8.1 Accelerator Authentication Parameter Page
In ConsoleOne, the fifth page of the iChain Web Server Accelerator Wizard is where you specify the accelerator authentication parameters. You can enable or disable authentication, enable or disable Secure Exchange, and create authentication profiles.
Figure 8-1 Accelerator Authentication Parameter Page
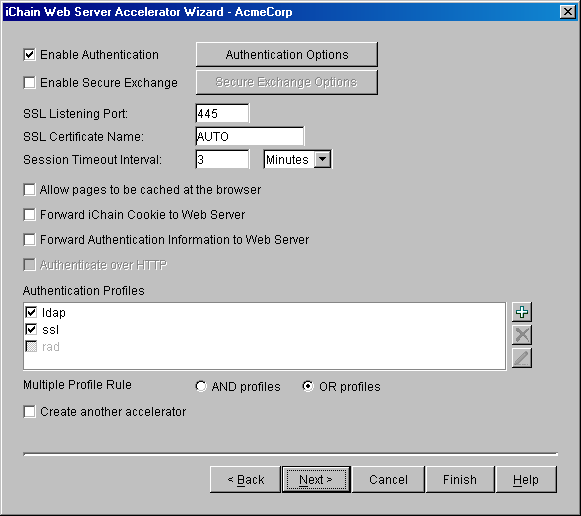
The following table describes the fields on this page:
|
Field Name |
Description |
Status |
|---|---|---|
|
Enable Authentication |
Selecting this option forces a user to authenticate to access this Web server |
Optional |
|
Enable Secure Exchange |
Selecting this option enables Secure Exchange (formerly known as SSLizer). Advanced options for Secure Exchange are not currently available from the wizard, but can be set from the proxy server administration application. |
Optional If you choose to enable this option, see Section 5.3, Using Third-Party Certificates for instructions on how to import the trusted root. Required to use Basic Authentication for LDAP. See Section 6.2, Enabling Authentication Through the HTTP Authorization Header |
|
SSL Listening Port |
The SSL port that the user is redirected to for authentication if Secure Exchange is enabled. |
Required if authentication or Secure Exchange is enabled |
|
SSL Certificate Name |
The certificate name for this accelerator. If the name does not appear in the drop-down list, it can be entered manually. |
Required if Secure Exchange is enabled |
|
Session Timeout Interval |
The amount of time a connection can be inactive before re-authentication is required. |
Required if authentication is enabled or Secure Exchange is enabled |
|
Forward iChain Cookie to Web Server |
Sends the Novell® iChain® cookie to the Web server along with the other data being sent. |
Optional |
|
Forward Authentication Information to Web Server |
Sends username and/or password to the Web server |
Optional |
|
Authenticate over HTTP |
Allows authentication over unencrypted HTTP instead of HTTPS. This feature is not compatible with RADIUS authentication profiles. |
Optional |
|
Authentication Profiles |
Each existing profile is listed; those in use appear with a check box. At least one profile must be selected when authentication is enabled. When multiple profiles are in the list, more than one can be enabled. Currently, only Mutual SSL profiles may be used with LDAP or RADIUS profiles. LDAP and RADIUS profiles cannot be used together. |
Required if authentication is enabled. |
|
Multiple Profile Rule |
Only valid if multiple Authentication Profiles are checked. Selects whether only one profile is required (OR) or if all selected authentication methods need to be fulfilled before authentication is granted (AND). OR is the default when multiple profiles are checked. |
|
|
Create another accelerator |
If this check box is selected when you select the Next button, the wizard returns to the Accelerator Specification Page where a new accelerator can be created. This saves you from needing to select the Next button followed by selecting the Back button three times to return to the Accelerator Specification Page. |
Optional |
8.1.1 Controls for Accelerator Authentication Parameters
Four buttons allow you to modify authentication parameters:
-
Advanced Options: Launches the Advanced Authentication Options dialog box as shown in Figure 8-2.
-
Add: Launches the Add Authentication Profile dialog box.
