6.10 Understanding Azure Active Directory for Change Guardian
Azure Active Directory (Azure AD) is Microsoft’s cloud based directory and identity management service. Change Guardian allows you to monitor Azure AD along with on-premises Active Directory. Change Guardian can monitor Azure AD users and groups. You can use the Azure AD feature to improve employee productivity, streamline IT processes, improve security, and cut costs. For more information about Azure AD, see Azure AD documentation.
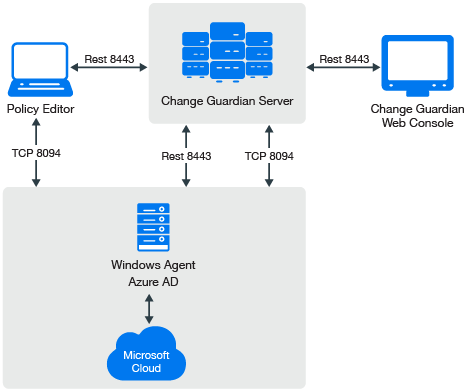
Change Guardian connects with Azure Active Directory using the Microsoft Azure AD Reporting API. It supports a single tenant.
NOTE:The Azure AD agent is supported on Windows platforms. Change Guardian supports the user and group event types.
6.10.1 Planning Azure AD Monitoring Using Change Guardian
The following table provides an overview of the tasks required for Change Guardian to start monitoring Azure AD audit events:
|
Task |
See... |
|---|---|
|
Ensure that you have created a tenant and its credentials are available for Change Guardian. Required credential details:
|
|
|
Assign the license key for Azure AD module manually. |
|
|
Create the Azure AD web application. |
|
|
Configure the Microsoft Azure tenant. |
|
|
Create policies for users and groups. |
|
|
Assign policies and view events on the Change Guardian web console. |
|
|
(Conditional) Configure the default Windows registry keys, if you want to modify the default keys based on your requirements. |
|
|
(Conditional) During upgrade, ensure that you reconfigure the Windows agent to enable Azure AD monitoring. |
Reconfigure Windows Agent to Monitor Azure AD Using Agent Manager |
|
Triage events. |
You can triage events in the Change Guardian web console and click the Change Guardian shield to get more information about the events. |
The Azure AD monitoring capability in Change Guardian is built in conjunction with Microsoft Inc's Azure AD reporting API. You must understand the technical limitations of the reporting APIs that are captured in Azure Active Directory reporting latencies documentation.
Change Guardian supports real-time monitoring. But, due to latency limitation from Microsoft Azure, Change Guardian is experiencing delay in fetching audit logs. This limitation can be overcome when Microsoft fixes this latency issue.
IMPORTANT:NetIQ supports monitoring on the Microsoft Azure public cloud. For more information, see Azure FAQs.
The following illustration explains the work flow of various components namely: the Change Guardian server, agents, clients, Policy Editor and Microsoft Azure Active Directory.
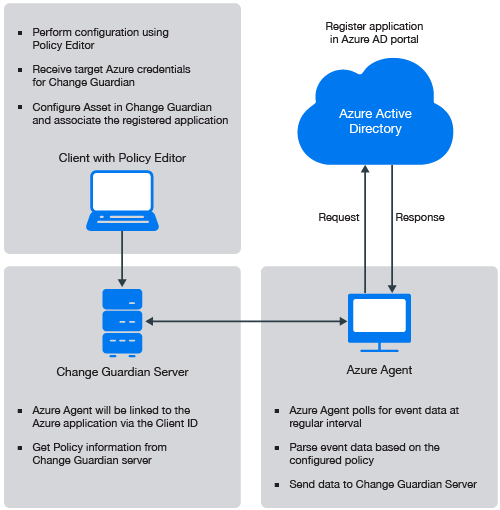
6.10.2 Configuring Azure AD Tenant
In Azure Active Directory (Azure AD), a tenant is a representative of an organization. You have to configure a tenant and its credentials such as Domain Name, Client secret key, and Client ID and make it available for Change Guardian.
