4.3 Configuring LDAP Plus NCSS Authentication
The NetIQ Cloud Manager administrator can choose to authenticate tenant customers through a supported NetIQ Cloud Security Service (NCSS) server that redirects the customers back to their own LDAP source for authentication credentials.
With this authentication option, Cloud Manager users of various roles store their credentials in the LDAP directory that you specify during configuration. For example, if you are a cloud service provider, you can set up your own enterprise LDAP structure for logging in to Cloud Manager, but your customers can use their own LDAP structures–preconfigured within NCSS–to authenticate to Cloud Manager.
This section helps you to prepare the information you need to configure LDAP plus NCSS for Cloud Manager authentication.
If you want to use another authentication service, see Section 4.1, Configuring Authentication to an LDAP Directory, Section 4.3, Configuring LDAP Plus NCSS Authentication, or Section 4.4, Configuring Authentication to Novell Access Manager.
If you want to learn more about NetIQ Cloud Security Service, see the NetIQ Cloud Security Service 1.5 documentation Web site.
4.3.1 LDAP Plus NCSS Authentication Concepts
The following diagram illustrates the process of LDAP plus NCSS authentication from the perspective of the customer or “tenant” on the Cloud Manager Service Provider after you provide the required configuration information.
Figure 4-1 LDAP Plus NCSS Authentication
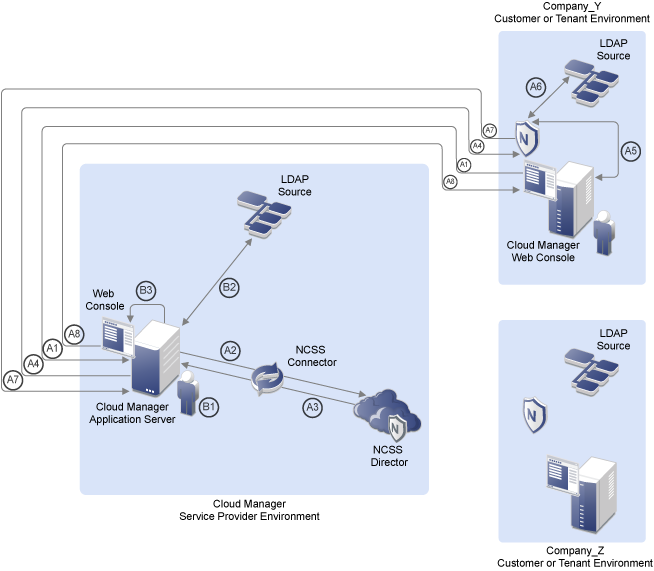
Customer or “Tenant” Authentication
Stage A1: Customer Steve at Company_Y has bought tenant rights in Jim’s Cloud Manager Service Provider environment. Steve opens a Web browser and loads the URL to the Cloud Manager Application Console. Steve’s Web browser opens the Cloud Manager Web portal, which connects to the Cloud Manager Application Server.
Stages A2, A3: The Application Server uses a preconfigured NCSS connector to communicate to the NCSS Director. The NCSS Director recognizes the login request and redirects that request back to the Cloud Manager Application Server.
Stage A4: The Application Server sends login requirements to NCSS components that were previously installed in the Company_Y environment and directs the Application Console to display open login fields.
Stage A5: NCSS components at Company_Y recognize that an LDAP login is required and establish a link to the Company_Y LDAP source. Steve at Company_Y sees the login field waiting for input on the Cloud Manager Application Console. He enters his username and password.
Stages A6, A7: NCSS components at Company_Y check the customer’s LDAP source to validate Steve’s login credentials. The NCSS components send the tested credentials back to the Cloud Manager Server, which validates them through the NCSS Director.
Stage A8: The Cloud Manager Server recognizes the privileges that Steve has, based on the context of the email address information listed in his LDAP Source. The Cloud Manager Server opens the relevant Web page for Steve in its Application Console.
