3.2 Configuring the Optional Settings
The following table describes the optional settings that you can configure for Mac OS Client:
|
Setting |
Description |
|---|---|
|
disable_1N: true |
To disable the automatic detection of username for Card and PKI methods. For more information, see Disabling 1:N. |
|
tenant_name |
To use Multitenancy, you must point Mac OS Client to a specific tenant. For more information, see Configuration Settings for Multitenancy. |
|
logo_path: <custom_logo_path> |
To customize a logo for Mac OS Client. For more information, see Customizing a Logo. |
|
card.timeout: X |
To change a default Card waiting time-out duration. For more information, see Configuring Time-Out for Card Waiting. |
|
u2f.timeout: X |
To configure the time-out duration for authentication with the U2F token. For more information see, Configuring Time-Out for the U2F Authentication. |
|
event_name: <CustomEventName> |
If you want to use both domain-joined and non-domain machines, you can use a custom event for the specific machines. For more information, see Selecting an Event. |
|
verifyServerCertificate: true |
To configure the verification of server certificates for LDAP connection. For more information, see Configuring to Verify Server Certificates. |
|
authentication_agent_enabled: true |
To enable the Authentication Agent chain in Mac OS X Client. For more information, see Enabling the Authentication Agent Chain. |
|
forceCachedLogon: true |
To enforce the cached login for unlocking the Client. For more information, see Configuring the Enforced Cached Logon. |
|
keep_window_on_unlock: false |
To display the authentication window on the Mac OS Client unlock screen, see Displaying the Authentication Window on Unlock Screen. |
|
enableLinkedChainsOffline:false |
To disable linked chains for offline login. For more information, see Disabling Linked Chains for Offline Login. |
|
rest_profiling: true |
To enable the profiling tool that helps in analyzing the performance and CPU utilization of different programs. For more information, see Enabling the Profiling Tool. |
|
locale: xx |
To change the client locale to a language other than the operating system’s default language. For more information, see Changing the Locale of Mac OS Client without Changing the Locale of the Operating System. |
|
tlsVersion: value |
To configure the TLS version that the network library of the Mac OS Client uses for establishing HTTPS connection with the Advanced Authentication server. For more information, see Configuring the TLS Version. |
NOTE:A separator between the setting and its value can be either equal (=) or colon (:).
Following are the other optional settings:
-
To bind Mac to an Active Directory, see
Binding Mac to Active Directory
. -
To force offline login manually for users, see
Enabling the Offline Mode
. -
To display the user on the login screen in the non-domain mode, see
Displaying Other User on the Login Screen in Non-Domain Mode
. -
To create a mobile account, see “Creating a Mobile Account for the Offline Mode”.
-
To localize the Advanced Authentication resources for your language with the instructions, see Localizing the Messages for Clients.
3.2.1 Disabling 1:N
You can disable the 1:N feature that allows you to detect the user name automatically while authenticating with the Card and PKI methods.
For example, Bob can place the card on the reader to log in to Mac system and authenticate with the Card method automatically without specifying his user name.
To disable the 1:N feature, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Add the parameter disable_1N: true in the file.
-
Save the changes.
-
Restart the operating system.
3.2.2 Configuration Settings for Multitenancy
If the Multi-tenancy option is enabled, you must add the parameter tenant_name with a tenant name in the aucore_login.conf file.
To configure a specific tenant name, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the configuration file does not exist, create a new file.
-
Specify tenant_name: <name of tenant>
For example, tenant_name: TOP for the TOP tenant.
-
Save the changes.
-
Restart the operating system.
NOTE:If you do not add the parameter tenant_name, an error message Tenant not found might be displayed.
3.2.3 Customizing a Logo
You can customize the logo of Mac OS Client according to your requirement. The format of the logo must meet the following requirements:
-
Image format: png, jpg, gif
-
Resolution: 400x400px
-
Maximum file size: 100Kb
To customize the logo, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify the path of the folder where the image file is stored, in the following format:
logo_path: /Users/<username>/<path_of_the_file>/<file_name>.png
-
Save the changes.
-
Restart the operating system.
3.2.4 Configuring Time-Out for Card Waiting
You can configure the duration for which the card waiting dialog is displayed when the user authenticates using the card method. If the user does not present the card for the specified time-out period, the Hardware timeout message is displayed and the card waiting dialog is closed. Then, the user login selection screen is displayed.
