHost=www.metaframe.com:80
ICHAIN-TOKEN
</icaReplace>
<icaMetaPrivateAddress>
Address=10.10.0.5
</icaMetaPrivateAddress>
<icaMetaPublicAddress>
Address=www.metaframe.com
</icaMetaPublicAddress>
<icaOriginal>
TransportDriver=TCP/IP
</icaOriginal>
<icaReplace>
TransportDriver=TCP/IP
ICHAIN-ICA-SSO-POLICY=loginWithoutNfuse
</icaReplace>
</icaFill>
</actions>
</urlPolicy>
<!- end of secure tunnel to MetaFrame without Nfuse -->
WARNING:This Form Fill example does not work for the newer 9.x ICA clients. See TID 3663363
There needs to be a Form Fill policy that is used for holding the username and password that will be added into the ICA file. In the above example, this is the <loginWithoutNFuse> Form Fill policy. See Section 14.0, Form Fill for advanced Form Fill functionality and configuration. The second <name>NativeMFTest</name> Form Fill policy looks similar to the above Form Fill policy used with Nfuse. See the above policy for the examination of the ICA Form Fill Policy. The difference with the Nfuse Form Fill policy and the Form Fill policy without Nfuse is another replacement within the ICA file listed below.
IMPORTANT:Login credentials to the MetaFrame server are inserted as clear text to an ICA file. The Citrix client saves this ICA file locally to launch a session.
<icaOriginal>
TransportDriver=TCP/IP
</icaOriginal>
<icaReplace>
TransportDriver=TCP/IP
ICHAIN-ICA-SSO-POLICY=loginWithoutNfuse
</icaReplace>
Form Fill looks for the following entries within the ICA file generated in the *.asp file created previously.
<icaOriginal>
TransportDriver=TCP/IP
</icaOriginal>
When Form Fill finds this entry, it replaces the it with the following:
<icaReplace>
TransportDriver=TCP/IP
ICHAIN-ICA-SSO-POLICY=loginWithoutNfuse
</icaReplace>
This instructs Form Fill to add the credentials within the <name>loginWithoutNFuse</name> Form Fill policy in the ICA file. These credentials are inserted into the ICA file as clear text. The user must be authenticated to iChain and the Form Fill Crib attributes must be available in order for Form Fill to insert the credentials listed in the ICHAIN-ICA-SSO-POLICY tag. When the credentials are added to the ICA file, iChain returns the ICA file to the client. The client then uses iChain's rewritten ICA file to connect to the MetaFrame accelerator on iChain with the credentials passed by the ICHAIN-ICA-SSO-POLICY.
For troubleshooting information on configuring iChain to accelerate Citrix Metaframe servers, see the Appnote: setting up and troubleshooting the iChain/Citrix integration.
16.1.4 Using the Citrix Java Client
To use the Citrix Java Client, your system must meet the following requirements:
-
The Citrix Presentation Server Client for JAVA 9.4 or later. Earlier versions incorrectly handle the encoding of the basic authentication header.
-
iChain 2.3 Service Pack 4 Interim Release IR1a or later. Earlier versions cannot retrieve the IP address which is enclosed in quotes.
You also need to create a form fill policy similar to the following sample policy:
<!-start of secure tunnel to MetaFrame with Java ICA clients-->
<urlPolicy>
<name>JavaCitrix</name>
<url>nw65.ichainsite.com/citrix/JavaClient/examples/desktop.html</url>
<actions>
<icaFill>
<icaOriginal>
<param name="Start" value="auto">
</icaOriginal>
<icaReplace>
<param name="Start" value="auto">
<param name="ProxyHost" value="citrix.ichainsite.com:80">
ICHAIN-JAVASCRIPT-TOKEN
</icaReplace>
<icaMetaPrivateAddress>
value="10.1.1.195"
</icaMetaPrivateAddress>
<icaMetaPublicAddress>
value="citrix.ichainsite.com"
</icaMetaPublicAddress>
</icaFill>
</actions>
</urlPolicy>
WARNING:This Form Fill example does not work for the newer 9.x ICA clients. See TID 3663363