-
Delete: Allows you to delete an existing Authentication Profile.
-
Edit: Launches the Modify Authentication Profile dialog box.
8.1.2 Advanced Authentication Options Dialog Box
The Advanced Authentication Options dialog box allows you to specify advanced authentication options, including options that are set under special circumstances.
Figure 8-2 Advanced Authentication Options Dialog Box
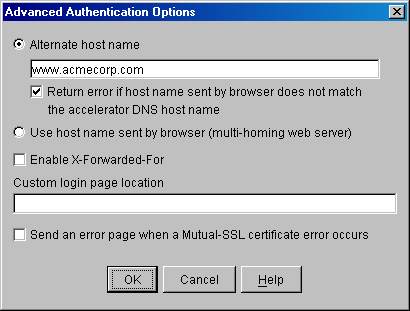
The following table describes the fields in this dialog box:
8.1.3 RADIUS Authentication Load Balance and Failover
Load balancing divides a computer's workload between two or more computers so more work can be accomplished in the same amount of time. For authentication, load balancing commonly distributes credential search requests in a fixed sequential order to the different servers.
This feature has a 60-second, non-configurable timeout period after which the authentication search cycle begins again.
When a configuration requires multiple servers, load balancing is often combined with failover. Failover is a backup operational mode where processes are shifted to another server if the primary server becomes unavailable. The failover process offloads tasks to a standby system component. Failover is different from load balancing. Instead of searching servers sequentially, it continues to search on one server until the information cannot be found or the server becomes inactive. Then it moves to the next server.
-
In the proxy server administration tool, click Configure, click the Authentication tab, select radius, then click Modify.
-
Select RADIUS Authentication, click RADIUS Options.
-
In the RADIUS Connect Mode drop-down menu, select FailOver or RoundRobin.
-
Click OK.
8.1.4 Add (Modify) Authentication Profile Dialog Box
The Add Authentication Profile dialog box allows you to name and create authentication profiles. The Modify Authentication Profile dialog box is exactly the same except for the dialog box title.
Figure 8-3 Add Authentication Profile Dialog Box
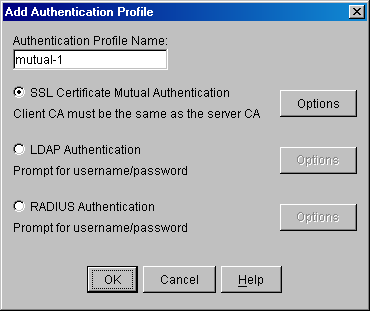
The following table describes the fields in this dialog box:
8.1.5 Mutual Certificate Mapping Dialog Box
The Mutual Certificate Mapping dialog box allows you to configure certificate mapping types. See Figure 8-4.
Figure 8-4 Mutual Certificate Mapping Dialog Box
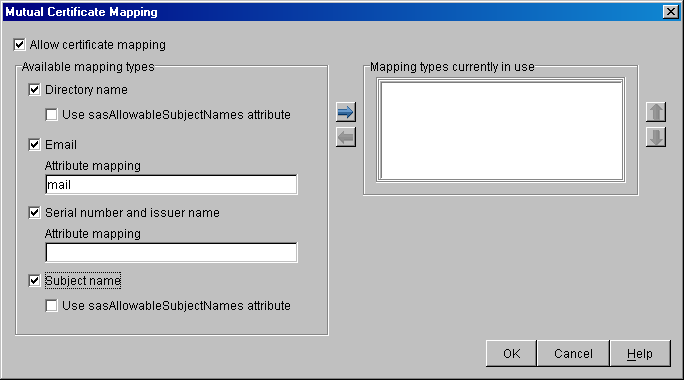
The following table describes the fields and buttons in this dialog box:
|
Field Name or Button |
Description |
Status |
|---|---|---|
|
Directory Name |
Enables certificate mapping, which gives four ways to map the user certificate to a user in the iChain LDAP Authentication tree. |
Optional |
|
Use sasAllowableSubjectNames attribute |
If a user is not found with Directory Name and Use sasAllowableSubjectNames is also enabled for directory mapping, the LDAP Authentication tree is searched for a user containing an sasAllowableSubjectName attribute matching the Directory Name in the Subject Alternative Name field of the certificate. If sasAllowableSubjectName is enabled, the LDAP Authentication tree should be configured so that there is no duplication of allowed names between users in the sasAllowableSubjectName attribute. |
|
|
Email Description |
