5.3 Configuring the Time-Based One-Time Password (TOTP) Tool for Two-Factor Authentication Using Google Authenticator
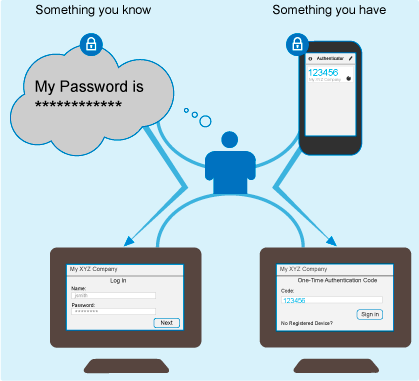
The Time-Based One-Time Password (TOTP) tool in CloudAccess supports the use of one-time passwords (OTPs) for two-factor authentication of users as they access applications through CloudAccess. With two-factor authentication, users must provide two categories of authentication factors before they can access the applications. The authentication factors used by the TOTP tool are:
-
Something the user knows: The first authentication factor requires something the user knows, such as the password for the user’s single-sign-on user name.
-
Something the user has: The second authentication factor requires something the user has, such as a mobile device running Google Authenticator to generate time-based one-time passwords.
Google Authenticator is a free software-token app that users deploy on their mobile devices. Authenticator generates time-based OTPs for authentication, without requiring an Internet connection or cellular service.
If users construct strong passwords and protect them, one-factor authentication can be an effective measure against security breaches. Two-factor authentication provides an additional layer of security to help ensure the identity of a user and reduce the risk of unauthorized access to your applications and data. Users still enjoy the convenience of single sign-on, but the access is more secure.
Figure 5-1 The Two-Factor Authentication Solution for CloudAccess
The following sections describe how to set up and use TOTP for CloudAccess:
5.3.1 Understanding One-Time Passwords
The one-time password secret keys, code generation, and code verification are based on the industry standard HMAC-SHA1 token algorithm that is defined in the IETF RFC 6238. Each OTP is intended for use by only one user, is valid for a specific period of time, and becomes invalid after the user successfully logs in. It cannot be easily duplicated and reused elsewhere. The entered code is sent securely to CloudAccess through HTTPS (Secure HTTP) encryption on TCP port 443.
With time-based OTP, the TOTP validation server and software-token app use their respective system times to generate OTPs. The TOTP algorithm assumes that the system times are synchronized. To minimize time drift, you should configure the network time protocol (NTP) on the CloudAccess appliance so its clock stays accurate. If you cluster the CloudAccess appliances, ensure that the member nodes in the cluster point to the same centrally located time server. Users should synchronize the clocks on their mobile devices with their service providers’ networks, which are typically aligned with atomic clocks.
Time differences between the TOTP validation server and a mobile device can result in a mismatch of the OTP, and subsequent login failure. Common causes include clock time drift, network latency, and slow data entry. To allow for time differences, the Validity Time setting allows a submitted OTP to be considered valid if it matches a server-generated OTP for any time-step that occurs in a specified validity window centered on its received timestamp, plus 30 seconds. A time-step is 30-seconds.
For the TOTP tool, the default validity time setting is 5 minutes. The validity window is 2.5 minutes before and 2.5 minutes after the password’s received timestamp, plus 30 seconds. You can specify integer values from 2 to 10. Shorter validity times are considered to be more secure than longer ones.
If you enable both the Google ReCAPTCHA tool and the TOTP tool in CloudAccess, ReCAPTCHA works only for the user’s login password, and not for the one-time password. The ReCAPTCHA is not used if the OTP is incorrect.
5.3.2 How to Use Google Authenticator for TOTP
You can enable the TOTP validation service for one or more applications. At a user’s next login, TOTP prompts the user to register a device to use for the additional authentication. If you enable all applications, the prompt occurs immediately after CloudAccess validates the user’s credentials. Otherwise, the prompt occurs when the user first selects any one of the TOTP-enabled applications.
Figure 5-2 illustrates the setup for Google Authenticator on a users mobile device and the registration of the device with TOTP in CloudAccess.
Figure 5-2 Self-Service Device Registration
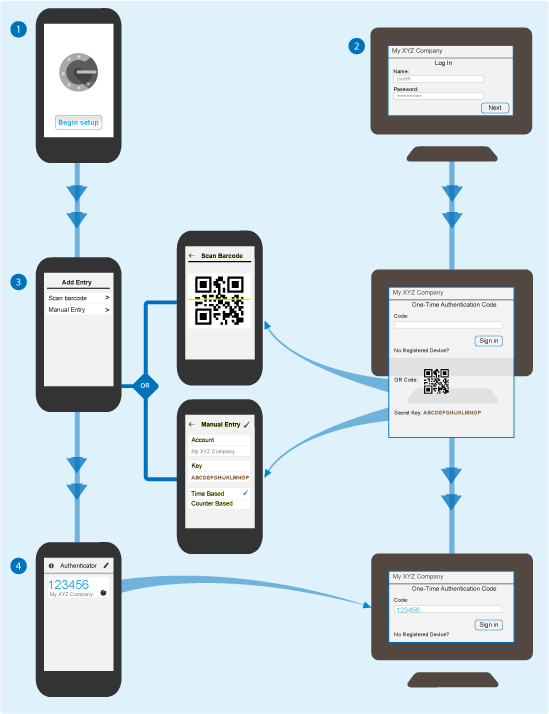
The user registers a device with CloudAccess as follows:
-
The user installs the Google Authenticator app on their mobile device.
