8.7 Configuring Policies
To configure an applicable policy for Advanced Authentication, follow the steps:
-
Open the Policies section. The list of available authentication methods will be displayed.
-
Click the Edit button next to an applicable policy.
-
Edit configuration settings for a specific policy.
-
Click Save at the bottom of the Policies view to save changes.
In the section you can find the following settings:
-
Admin UI Whitelist: security settings which allows to limit using of Advanced Authentication Administrative Portal only for permitted IP addresses.
-
Authenticator management options: setting that allows a helpdesk (security officer) to link authenticators of a user to help authenticate to another user’s account. This policy also allows you to disable re-enrollment of authenticators by users in the Self-Service portal.
-
Cache options: security settings which allows to disable local caching of authenticators.
-
CEF log forwarding: settings to configure an external syslog server.
-
Delete me options: Enable/Disable delete me option.
-
Endpoint management options: an option to require authentication data for Endpoint creation. It must be disabled when installing Advanced Authentication Access Manager Advanced Authentication plug-in.
-
Event categories: Allows you to add categories, which can be used in an event to support multiple enrollments for a method.
-
Geo fencing options: setting that helps to create authentication zones by drawing boundaries for a geographical location.
-
HTTPS Options: setting that allows administrators to configure policies to ensure that appliance is safe from security vulnerabilities.
-
Helpdesk Options: a security option which allows to disable asking for user's credential when a security officer is managing the user's authenticators.
-
Kerberos SSO Options: Allows you to select a repository for Kerberos single sign-on.
-
Last Logon Tracking Options: allows to enable tracking for last logon to configure and use simple chain corresponding to a high-security chain.
-
Lockout Options: security settings which allows to lock user after some authentication failures.
-
Login Options: allows to specify the default repositories, to avoid of necessity to enter a repository name in username field.
-
Logo: setting that allows you to set an image or alternate text as a logo for the Administration and Self-Service portal.
-
Logon Filter for AD: Enable/Disable logon filter for Active Directory.
-
Mail sender: SMTP server settings.
-
Multitenancy Options: Enable/Disable multitenancy mode in the appliance.
-
Password Filter for AD: Enable/Disable password filter for Active Directory.
-
SAML 2.0 options: settings that allows you to add external URL and to download identity provider’s SAML 2.0 Metadata.
-
SMS sender: settings for external SMS service provider, contains predefined settings for Twilio, MessageBird.
-
Services Director Options: setting to enable the integration with Services Directory.
-
Voice sender: Twilio settings for Voice and Voice OTP method; an option to allow enrollment for users without telephone number.
IMPORTANT:The configured policies will be applied for all servers.
NOTE:A tenant administrator will not have access to CEF log forwarding and Multitenancy Options.
8.7.1 Admin UI Whitelist
The Admin UI whitelist settings are located in the Policies section.
The settings allows to configure access to the Advanced Authentication Administrative Portal only for permitted IP addresses. By default the restrictions are not set. To configure the restrictions click Add button. Enter address in format 10.20.30.0/255.255.255.0 or 10.20.30.0/24. Advanced Authentication has an automatic check which allows to prevent administrators from losing access to the Administrative Portal. If your IP address is out of the range you will see a message: Your IP address is not whitelisted. You will lose access! Please add your IP.To apply the changes click Save button.
8.7.2 Authenticator management options
This policy allows you to configure two settings:
-
Enable sharing: This setting allows a user to authenticate with his/her authenticator to another user’s account. The helpdesk admin will be able to link an authenticator of one user to another user.
To enable sharing authenticators, turn Enable sharing to ON.
NOTE:Only online logon by linked authenticators is supported. Cached logon is not supported.
NOTE:The supported methods for sharing authenticators are TOTP, HOTP, Password, Fingerprint, Card and FIDO U2F.
-
Disable re-enrollment: This setting allows you to restrict users from re-enrolling, editing, and deleting the enrolled authenticators in the Self-Service portal.
To disable re-enrollment or removal of authenticators, turn Disable re-enrollment to ON.
NOTE:This setting disables re-enrollment and removal of the authenticators only in the Self-Service portal. The setting has no effect on the Helpdesk portal.
8.7.3 Cache Options
The Cache options are located in the Policies section.