With Email mapping, there are two possible fields in the user certificate that can be used to identify the certificate portion of the user. The first is the Subject Alternative Name field in the user certificate, with a name type of RFC822. The second is when an e-mail name is embedded in the Subject field of the certificate. If both the Subject Field and the Subject Alternative Name field contain an e-mail address, the Subject Alternative Name is the only field used. |
|
|
Attribute Mapping |
This attribute is used to match the Email address from the certificate when searching for a user in the LDAP Authentication tree. The default LDAP attribute is mail, which is the attribute currently used by GroupWise® and Novell Certificate Server™. The LDAP Authentication tree should be configured so that there is no duplication of Email addresses between users in the configured email attribute mapping. |
|
|
Serial Number and Issuer Name |
With serial number and issuer name mapping, both the serial number and the issuer name fields from the certificate are used together to identify the certificate portion of the user. |
|
|
Attribute Mapping |
Both the issuer name and the serial number need to be put into the same LDAP attribute of the user. The LDAP attribute that is used is specified in this field. The LDAP attribute can be any Case Ignore List or Cast Ignore String attribute of the user. If you are configuring your own attribute, make sure the attribute is added to the Person class. |
|
|
Subject Name |
A user in the LDAP Authentication tree matching the Subject Name field of the certificate is checked first. |
|
|
Use sasAllowableSubjectNames Attribute |
If a user is not found with Subject name and Use sasAllowableSubjectNames is also enabled for directory name mapping, the LDAP Authentication tree will be searched for a user containing an sasAllowableSubjectName attribute matching the Directory Name in the Subject Alternative Name field of the certificate. If sasAllowableSubjectName is enabled, the LDAP Authentication tree should be configured so that there is no duplication of allowed names between users in the sasAllowableSubjectName attribute. |
|
|
Add |
The iChain Proxy Server can be configured to use any combination of the four mapping types. This button allows type to be added to the Mapping types currently in the use list. |
|
|
Remove |
Allows a type to be removed from Mapping types currently in the use list. |
|
|
Order Up |
Allows for a mapping type within the Mapping types currently in the use list to be moved up. NOTE:When searching for a user with the configured mappings, the first user found is the user that is used for authentication and access control, even if the other users map to the same certificate. See Using Certificate Mapping for more information. |
|
|
Order Down |
Allows for a mapping type within the Mapping types currently in the use list to be moved down. NOTE:When searching for a user with the configured mappings, the first user found is the user that is used for authentication and access control, even if the other users map to the same certificate. See Using Certificate Mapping for more information. |
|
8.1.6 Controls for Authentication Profiles
-
LDAP Options: Launches the LDAP Authentication Profile Options dialog box, which allows you to specify LDAP authentication parameters. It is functionally identical to the corresponding dialog box in the iChain Proxy Server administration application.
-
Radius Options: Launches the RADIUS options dialog box.