-
On a computer, the user logs in to CloudAccess using their corporate user name and password. If the credentials are valid, CloudAccess prompts the user to register a device for one-time passwords.
-
The user registers the mobile device with their CloudAccess account.
-
TOTP creates a secret key for the user and displays it in text and Quick Response (QR) code format in the computer web browser.
-
On the mobile device, the user starts Google Authenticator and adds an account for CloudAccess.
-
In Google Authenticator, the user scans the Quick Response (QR) code displayed on the browser, or manually enters the security key.
-
-
The Google Authenticator app generates a 6-digit code, and the user enters the code on the Authentication Code page.
The device registration process is not complete until the user submits a one-time authentication code that was generated using the secret key on the registration page, and the server validates it. If the submitted code does not validate, TOTP re-displays the registration page with the current secret key. The user can generate a new code on the mobile device, and then try again to authenticate. On successful authentication, TOTP stores the shared key with the user’s identity information in the related identity source. The user’s registered device and its authentication codes apply to all TOTP-enabled applications. Each session requires only a single successful authentication.
TOTP cancels the registration process if the user makes no attempt to register the device and discontinues the login by closing the tab or browser. The next time that the user logs in, CloudAccess generates a new secret key, and prompts the user to register a device with a new key.
For each log in to CloudAccess, the user runs the Google Authenticator app to generate a new 6-digit code for the CloudAccess account. When the app runs, it generates a new 6-digit authentication code every 30 seconds. This code is the one-time password that the user enters for two-factor authentication.
TOTP requires a newly generated authentication code at each subsequent login. If you enable all applications, TOTP prompts for the code immediately after CloudAccess verifies the user’s credentials. Otherwise, the prompt occurs when the user first selects any one of the TOTP-enabled applications. The authentication automatically applies to other TOTP-enabled applications for that session.
An administrator can reset a device associated with a user account. This deregisters the device from the account, and invalidates the old key. The next time that the user logs in, CloudAccess generates a new secret key, and prompts the user to register a device with a new key.
5.3.3 Configuring the TOTP Tool
You can enable the Time-Based One-Time Password tool to require users to use two-factor authentication when logging in through CloudAccess.
To configure the TOTP service:
-
Log in with an appliance administrator account to the Admin page at https://appliance_dns_name/appliance/index.html.
-
Drag the TOTP Tool icon from the Tools palette to the Tools panel.

-
Click the TOTP icon on the Tools panel, then click Configure.
-
(Optional) Specify the Validity Time.
Specify an integer value from 2 to 10. The default value is 5. Shorter validity times are considered more secure.
-
Click the Applications tab, then select the check box next to one or more applications to enable them for TOTP.
By default, no applications are enabled for TOTP.
When a user registers an authentication device, the device and authentication codes apply to all TOTP-enabled applications.
-
Click OK to save the setting and enable the TOTP tool.
-
Click Apply to activate the TOTP configuration.
-
Wait while the service is activated across all nodes in the cluster. Do not attempt other configuration actions until the activation completes successfully.
In the Appliances pane, a green gear icon spins on top of each node until the activation is complete across all nodes in the cluster.
5.3.4 Registering a Mobile Device with the TOTP Tool for OTP Generation
After you enable the TOTP tool, users are prompted to register a device to use for the additional verification the next time they sign in to CloudAccess. Each user must register a mobile device for generating the user’s one-time passwords. For the initial setup, the user should use a web browser on a computer other than the mobile device where the one-time passwords will be generated.
The One-Time Authentication code page displays a QR code and its equivalent secret key. The user deploys the Google Authenticator app on a mobile device, and sets up an account for CloudAccess by using the shared key. The user can scan the QR code or manually enter the key. When the app runs, it generates a new one-time password every 30 seconds.
Before registering a device, the following setup is required:
-
The user must be an authorized user of CloudAccess with a valid user name and password.
-
The user must have access to a computer running a supported web browser.
For a list of supported web browsers, see Browsers in Table 2-2, Product Requirements.
-
The user must use a supported mobile device.
For a list of supported mobile device platforms, see Mobile Devices in Table 2-2, Product Requirements.
-
The user must install the Google Authenticator app on the mobile device.
To register a mobile device for use with the TOTP tool:
-
(Conditional) If the Google Authenticator mobile app is not already installed on the mobile device, download and install it.
-
Visit the app store for your mobile device.
-
Search for Google Authenticator.
-
Download and install the app.
-
-
From a computer that will not be used as the OTP device, access CloudAccess either directly or through a SAML2 redirect.
-
On the CloudAccess login page, enter your network user name and password (your normal identity source login credentials).
