A.3 Key Pairs
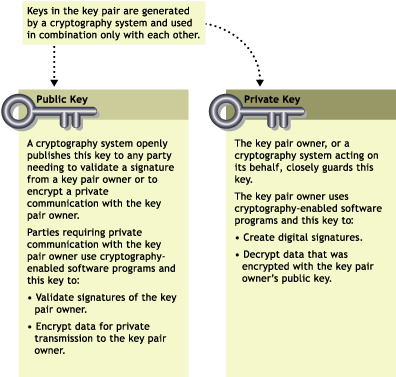
Authentication and encryption are both provided through the use of mathematically related pairs of digital codes or “keys.” One key in each pair is publicly distributed; the other is kept strictly private.
Each data transmitter, whether it is a person, a software program, or some other entity such as a bank or business, is issued a key pair by a public key cryptography system.
The basic principles and functions of each key in the key pair are summarized in the following illustration:
Figure A-1 Basic Key Pair Description
A.3.1 Key Pairs and Authentication
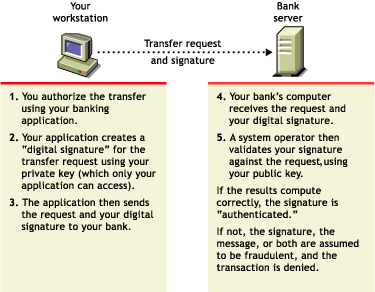
Authentication means that the data receiver knows that the data sender is exactly who or what it claims to be.
Suppose that you want to authorize your bank to transfer funds from your account to another account. The bank needs proof that the message came from you and that it has not been altered during transit. The following illustrates the process that your online transaction would follow, using public key cryptography.
Figure A-2 Public Key Process
For information about digital signatures and their verification, see Digital Signatures.
A.3.2 Key Pairs and Encryption
Encryption means that the data can be read only by the intended receiver.
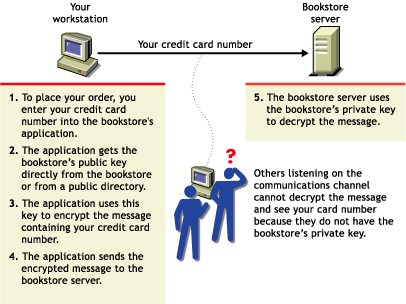
Suppose you want to order a book from an Internet vendor and you need to use your credit card to pay for it. You don't want your credit card number read by anyone other than the intended recipient.
The encryption process in the following illustration provides the mechanisms through which your credit card number can be safely transmitted.
Figure A-3 Encryption Process