NOTE: This functionality is supported for Windows Client, Mac OS X Client, Linux PAM Client for chains which use the methods: LDAP Password, Password, HOTP, TOTP, Smartphone (offline mode), Card, FIDO U2F, Fingerprint and PKI.
The caching functionality allows to store credentials on client side for offline authentication when the Advanced Authentication Server is not available. This helps a user who performed a successful logon with the Advanced Authentication Server when the server was available, to use the offline authentication during a business trip or access the system from home. By default the Enable local caching option is enabled. To disable the caching switch option to OFF and click Save.
NOTE:To cache Fingerprint data, you need to install Microsoft.NET Framework 4 or higher on your workstation.The caching period cannot be configured. Cache will be cleared only if the Enable local caching option is disabled.
8.7.4 CEF log forwarding
The CEF log forwarding settings are located in the Policies section.
The settings allows to configure forwarding of logs to an external Syslog server. The central logging server may be used for log forwarding. To configure it, follow the steps:
-
Open the Policies section.
-
Click the Edit button next to the CEF log forward policy.
-
Select the Enable check box.
-
Specify the IP address of the remote logging server in the Syslog server text field.
-
Specify the port of the remote logging server in the Port text field.
-
Select an applicable transfer protocol from the Transport drop-down list.
-
Click Save at the bottom of the Policies view to save changes.
IMPORTANT:The same Syslog configuration is used for each server type. Each server type in the appliance records its own log file.
Events from all facilities are recorded to syslog. E.g., Advanced Authentication Server Core, Kernel, Daemon, etc.
The following Server Core events are being recorded in the log file:
-
Failed to join endpoint
-
No rights to join endpoint
-
Endpoint joined
-
Failed to remove endpoint
-
No rights to remove endpoint
-
Endpoint remove
-
Failed to create endpoint session
-
Endpoint session ended
-
Failed to create endpoint session
-
Invalid endpoint secret
-
Endpoint session started
-
Failed to create local user
-
Local user was created
-
Failed to remove local user
-
Local user was removed
-
Repository configuration was changed
-
Failed to add repository
-
New repository was added
-
Request failed
-
Server started
-
Server stopped
-
Server unexpectedly stopped
-
Failed to assign template to the user
-
Template was assigned to the user
-
Failed to change template
-
Template was changed
-
Failed to enroll template for the user
-
Template was enrolled for the user
-
Failed to link template
-
Template was linked
-
Failed to remove template link
-
Template link was removed
-
Failed to remove template
-
Template was removed
-
Failed to create user
-
User was created
-
User can't enroll the assigned template
-
User enroll the assigned template
-
User was failed to authenticate
-
User logon started
-
User was successfully logged on
-
User was switched to different method
-
User do not want logon by phone but Twilio calling
-
User read app data
-
User write app data
8.7.5 Delete me options
The Delete me options allow you to enable/disable Advanced Authentication users with Delete me option, which can be used to delete all user data including enrolled methods and all data from the repository.
If Enable delete me feature is set to ON, then Advanced Authentication users will get Delete me option by clicking on the user name drop-down list in top right corner of the Self-Service portal. By clicking Delete me and then clicking OK, all the user data from the repository including the enrolled methods are deleted.
If Enable delete me feature is set to OFF, then Advanced Authentication users will not get Delete me option in the Self-Service portal.
8.7.6 Endpoint Management Options
The Endpoint management options are located in the Policies section.
If the option Require admin password to register endpoint/workstation is enabled, the Advanced Authentication will require endpoints to provide the local administator's credentials during installation of endpoint component.
The option must be disabled when installing the Access Manager Advanced Authentication plug-in or Advanced Authentication Windows Client or Advanced Authentication MacOS Client. Otherwise the endpoints will not be created.
8.7.7 Helpdesk Options
The Helpdesk options are located in the Policies section.
The options provide security settings for security officers who manage users' authenticators in Helpdesk Portal.
With the enabled Ask credentials of management user option the security officers should provide credentials of users before its management. This authentication uses the Helpdesk User event. Ensure that you have specified a chain for the Helpdesk User event.
When the option is set to OFF a security officer doesn't need to provide credentials of managed user. This may be not secure, but user management can be done much faster when the option is disabled.
8.7.8 HTTPS Options
This policy allows you to configure two settings:
-
Enable TLS 1.0: Advanced Authentication recommends to keep the option disabled by default to ensure security vulnerabilities are prevented as TLS 1.0 is considered as an unsafe protocol. In some cases, you may enable the option to support old versions of browsers. For more information on browser support for TLS, see TLS support for web browsers.