By default, the card timeout is 60 seconds.
To configure time-out for card waiting, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify card.timeout: X. X is the timeout value in seconds.
-
Save the changes.
-
Restart the operating system.
3.2.5 Configuring Time-Out for the U2F Authentication
You can configure the duration after which the authentication fails if the user does not touch U2F token for authentication. The default timeout is 60 seconds.
To configure the timeout for U2F authentication, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify u2f.timeout: X in the file. X is the timeout value in seconds.
-
Save the changes.
-
Restart the operating system.
3.2.6 Selecting an Event
By default, Mac OS X Client uses the Mac OS logon event for authentication. However, in some scenarios you must create a separate custom event.
For example, when the predefined event is used for domain joined workstations, you can create a custom event with type Generic for the non-domain joined workstations.
To configure custom event for Mac OS X Client, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify event_name: <CustomEventName>
-
Save the changes.
-
Restart the operating system.
3.2.7 Configuring to Verify Server Certificates
You can secure connection between Mac OS X Client and Advanced Authentication servers with a valid self-signed SSL certificate. This prevents any attacks on the connection and ensures safe authentication.
To enable verification of the server certificates, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/open aucore_login.conf.
If the file does not exist, create a new file.
-
Specify verifyServerCertificate=true (default value is false).
-
Save the changes.
-
Place the server certificate in the Keychain Access.
NOTE:Ensure that the server certificate is in the.p12 format.
You must upload the SSL certificate in the Administration portal > Server Options. The SSL certificate provides high level of encryption, security, and trust. For more information about how to upload the SSL certificate, see Uploading the SSL Certificate.
3.2.8 Enabling the Authentication Agent Chain
NOTE:The authentication_agent_enabled parameter is valid for Advanced Authentication 6.3 SP4 and prior versions. This parameter is not required from Advanced Authentication 6.3 SP5.
You can enable the Authentication Agent chain in the Mac OS X Client to allow users to authenticate with the Authentication Agent on a Windows system. This helps users to get authorized access to the Mac OS X Client that does not support the external devices. To perform such authentication, users must select the Authentication Agent chain from the Chains list of Mac OS X Client to initiate the authentication process on the Windows system, where the Authentication Agent is installed.
To enable the Authentication Agent chain on the Mac OS X Client, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify authentication_agent_enabled:true.
-
Save the changes.
-
Restart the operating system.
3.2.9 Configuring the Enforced Cached Logon
When the network connection is slow or unstable, the client login or unlock process can take several minutes. A solution to this is to enforce the cached login. The Client connects to the Advanced Authentication server to validate the credentials in the background after the cached login. By default, the enforced cached login is disabled and the Client always connects to the Advanced Authentication server to validate the credentials.
To enforce cached login for Mac OS X Client, perform the following steps:
-
Open the configuration file \Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify forceCachedLogon: true (default value is false).
-
Save the changes.
-
Restart the operating system.
3.2.10 Binding Mac to Active Directory
You can bind a Mac to Active Directory to enable the Mac system to access user accounts in the Active Directory domain. Domain users can use credentials stored in the Active Directory to get authorized access to Mac system. Perform the following steps to bind Mac to Active Directory:
-
Click Apple icon in the upper-left corner.
-
Click System Preferences > Network.
-
Click Advanced > DNS.
-
Double click an existing record to edit it or click + in DNS Servers section.
-
Specify the IP address of your DNS server.
For example, 192.168.0.200.
-
Click + in the Search Domains section.
-
Specify the FQDN of your domain.
For example, company.com.
-
Click OK.
-
Click Apply in the Network window.
-
Click System Preferences > Users & Groups.
-
Click Login Options in the left pane.
-
Click the lock icon in lower-left of the screen to unlock and edit the settings.
-
Specify Username and Password of the local administrator and click Unlock.
-
Click Join adjacent to the text Network Account Server.
-
Specify the IP address of Active Directory domain in Server.
For example, company.com.
-
Specify AD Admin User and AD Admin Password.
-
Click OK.
A green icon is displayed adjacent to your domain name indicating, that the Mac system is joined to the domain.
-
Click Edit > Open Directory Utility.
-
Click the lock icon in lower-left of the Directory Utility screen to unlock and edit the settings.
-
Specify Username and Password of local administrator.
