9.8 Configuring Integration with ADFS
This section provides the configuration information on integrating Advanced Authentication with ADFS. This integration secures the ADFS connection.
The following diagram represents Advanced Authentication in ADFS.
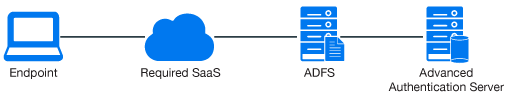
To configure the Advanced Authentication integration with ADFS (Active Directory Federation Services) using SAML 2.0 perform the following configuration tasks:
NOTE:These instructions are valid only for ADFS 3 and 4.
9.8.1 Configuring the Advanced Authentication SAML 2.0 Event
-
Open the Advanced Authentication Administration portal.
-
Click Events > Add to add a new event.
-
Create an event with the following parameters:
-
Name: ADFS_SAML.
-
Event Type: SAML 2.
-
Chains: Select the required chains.
-
Paste the content of the file https://<adfs_hostname>/FederationMetadata/2007-06/FederationMetadata.xml to SP SAML 2.0 meta data.
Or
-
Click Browse and upload the saved XML file.
-
-
Click Save.
NOTE:Verify that you can access the file in your browser. If the file is not displayed, you have an issue on ADFS that you must resolve.
-
-
Click Policies > Web Authentication.
-
Set Identity provider URL to https://AdvancedAuthenticationServerAddress/ and replace AdvancedAuthenticationServerAddress with the domain name or IP address of your Advanced Authentication server.
NOTE:To use multiple Advanced Authentication servers with SAML 2.0, you must do the following:
-
Configure an external load balancer.
-
Specify the address in Identity provider URL instead of specifying an address of a single Advanced Authentication server.
-
-
Click Download IdP SAML 2.0 Metadata.
You must open the file as an XML file.
NOTE: If {"Fault":{... ` is displayed, you must verify the configuration.
9.8.2 Making the Corresponding Changes in ADFS
-
Open the ADFS management console.
-
Expand Trust Relationships.
-
Click Add Claims Provider trust.
-
Paste OSP metadata URL https://<AAF_server_hostname>/osp/a/TOP/auth/saml2/metadata.
It may not work for self-signed certificate. You can copy metadata from OSP URL to an XML file and provide the file name.
-
Specify the Display name.
-
Select Open the Edit Claim Rules dialog for this claims provider when the wizard closes.
-
In Edit Claims Rules, click Add Rule.
-
Select Send Claims Using a Custom Rule.
-
Click Next.
-
Specify Claim rule name.
-
Paste Custom rule and click Finish.
c:[Type == "upn"]=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType);
-
In ADFS snap-in, double click on the provider name.
-
Click Advanced.
-
Move the hash algorithm from SHA-256 to SHA1.
-
Click OK.