-
Enable HTTP compression: This setting allows you to enable HTTP compression to accelerate performance in the scenarios of low band with or when the network connectivity is very slow.
8.7.9 Kerberos SSO Options
The Kerberos SSO options policy allows you to select an Active Directory repository, which points to a domain for which you want to configure single sign-on.
Perform the following steps:
-
Select a required repository.
-
Click Save. A message Policy "Kerberos SSO options" saved is displayed.
-
Wait for 2-3 minutes for the changes to apply.
NOTE:This feature works only for a single Active Directory repository at a time and is disabled in multitenancy mode.
Generate a keytab file for each Advanced Authentication Server and upload them in appliance for each server. For more information, see Uploading Keytab File.
After configuring the Kerberos SSO options and uploading the keytab files, enable Allow kerberos SSO option for the required event. Kerberos SSO is supported for AdminUI, Authenticators Management, Helpdesk and Report logon events. For more information on configuring an event, see Configuring Events.
By default, basic authentication window is displayed in your browser while accessing a configured Advanced Authentication portal. Advanced Authentication Servers’ sites must be added to the Local intranet in browser on the domain-joined workstations to avoid it. Perform the following steps to do it for Internet Explorer:
-
From the Start menu, navigate to Control Panel > Network and Internet > Internet Options.
-
In the Internet Properties window, click Security tab and then select Local intranet.
-
Click Sites.
-
In the Local intranet window, click Advanced.
-
Add the Advanced Authentication Servers’ sites to the zone. For example: https://v5.netiq.loc or v5.netiq.loc
-
Click Close and save the changes.
NOTE:Basic authentication window is displayed while accessing a configured Advanced Authentication portal, if Kerberos SSO option is enabled for Authenticators Management event and security is set to High for Local intranet in Internet Explorer.
NOTE:By default, Firefox browser does not support single sign-on. If you are using Firefox browser, then you can enable single sign-on by performing the steps suggested in the website.
8.7.10 Last Logon Tracking Options
The Last Logon Tracking options allow you to enable tracking for the last logon. You can simplify multi-factor authentication by automatically switching to another (simple) chain (that contains less factors) within few hours of authentication by a high-security chain. For example, if a user authenticates by the LDAP Password+Card methods once in a day, the user can further use only Card without the LDAP Password method, or if a user authenticates by the Fingerprint+SMS methods once in every four hours, the user can further use Smartphone authentication only.To enable tracking, switch the Enable tracking option to ON.To configure a high-security chain and the corresponding simple chain, see Creating Chains.
8.7.11 Lockout Options
The Lockout options are located in the Policies section.
The options allows to configure the user account lockout in case of reaching limit on failure attempts. It may be used to prevent of guessing the one-time passwords. It's possible to configure the following settings:
-
Enable: The option enables the lockout settings.
-
Failed attempts: The option allows to setup a limit of authentication attempt failures after which the user account will be locked. 3 attempts by default.
-
Lockout period: The option allows to configure a period within which the user will be locked and not possible to authenticate. 300 seconds by default.
-
Lock in repository: The option allows to lock the user account in repository. The Lockout period option is not used for the case. It will be required for system administrator to unlock the user manually in the repository.
IMPORTANT:You need to configure the appropriate settings in your repository, for the options to function correctly.
For Active Directory Domain Services, the Account lockout threshold policy must be enabled on Domain Controllers.For NetIQ eDirectory the Intruder Detection must be properly configured.
It's possible to manage the locked users (only the users who are not locked in repository). To do it switch to the Repositories section. Click Edit button for the used repository. Switch to Locked Users tab. Click Remove button next to account name to unlock the user account.
8.7.12 Login Options
The Login options are located in the Policies section.
Here it's possible to configure the Default repositories. Using the Default repositories it's not required to enter repository name before a username for authentication. So instead of company\pjones it will be possible to enter only pjones, instead of local\admin it will be possible to use admin.
8.7.13 Logo
This policy allows you to set and customize an image as a logo for the Administration and Self-Service portal. You can also set an alternate text instead of an image as logo.
To set a logo for the Administration and Self-Service portal, perform the following steps:
-
In the Logo page, set Use image to ON.