Complete the following steps to configure the Azure AD tenant for monitoring, using the Policy Editor:
-
Select Azure Active Directory from the left panel of the Policy Editor.
-
From the tree, navigate to Azure Tenant Configuration.
-
In the Azure Tenant Configuration window, specify values for the following fields:
-
Domain Name: Specify the name of the Azure Active Directory domain.
-
Client ID: Enter the Client ID that was displayed in the Azure portal during configuration.
-
Client Secret Key: Enter the Client secret key that was displayed in the Azure portal during configuration.
-
Comment: (Optional) Enter a comment.
-
-
Click Save.
-
(Conditional) If you want to modify any particular configuration, you need to make the modifications in the Azure Tenant Configuration window.
6.10.3 Creating a Policy for Azure AD Groups
Complete the following steps to create the Azure Active Directory policy using the Policy Editor:
-
In the left pane of the Policy Editor window, select Azure Active Directory > Azure Active directory Policies.
-
Expand the Azure Active directory Policies and select Groups.
-
On the Groups Policy window, specify the appropriate information.
NOTE:Specifying the specific group event type from the event list is mandatory.
-
Click Submit.
6.10.4 Creating a Policy For Azure AD User Accounts
Complete the following steps to create the Azure Active Directory policy using Policy Editor:
-
In the left pane of the Policy Editor window, select Azure Active Directory > Azure Active directory Policies.
-
Expand the Azure Active directory Policies and select User Accounts.
-
Click Create Policy.
-
On the User Account Policy window, specify the appropriate information.
NOTE:Specifying the specific user event type from the event list is mandatory.
-
Click Submit.
6.10.5 Assigning a Policy to an Asset
Complete the following steps to assign a policy:
-
In the left pane of the Policy Editor window, navigate to NetIQ Change Guardian.
-
Click Policy Assignment.
-
Select an Azure asset group or computer, and click Assign Policies.
-
Select Assets from the drop-down list.
NOTE:You cannot assign Azure AD policies via Asset Groups.
-
Select a policy set or policy and click Apply.
6.10.6 Configuring Default Windows Registry Keys
By default, Change Guardian has defined the default values for the Windows registry keys. If you want to modify the registry key values, perform the following procedures:
Configuring Azure AD Event Fetching Interval
By default, Change Guardian sets the time interval to 120 minutes behind the current system time as the start time to fetch the events due to latency issues from Microsoft Azure AD Reporting API. Change Guardian does deduplication of events internally to avoid any duplicate events while processing the events once Change Guardian receives the events from Azure AD. For more information, see Azure Active Directory reporting latencies.
If you observe a different latency time in your environment, you can change this value to the observed value. Complete the following steps to modify the time interval:
-
In Windows registry settings, navigate to the Change Guardian Agent installation directory:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\NetIQ\ChangeGuardianAgent
-
Right click the AzureADEventFetchInterval key.
-
Select Decimal under Base.
-
(Conditional) If you notice a higher latency value in your environment, you can configure this value based on your observed value. The value range is between 120 minutes to 1440 minutes (24 hours) for the Value data field.
NOTE:If you configure this value to above 1440 minutes, it will reset it to 1440 minutes by default, since that is the maximum value. If the latency from Microsoft is more than this value, you might face a data loss.
-
Click OK.
-
Go to Services > NetIQ Change Guardian Agent.
-
Select the Change Guardian Windows Agent application, then click Restart.
Configuring Azure AD Access Token Refresh Time Interval
By default, every 30 minutes, Change Guardian refreshes the access token which is used for connecting to Azure active directory. The maximum limit is 50 minutes. If you configure this value to below 15 minutes, the system will reset it to 15 minutes automatically. If you configure this value to above 50 minutes, the system will reset it to 50 minutes automatically.