Service Provider Administrator Authentication
Stage B1: Service Provider Jim is the Cloud Manager administrator. He wants to use NetIQ Cloud Manager to provide business services to his customers, including Steve at Company_Y, so he opens a Web browser and loads a special URL provided to him by the Cloud Manager Application Server.
Stage B2: Jim’s Web browser opens the Cloud Manager Application Console, which is directly connected to the Cloud Manager Server. The Cloud Manager server recognizes the special URL as a Cloud Manager administrator login request, so it establishes a connection to Jim’s LDAP source and directs its Application Console to display open login fields for a potential Cloud Manager Administrator.
Stage B3: Jim sees the login field waiting for input on the Cloud Manager Application Console, so he enters his username and password.
The Cloud Manager Server also recognizes the privileges that Jim has, based on the context of the email address information listed in his LDAP Source. The Cloud Manager Server opens the relevant Web page for Jim in its Application Console.
4.3.2 Configuring LDAP plus NCSS Authentication
-
Make sure you know the information you’ll be prompted to provide during the LDAP plus NCSS authentication configuration:
Information Needed to Configure Authentication
Description
NCSS Director Configuration
DNS Address of the NCSS Director service
Specify the DNS name of the server that hosts the NCSS Director service. This address should match the address on the SSL certificate that was issued for the server.
Path to the SSL Certificate of the NCSS Director server
Specify the path in the file system where the SSL certificate resides. This certificate must be in DER format.
If no SSL certificate exists, you can create one by visiting the NCSS Web page in your browser. You can use your browser tools to export the certificate. Remember that it must be in DER format.
LDAP Configuration
Do you want to use SSL with LDAP?
If you respond with “yes” to this question, you are asked for an SSL certificate later in the configuration.
LDAP Source
You need to select the LDAP source for use with Cloud Manager, either Novell eDirectory or Microsoft Active Directory.
LDAP host address
This is the address (DNS name or IP address) of the LDAP host that Cloud Manager can connect to for authentication.
If you chose to use SSL with LDAP, this address should match the subject of the certificate issued for the LDAP host.
The configuration tool immediately validates this address when you specify it.
LDAP port
Designate the port where you want the LDAP server to listen for communication from Cloud Manager.
If you are using SSL, the default port is 636. If you chose not to use SSL, the default port is 389.
Path to SSL certificate on LDAP server
This is the file system path to the SSL certificate you previously copied to the LDAP server. The certificate must be in DER format.
LDAP read-only user DN
Specify the distinguished name (DN) of an existing LDAP read-only user who has read access to the LDAP directory.
LDAP read-only user’s password
Specify the password for the LDAP read-only user.
When you specify the user password, the configuration tool immediately attempts an SSL authentication to validate the existence of this user and password.
Cloud Manager LDAP user DN
Specify the DN of an existing LDAP user whom you want to designate as the Cloud Manager administrator.
When you specify this LDAP user, the configuration tool immediately attempts to locate the user in LDAP, then asks you to verify that this is the user you want to designate as the Cloud Manager administrator.
Make sure that the mail attribute is set for this user in LDAP.
LDAP DN of NCM Users
Specify the DN of the LDAP container where the users whom you want to log in to Cloud Manager already exist.
This is the parent context of users that will be allowed to log in to the Cloud Manager Application Console. All subdirectories and users are included by default.
Make sure that all users, regardless of their context in this container, have an email domain configured prior to logging into the Application Console.
NOTE:You can use the Cloud Manager Application Console later to import users who do not currently exist in this DN.
As you continue running the configuration tool (/opt/netiq/cloudmanager/configurator/config) following the configuration of the Postgres database, the tool displays the following text:
Authentication Type 1) LDAP 2) NCSS 3) LDAP plus NCSS 4) NAM Selection:
-
Specify 3 (LDAP plus NCSS) as the Authentication Type you want to configure.
-
Follow the prompts and use the information you gathered in Step 1 to complete this segment of the configuration.
After the LDAP plus NCSS authentication configuration, continue with Section 5.0, Installing and Configuring Other Cloud Manager Feature Settings.