-
Specify an alternate text for the image in Image ALT text.
-
Specify the URL that is displayed when you click on the logo.
-
Select an image for the logo. The image resolution must be 230x50 pixels. The supported formats are jpg and png.
-
You can also set a mini logo with an image. This mini logo is displayed when the navigation pane on the left is collapsed. The image resolution for the mini logo must be 50x50 pixels.
-
Click Save.
NOTE:The logo is applied for all the tenants. A tenant administrator cannot customize the logo.
8.7.14 Logon Filter for AD
The Logon Filter for AD is located in the Policies section.
This policy enables use of Logon Filter which must be installed on all Domain Controllers in the domain and must be properly configured. Logon Filter allows you to prohibit authentications of users without the Advanced Authentication solution.
For information to configure Logon Filter, see Configuring Logon Filter.
8.7.15 Mail Sender
The Mail sender settings are located in the Policies section.
The section contains the mail server settings. It's used by Email OTP to send the email messages with one-time passwords to users.
It's required to configure the following settings:
-
Host, the outgoing mail server name (e.g. smtp.company.com)
-
Port, the used port number (e.g. 465)
-
Username, username of an account which will be used to send the authentication email messages (e.g. noreply or noreply@company.com)
-
Password, password for the specified account
-
TLS and SSL is used to specify a cryptographic protocol used by the mail server.
Click Save to apply the changes.
Authentication flow
The following chart demonstrates the authentication flow:
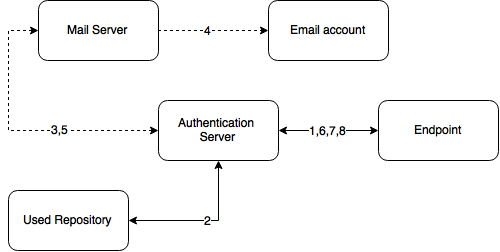
A user is authenticating on endpoint (which can be the user's laptop with Advanced Authentication Windows Client installed or a website etc.) by Email method.
-
The endpoint calls the Advanced Authentication Server.
-
It validates the provided user's credentials and gets an email address of the user from a used Repository.
-
Advanced Authentication Server sends the request to a configured Mail Server to send an Email message with generated content which includes a one-time password (OTP) for authentication.
-
Mail Server sends the message to the user's email address.
-
Mail Server sends the 'sent' signal to the Advanced Authentication Server.
-
Advanced Authentication Server sends a request to enter an OTP on the endpoint side.
-
The user enters an OTP from the email message. The Advanced Authentication Server gets the OTP.
-
Advanced Authentication Server validates the authentication. The authentication is done/ forbidden.
HTTPS protocol is used for the internal communication.
Access configuration
Advanced Authentication Server - Mail Server (SMTP, outbound).
8.7.16 Multitenancy Options
A tenant is a company with a group of users sharing common access with specific privileges. Multitenancy options allows you to have a single instance of Advanced Authentication solution supporting multiple tenants. You can enable Multitenancy Options when you need to support more than one tenant on a single appliance.You can enable or disable multitenancy option.
IMPORTANT:If you have the workstations with Windows Client, Mac OS X Client or Linux PAM Client installed, then perform the following steps before enabling Multitenancy Option:
-
Upgrade the client components to 5.4 or above.
-
Configure the clients to point to a tenant. For more information on configuring in Windows Client, refer to Configuration Settings for Multitenancy. For more information on configuring in Mac OS X Client, refer to Configuration Settings for Multitenancy. For more information on configuring in Linux PAM Client, refer to Configuration Settings for Multitenancy.
The steps listed above are critical and if not performed, the users on the workstations will not be able to login.
8.7.17 Password Filter for AD
Password Filter automatically updates the LDAP Password stored inside Advanced Authentication, whenever the password is changed or reset in the Active Directory. This helps you to authenticate without getting any prompt to synchronize the password after it is changed or reset.
Set Update password on change option to ON, to enable updating of the LDAP password in Advanced Authentication, when it is changed in the Active Directory. This helps you to authenticate without getting any prompt to synchronize the password after it is changed. If Update password on change is set to OFF, user will get a request to synchronize the password while logging in to Windows, if he/she changed his/her password where the user will need to enter an actual password.
