1.5 Recommended Installation Scenarios
The following scenarios provide an overview of the flexibility built into Access Manager. Use them to design a deployment strategy that fits the needs of your company.
1.5.1 Basic Setup
You need to protect Administration Console from Internet attacks. Install it behind firewall. For a basic Access Manager installation, you can install Identity Server and Access Gateway outside your firewall. Figure 1-5 illustrates this scenario:
Figure 1-5 Basic Installation Configuration

-
Install Administration Console.
Administration Console and Identity Server are bundled in the same download file or ISO image.
-
If firewall is set up, open the ports required for Identity Server and Access Gateway to communicate with Administration Console:
TCP 1443, TCP 8444, TCP 1289, TCP 1290, TCP 524, TCP 636.
For more information about these ports, see Section 1.8, Setting Up Firewalls.
-
Run the installation again and install Identity Server on a separate server.
Log in to Administration Console and verify that Identity Server installation was successful.
-
Install Access Gateway.
Log in to Administration Console and verify that Access Gateway imported successfully.
-
Install Analytics Server.
Log in to Administration Console to verify that Analytics Server is imported successfully.
-
Configure Identity Server, Analytics Server, and Access Gateway. See Configuring Access Manager in the Access Manager 4.5 Administration Guide.
In this configuration, the LDAP server is separated from Identity Server by firewall. Ensure that you open the required ports. See Section 1.8, Setting Up Firewalls.
For information about setting up configurations for fault tolerance and clustering, see High Availability and Fault Tolerance in the Access Manager 4.5 Administration Guide.
Firewall protects the LDAP server and Administration Console, both of which contain a permanent store of sensitive data. Web servers are installed behind the firewall for added protection. Identity Server does not permanently store any user data. This is the recommended configuration. This configuration also supports an L4 switch in place of a router to support clusters of Identity Servers and Access Gateways.
1.5.2 High Availability Configuration with Load Balancing
Figure 1-6 illustrates a deployment scenario where web resources are securely accessible from the Internet. The scenario also provides high availability because both Identity Servers and Access Gateways are clustered and have been configured to use an L4 switch for load balancing and fault tolerance.
Figure 1-6 Clustering Configuration for High Availability
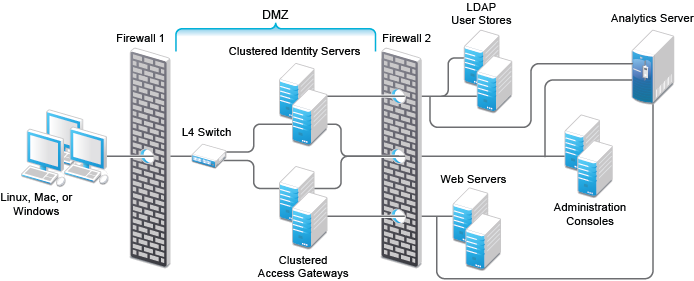
You can configure end users to communicate with Identity Servers and Access Gateways through HTTP or HTTPS. You can configure Access Gateways to communicate with web servers through HTTP or HTTPS. Multiple Administration Consoles provide administration and configuration redundancy.
This configuration is scalable. As the number of users increase and the demands for web resources increase, you can easily add another Identity Server or Access Gateway to handle the load, then add the new servers to the L4 switch. When the new servers are added to the cluster, they are automatically sent the cluster configuration.