A message displays a QR code (and its equivalent secret key) to use for the TOTP registration.
If you are not prepared to register your mobile device at this time, you can cancel the registration process by closing the tab or your browser. On your next login, CloudAccess generates a new secret key, and prompts you to register a device with a new key.
-
On your mobile device, use the Google Authenticator app to scan the displayed QR code, and register the device with CloudAccess. You can alternatively type the secret key.
-
On your mobile device, open the Google Authenticator app.
-
Select Settings > Add an account.
-
Use either of the following methods to configure the account:
-
Scan a barcode:
-
Select Scan a barcode.
-
Use your device’s camera to scan the QR code that appears on the CloudAccess One-Time Authentication Code page.
-
-
Enter provided key:
-
Select Time Based.
-
Select Enter provided key.
-
Type the 16-character secret key that appears on the CloudAccess One-Time Authentication Code page. The key is case sensitive. Do not add spaces or stray characters.
-
-
-
Specify a unique name for the account.
-
Tap Done.
-
-
On the mobile device, view the 6-character code that Google Authenticator displays for CloudAccess. This is your OTP.
-
On the computer on the One-Time Authentication Code page, type the OTP, then click Sign In.
CloudAccess confirms that the mobile device is registered, and the login is successful.
If the code does not validate, the registration page is redisplayed with the current secret key. You can generate a new code, and try again. The code might not validate if you enter an expired code, you do not enter a code, you mistype the code, or you make an error when setting up the secret key for the account in Google Authenticator.
-
To log in to your account from the mobile device, log in to CloudAccess as described in Section 5.3.5, Using Two-Factor Authentication at Login.
On successful authentication, you can access the apps icons for the authorized services and resources associated with your user identity. Access is granted only for the duration of that session.
To de-register a mobile device:
-
Access CloudAccess either directly or through a SAML2 redirect.
-
Log in and authenticate as described in Section 5.3.5, Using Two-Factor Authentication at Login.
-
Click the My Devices icon.
-
In the Registered Devices list, select the mobile device.
-
Click the Delete icon for the device.
-
In the Unregister Device window, click OK to confirm.
At your next login, CloudAccess prompts you to register a device before you can access applications that require two-factor authentication.
5.3.5 Using Two-Factor Authentication at Login
When two-factor authentication is enabled for CloudAccess, a user must provide login credentials and a one-time authentication code to gain access to TOTP-enabled applications. The code is a 6-digit number generated for CloudAccess by the Google Authenticator app that is running on the user’s mobile device. The user must have already registered the mobile device with CloudAccess, as described in Section 5.3.4, Registering a Mobile Device with the TOTP Tool for OTP Generation.
The user should enter the newly generated code as soon as possible after it appears in the Google Authenticator app. Each OTP is intended for use by only one user, is valid for 30 seconds, and becomes invalid after the user successfully logs in. Access is granted only for the duration of that session.
To log in to CloudAccess using two-factor authentication:
-
Access CloudAccess either directly or through a SAML2 redirect.
-
On the login page, enter your network user name and password (your normal identity source login credentials).
CloudAccess verifies the credentials against a defined identity source. If all applications require two-factor authentication, the One-Time Authentication Code page appears and prompts you to enter the code. Otherwise, CloudAccess displays the page when you first click any one of the applications that require it.
-
Use Google Authenticator to generate a new one-time password, and enter the code on the CloudAccess One-Time Authentication Code page.
If you enter the password incorrectly, you can try again with the same password until it times out. Google Authenticator generates a new OTP every 30 seconds.
On successful authentication, you can access the apps icons for the authorized services and resources associated with your user identity. Each session requires only a single successful authentication.
5.3.6 Resetting a Device (Deregistering a Device)
Each user can register a single device to use for generating one-time passwords. Resetting a device for a user’s account deregisters the user’s current device. The next time the user logs in, the TOTP tool creates a new secret key for the account.
An administrator can reset a device for a user account:
-
To allow the user to register a different device
-
To revoke access for a registered device that is lost or stolen
Information about a user’s registered device and secret key is part of the user’s identity information in the identity source. This information is deleted automatically if a user’s identity object is permanently deleted from the identity source. The information is stored with the user’s object if the user’s identity object is disabled.
If the Time-Based One-Time Password tool is disabled, CloudAccess no longer prompts the users for an OTP at login. However, information about a user’s registered device and secrete key continue to be stored in the users’ identity objects in the identity source. The OTPs generated for the user’s CloudAccess account by the Google Authenticator app are no longer needed at login.
After a device is deregistered, the OTPs generated for the user’s CloudAccess account by the Google Authenticator app are no longer valid. At the user’s next login, the TOTP tool generates a new secret key for the user, and the user must register a device to work with it.
To reset (deregister) a device for a user account as an administrator user:
-
Log in with an appliance administrator account to the CloudAccess Administration Console at https://appliance_dns_name/appliance/index.html.
-
Click the Devices icon.
-
In the User field, type a few characters of the user name, and then scroll in the window to select the user identity.
-
Under One-Time Password, click Reset.