If you want to modify this time interval based on your requirement, complete the following steps:
-
In Windows registry settings, navigate to the Change Guardian Agent installation directory:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\NetIQ\ChangeGuardianAgent
-
Right click the AzureADTokenRefreshInterval key.
-
Select Decimal under Base.
-
Specify the time interval to any required value range between 15 minutes to 50 minutes in the Value data field.
-
Click OK.
-
Go to Services > NetIQ Change Guardian Agent.
-
Select the Change Guardian Windows Agent application, then click Restart.
Configuring Azure AD Event Collection Interval
By default, Change Guardian fetches the events every 10 minutes from Azure Active Directory. NetIQ recommends the periodicity to be 10 minutes.
The default minimum value is 5 minutes and the maximum value is 30 minutes. If you configure this value to below 5 minutes, the system will reset it to 5 minutes automatically. If you configure this value to above 30 minutes, the system will reset it to 30 minutes automatically.
If you want to modify this time interval based on your requirement, complete the following steps:
-
In Windows registry settings, navigate to the Change Guardian Agent installation directory:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\NetIQ\ChangeGuardianAgent
-
Right click the AzureADEventCollectionInterval key.
-
Select Decimal under Base.
-
Specify the time interval to any required value range between 5 minutes to 30 minutes in the Value data field.
-
Click OK.
-
Go to Services > NetIQ Change Guardian Agent.
-
Select the Change Guardian Windows Agent application, then click Restart.
6.10.7 Reconfigure Windows Agent to Monitor Azure AD Using Agent Manager
During new installation of Change Guardian 5.0 or upgrade from Change Guardian 4.2 or later to Change Guardian 5.0 if you want to monitor Azure AD, you must deploy Windows agent 5.0 version and enable Azure AD monitoring using the Change Guardian Agent Manager.
Perform the following steps to deploy and reconfigure Windows agent to enable Azure AD monitoring:
-
From Change Guardian main, click Integration > Agent Manager.
-
Do one of the following:
-
(Conditional) If you have not previously added assets, in Agent Manager, under Asset Groups, click All Assets and then click Add Assets.
-
(Conditional) If you previously added assets, in Agent Manager, click All Assets > Manage Assets, and then click Add.
-
-
From the assets list, select the computer where you want to deploy an agent. You can select multiple computers if Agent Manager can use the same credentials to connect to the computers.
-
Provide credentials for an account that can connect to the computer and click Next.
The account must be the local administrator account or a domain account in the Local Administrators group.
-
Click Manage Installation, and then select Reconfigure.
-
Perform the following steps:
-
For the agent version, select Change Guardian Agent for Windows Agent Version, where Agent Version is the version of the Windows agent you want to deploy.
-
For the agent configuration, click add a new configuration using the Add option. Fill in all the details.
-
For Enable Azure AD Monitoring option, select Yes to specify that you want to reconfigure the Windows agent to enable Azure AD monitoring.
-
Click Start Reconfiguration.
-
6.10.8 Troubleshooting
This section contains some of the issues that might occur when you want to monitor Azure AD using Change Guardian, along with the actions to work around the issues.
Receiving an Invalid Token
Issue: Change Guardian is unable to receive events because of the Incorrect Domain Name, Client secret key, or Client ID.
Workaround: Obtain the correct Domain Name, Client secret key, or Client ID from the Microsoft Azure AD portal.
NOTE:Severity of the Invalid token event varies based on the severity of the first policy that was assigned. If the policy assigned is of the automatic severity, the severity of Invalid token event will be set to 4.
Change Guardian Is Unable to Receive Azure AD Events
Issue: Change Guardian is unable to receive events because of the following:
-
Incorrect Domain Name, Client secret key or Client ID.
-
Tenant is not reachable
-
Invalid remote web application
Workaround:
-
Obtain the correct Domain Name, Client secret key or Client ID from the Microsoft Azure AD portal.
-
Enter a valid tenant name in the tenant configuration page.
-
Check if the tenant is accessible from the Change Guardian Agent computer.