-
Double click the Active Directory.
-
Click the show options icon to view the hidden options.
-
Click Administrative.
-
Select Allow administration by to grant administrative privileges for members of the Active Directory on the local Mac.
-
Click OK.
-
Click the lock icon to prevent further changes.
-
Close the Directory Utility and Users & Groups screens.
To verify the binding, perform the following steps:
-
Open Terminal.
-
Run the following command to log in as an Active Directory user:
login <UsernameOfActiveDirectoryUser>
For example, login pjones.
-
Specify the password. The console switches to the logged in user.
-
Run the command: exit to close the Terminal.
-
Click the Apple icon in upper-left corner and select Log Out <username>.
-
Click Other in the user selection screen to log in as a different domain user.
3.2.11 Enabling the Offline Mode
-
Click the Apple icon in upper-left corner.
-
Click System Preferences > Users & Groups.
-
Select Login Options.
-
Click the lock icon in lower-left of the window to unlock and edit the settings.
-
Specify Username and Password of the local administrator and click Unlock.
-
Click Edit next to Network Account Server.
-
Click Open Directory Utility.
-
Click the lock icon in lower-left of the window to unlock and edit the settings.
-
Specify Username and Password of the local administrator and click Unlock.
-
Double click Active Directory.
-
Click the show options icon to view the hidden options.
-
Select Create mobile account at login.
-
Click OK.
NOTE:The users must create a mobile account to use Mac OS X Client in the offline (cached) mode. For more information about creating a mobile account, see Creating a Mobile Account for the Offline Mode.
3.2.12 Displaying Other User on the Login Screen in Non-Domain Mode
Open the terminal and run the following command to display Other User on the login screen of the non-domain mode:
sudo defaults write /Library/Preferences/com.apple.loginwindow SHOWOTHERUSERS_MANAGED -bool TRUE
3.2.13 Creating a Mobile Account for the Offline Mode
To use Mac OS X Client in the offline mode, you must create a mobile account for a domain user. Perform the following steps to create the mobile account for a domain user:
-
Log in as a domain user.
-
Click the Apple icon in the upper-left corner and select System Preferences.
-
Click Users & Group.
-
Click the lock icon in lower-left of the screen to unlock and edit the settings.
-
Specify Username and Password of the local administrator and click Unlock.
-
Select the preferred domain user.
-
Select Create Mobile Account for the User.
-
Click Create.
The operating system gets logged off automatically.
3.2.14 Displaying the Authentication Window on Unlock Screen
Sometimes, when users log in or unlock a Mac machine with the Mac Client installed, the authentication window disappears at some point during the process. If the user moves the mouse, the screen directs to the beginning of the login or unlock process. A solution to this issue, when the Mac Client is in sleep, lock, or screen saver mode, you can display an authentication window instead of blank or black screen.
Perform the following steps to display an authentication window during sleep, lock or screen saver mode:
-
Open the configuration file \Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify keep_window_on_unlock: true (default value is false) to display the authentication window during the unlocking process until the user closes the window manually.
With the keep_window_on_unlock parameter set to false, the authentication window disappears if user is inactive (no click on mouse or no use of keyboard) for 30 seconds. However, the authentication window does not disappear if the user is active.
-
Save the configuration file.
-
Restart the operating system.
3.2.15 Disabling Linked Chains for Offline Login
With a linked chain, users can authenticate to the Mac OS client within the grace period after successful authentication with the required chain.
For example, LDAP Password+Card is a required chain, and Card is a linked chain. The users must use the LDAP Password+Card chain once in every 8 hours and within this period, they can only provide card without the LDAP Password to authenticate.
By default the linked chains are available in both online and offline mode.
NOTE:An administrator must ensure that the Enable linked chains option is set to ON in the Linked chains policy of the Administration portal to allow users to login with the linked chain.
To disable linked chains for offline login, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify enableLinkedChainsOffline:false. The default value is true.
-
Save the changes.
-
Restart the operating system.
3.2.16 Enabling the Profiling Tool
You can configure the Mac OS X Client to enable the profiling for Web server logs of the Advanced Authentication server. Profiling tool helps in tracking the performance, memory allocation, and CPU utilization of each REST API calls that are processed including the background programs that are initiated by the call. In case of an issue, it facilitates in identifying the cause.