Set Update password on reset option to ON, to enable updating of the LDAP password in Advanced Authentication, when it is reset in the Active Directory. This helps you to authenticate without getting any prompt to synchronize the password it is reset. If Update password on reset is set to OFF, user will get a request to synchronize the password while logging in to Windows, if administrator has reset the user's password where the user will need to enter an actual password.
NOTE:Endpoint for Password Filter should be trusted. To set this option, open the Advanced Authentication - Administrative Portal > Endpoints section, edit an endpoint of the Password Filter, set Is trusted flag to ON and add a description. Save the changes.
8.7.18 SMS Sender
The SMS sender settings are available in the Policies section.
This section contains the SMS service provider settings. It is used by SMS OTP to send the SMS messages with one-time passwords to users. Advanced Authentication contains the predefined settings for Twilio and MessageBird services.
To configure SMS sender settings for Twilio service select Twilio in Sender service drop down list and fill or set the following fields:
-
Account sid
-
Auth token
-
Use Copilot
-
Sender phone
-
Messaging Service SID
NOTE:Messaging Service SID option is enabled only when Use Copilot option is set to ON.
You can find more information on the Twilio website.
For more information on Copilot and its features, visit the following websites:
https://www.twilio.com/copilot#phone-number-intelligence
https://www.twilio.com/docs/api/rest/sending-messages-copilot#features
To configure SMS sender settings for MessageBird service, select Messagebird in Sender service drop down list and fill the following fields:
-
Username
-
Password
-
Sender name
You can find more information on the MessageBird website.
IMPORTANT:MessageBird API v2 is not supported. To activate MessageBird API v1, go to the MessageBird account, click Developers from the left navigation bar and open the API access tab. Click Do you want to use one of our old API's (MessageBird V1, Mollie or Lumata)? Click here.
To configure SMS sender manually, select Generic in Sender service drop down list and perform the following steps:
-
Specify a Service URL value. For example: Clickatell http://api.clickatell.com/http/sendmsg?.
-
Leave the HTTP Basic Auth Username and HTTP Basic Auth Password text boxes blank.
-
Select POST from the HTTP request method drop down list.
-
Click Add and create the following parameters in HTTP request body section.
-
name: user
value: name of your account
-
name: to
value: {phone}
-
name: text
value: {message}
-
name: api_id, this is a parameter issued upon addition of an HTTP sub-product to your Clickatell account. A single account may have multiple API IDs associated with it.
-
name: from
value: sender’s phone number
-
-
Click Add secure and create the following parameter in HTTP request body section.
-
name: password
value: current password that is set on the account
For more information on additional parameters for Clickatell, refer to the Clickatell documentation.
NOTE:The parameters may differ for different SMS service providers. But the {phone} and {message} variables are obligatory.
-
-
Click Save at the bottom of the view to save changes.
Authentication flow
The following chart demonstrates the authentication flow:
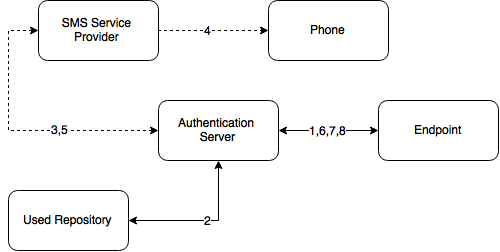
A user is authenticating on endpoint (which can be the user's laptop with Advanced Authentication Windows Client installed or a website etc.) by SMS method.
-
The endpoint calls the Advanced Authentication Server.
-
It validates the provided user's credentials and gets a phone number of the user from a used Repository.
-
Advanced Authentication Server sends the request to a configured SMS Service Provider to send an SMS message with generated content which includes a one-time password (OTP) for authentication.
-
SMS Service Provider sends the SMS message to the user's phone.
-
SMS Service Provider sends the 'sent' signal to the Advanced Authentication Server.
-
Advanced Authentication Server sends a request to enter an OTP on the endpoint side.
-
The user enters an OTP from the SMS message. The Advanced Authentication Server gets the OTP.
-
Advanced Authentication Server validates the authentication. The authentication is done/ forbidden.
HTTP/HTTPS protocol is used for the communication.
Access configuration
Advanced Authentication Server - SMS Service Provider (HTTP/HTTPS, outbound).
8.7.19 Services Director Options
This policy allows you to integrate with the Services Director.
To enable the integration of Advanced Authentication with Services Director, turn Enable integration to ON.