Figure 8-5 LDAP Authentication Profile Options Dialog Box
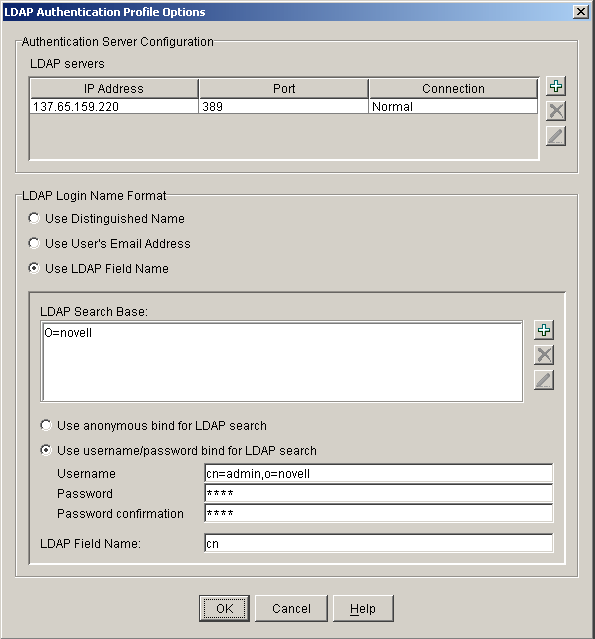
The following table describes the fields in this dialog box:
8.1.7 Controls for Authentication Profile Options
Use the following buttons to control the authentication profile:
-
Add LDAP Server: Allows you to launch the New LDAP Authentication Server dialog box.
-
Delete LDAP Server: Allows you to delete an authentication server from the list.
-
Edit LDAP Server: Allows you to launch the Modify LDAP Authentication server dialog box.
-
Add LDAP Context: Allows you to launch the dialog box to add an LDAP Search Base/User Context (if DN is selected).
-
Delete LDAP Context: Allows you to delete an LDAP Search Base/User Context from the list.
-
Edit LDAP Context: Allows you to launch the dialog box to modify an LDAP Search Base/User Context (if DN is selected).
8.1.8 New LDAP Authentication Server Dialog Box
The New LDAP Authentication Server dialog box allows you to specify the parameters for new LDAP authentication servers. The Modify LDAP Authentication Server dialog box is exactly the same except for the dialog box title.
Figure 8-6 New LDAP Authentication Server Dialog Box
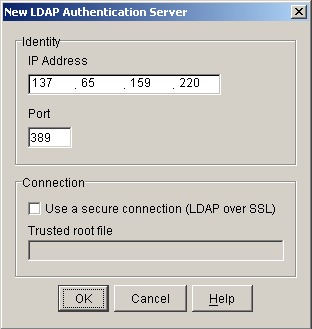
The following table describes the fields in this dialog box:
8.1.9 Add LDAP Context Dialog Box
The Add LDAP Context dialog box provides the input of LDAP search bases or user contexts. The Modify LDAP Context dialog box is exactly the same except for the dialog box title.
Figure 8-7 Add LDAP Context
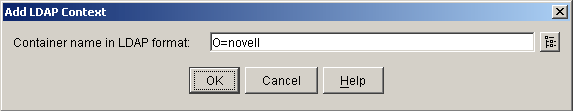
The following table describes the field in this dialog box:
8.1.10 Controls for Add LDAP Context
Use the Object Browser button to launch an object browser to select the desired container.
8.1.11 Radius Options Dialog Box
The Radius Options dialog box allows you to specify the parameters for RADIUS profiles. This dialog box is functionally identical to the corresponding iChain Proxy Server administration application dialog box.
Figure 8-8 RADIUS Profile Options Dialog Box
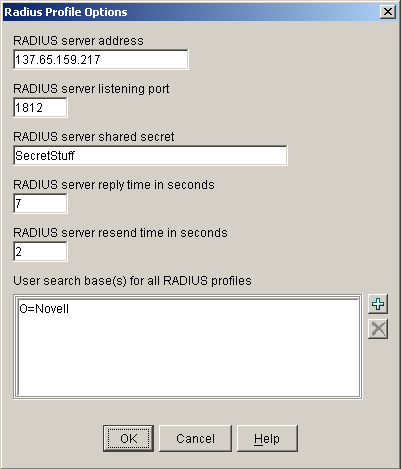
The following table describes the fields in this dialog box:
8.1.12 Controls for RADIUS Options
The following buttons allow you to add or delete search bases:
-
Add Search Base: Allows you to launch an object browser to select the desired container.
-
Delete Search Base: Allows you to delete a search base from the list.