Enabling the profiling tool appends &profiling=true parameter to API calls sent to the server. Before enabling profiling, ensure to set Debugging Logs to ON in the Administration portal. After enabling the Profiling tool, you can track the detailed logs in Logs > Web server in the Administration portal.
To enable the Profiling tool, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
If the file does not exist, create a new file.
-
Specify rest_profiling: true (default value is false).
-
Save the changes.
-
Restart the operating system.
3.2.17 Localizing the Messages for Clients
You can localize error messages, method message, and prompt message displayed on endpoints to an unsupported language.
To localize the client messages to an unsupported language, perform the following steps:
-
Navigate to Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/Resources/aucore/locale.
-
Create a new folder for preferred language and name the folder as per ISO nomenclature standards.
To know more about ISO nomenclature standard, see http://www.loc.gov/standards/iso639-2/php/langcodes-search.php.
For example, if you need to create a new folder for Latin, name the folder la.
NOTE:While naming the folder, keep the following points in mind:
-
The name of the language folder should be in lower case.
-
If the ISO standard name of a language contains any special character such as hyphen or period, replace the special character with an underscore.
For example, if the ISO code of a language is fr.ca, name the language folder fr_ca.
-
-
Inside the preferred language folder, create a new folder and name it LC_MESSAGES.
-
Copy aaacachesrv.pot, aucore.pot and aucore_login.pot files, and paste it in /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/Resources/aucore/locale/<language>\LC_MESSAGES.
-
Open the aaacachesrv.pot, aucore.pot and aucore_login.pot files in a text editor. For example, PoEditor.
-
Specify the preferred language message in the msgstr "".
For example, if you need to localize password will expire in $(days) days message to Latin, specify in password erit exspirare $ (dies) dierum in msgstr "" as in the following image.
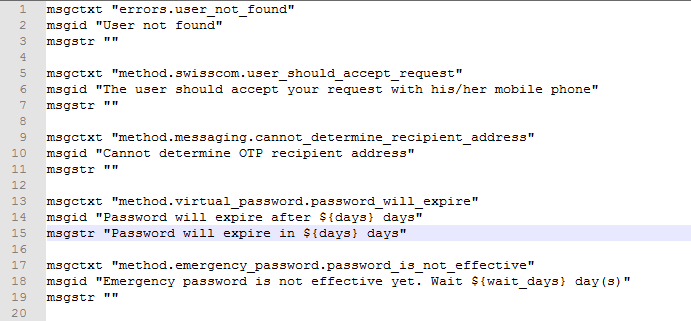
-
Save the changes.
-
Convert the aaacachesrv.pot, aucore.pot and aucore_login.pot files to.mo format using Po editing tools. For example, PoEditor.
-
Change the Administrative language of the operating system to the preferred language.
-
Restart the operating system.
3.2.18 Changing the Locale of Mac OS Client without Changing the Locale of the Operating System
This option allows you to change the locale of Mac OS Client without changing the locale of the operating system.
For example, if the default language of your operating system is English, you can configure Mac OS Client to display the messages and warnings in German.
To change the locale, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
-
Specify the following parameter:
locale: ISO code of the preferred language.
NOTE:While changing the locale, keep the following points in mind:
-
The code of the language should be in lower case.
-
If the ISO standard name contains any special character such as hyphen or period, replace the special character with an underscore.
For example, if the ISO code is fr.ca, then the value should be fr_ca.
NOTE:By default, no value is specified. If no parameter is specified in the configuration file,operating system’s default locale will be picked.
-
-
Save the changes.
-
Restart the operating system.
3.2.19 Configuring the TLS Version
You can configure the TLS version that the network library of the Mac OS Client uses for establishing HTTPS connection with the Advanced Authentication server. The default version is TLSv1.3.
To configure the TLS version, perform the following steps:
-
Open the configuration file /Library/Security/SecurityAgentPlugins/aucore_login.bundle/Contents/etc/aucore_login.conf.
-
Specify tlsVersion: value. The values are defined as follows:
-
TLSv1.3
NOTE:TLSv1.3 is applicable only for Advanced Authentication 6.3 Service Pack 7 and later versions.
-
TLSv1.2
-
TLSv1.1
-
TLSv1
-
All: Network library will choose the TLS version automatically.
NOTE:If you set invalid or unknown value for the tlsVersion parameter, then the default value TLSv1.3 is set automatically.
-
-
Save the changes.