Enter the Public DNS name of Advanced Authentication, Services Director DNS Name, Tenant Admin Name and Tenant Admin Password of Services Director to integrate it with Advanced Authentication.
NOTE:You cannot integrate Services Director with Advanced Authentication when Multitenancy is enabled.
8.7.20 Voice Sender
The Voice sender settings are located in the Policies section.
The section contains the Voice and Voice OTP method settings. It is used by Voice and Voice OTP. Advanced Authentication supports the Twilio service.
The following fields must be filled in Twilio section:
-
Account sid
-
Auth token
-
Sender phone
-
Public server url
The information regarding fields 1-3 you may get on the Twilio website. The Public server url must contain a public URL to where the Twilio service will connect for authentication. It's possible to use http protocol for testing purposes, but for production environment it's recommended to use https protocol. You need to have a valid certificate when using https.
The Enroll without phone section allows to configure behavior when a user is trying to enroll the Voice authenticator, but the user's repository data doesn't contain a phone number. If Allow enroll user w/o phone option is set to OFF such user will not be able to enroll the Voice authenticator and the user will get an error message, which can be specified in Error message field.
Click Save to apply the changes.
IMPORTANT:The users may get the calls with voice speaking Application error. It may happen because of not correct settings or invalid certificate. Ensure that the certificate is valid and not expired. Invalid certificate cannot be applied by Twilio.
Authentication flow
The following chart demonstrates the authentication flow:
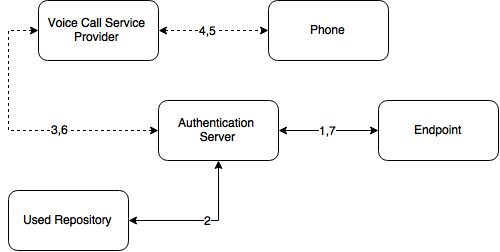
A user is authenticating on endpoint (which can be the user's laptop with Advanced Authentication Windows Client installed or a website etc.) by SMS method.
-
The endpoint calls the Advanced Authentication Server.
-
It validates the provided user's credentials and gets a phone number of the user from a used Repository.
-
Advanced Authentication Server sends the request to a configured Voice Call Service Provider (Twilio) to call the user.
-
Voice Call Service Provider calls the user.
-
The user picks up the phone, listens to the answerphone and enters the PIN code followed by hash sign.
-
Voice Call Provider sends the entered PIN code to the Advanced Authentication Server.
-
Advanced Authentication Server validates the authentication. The authentication is done/ forbidden.
HTTP/HTTPS protocol is used for the communication.
Access configuration
Advanced Authentication Server - Voice Call Service Provider (HTTP/HTTPS, inbound/ outbound).
8.7.21 Geo fencing options
This policy allows you to create authentication zones by drawing boundaries for a geographical location. When you enable geo-fencing, users will be able to authenticate with Smartphone from only allowed geographical locations.
To enable geo-fencing, turn Enable geo fencing to ON.
NOTE:When you enable Geo-fencing, the functioning of the TOTP mode of the Smartphone method, which is used in the offline mode, is affected. An error message TOTP login is disabled is displayed to the users when they try to authenticate with this method.
8.7.22 Event categories
This policy allows you to add categories, which can be used in an event to support multiple enrollments for a method.
To add a category, click Add and then enter a name and description for the category. Click Save to save the category.
NOTE:
-
It is possible to enroll only one authenticator of one type per category.
-
The Categories functionality is disabled when no category is created.
8.7.23 SAML 2.0 options
This policy allows you to enter Identity Provider’s URL and to download SAML 2.0 Metadata file. The downloaded SAML 2.0 Metadata file is used to configure the service provider.
IMPORTANT:WebAuth feature must be enabled in Server Options before configuring the policy.
Perform the following steps in SAML 2.0 options:
-
Enter the Identity Provider’s URL, if required.
-
Click Download IdP SAML 2.0 Metadata to open the Metadata.
IMPORTANT:At least one SAML 2.0 event must be created before downloading a metadata file in the policy.
-
The Metadata opens in a new browser page. Save the Metadata (XML text) from the browser.
-
Use the downloaded metadata file in your Service Provider, if required.
For information on how to configure Advanced Authentication integration with Salesforce using SAML2, see Configuring Integration with Salesforce
.