1.7 Installing Access Manager Components in NAT Environments
You can deploy Access Manager components in a multi-tenant or service provider environment, where Network Address Translation (NAT) protocol is used as one of the network configuration.
This section includes the following topics:
1.7.1 Network Prerequisites
Service Provider Network Setup
-
Obtain Static IP addresses for Administration Console, Identity Server, and Analytics Server or Sentinel. If the IP address of the machine changes, Access Manager components on that machine cannot start.
-
Install operating system, configure Network Time Protocol (NTP) server, and check connectivity.
-
NTP server, which provides accurate time to the machines on your network. Time must be synchronized within one minute among the components, or the security features of the product disrupt the communication processes. You can install your own or use a publicly available server such as pool.ntp.org.
IMPORTANT:If time is not synchronized, users cannot authenticate and access resources and data corruption can also happen in user stores.
-
An L4 switch if you need to configure load balancing. This can be hardware or software (for example, a Linux machine running Linux Virtual Services).
-
IP connectivity is established between different Access Manager components. Because the components can be in different private networks, you can use NAT, VPNs, or combination of both to achieve connectivity.
Customer Network Setup
-
A server configured with an LDAP directory (eDirectory 8.8.8.8 or later, Sun ONE, or Active Directory) that contains your system users. Identity Server uses the LDAP directory to authenticate users to the system.
-
Domain name server, which resolves DNS names to IP addresses and which has reverse lookups enabled.
Access Manager devices communicate to each other by their IP addresses, and some requests require them to match an IP address with the device's DNS name. Without reverse lookups enabled, these requests fail. In particular, Identity Servers perform reverse lookups to their user stores. If reverse lookups are not available, host table entries can be used.
-
Obtain Static IP addresses for Administration Console, Identity Server, and Analytics Server or Sentinel. If the IP address of the machine changes, Access Manager components on that machine cannot start.
-
IP connectivity is established between different Access Manager components. Because the components can be in different private networks, you can use NAT, VPNs, or combination of both to achieve connectivity.
1.7.2 Network Setup Flow Chart
Figure 1-9 provides the setup information about installing Access Manager components and configuring NAT in a multi-tenant or service provider network.
Figure 1-9 Network Setup Flow Chart
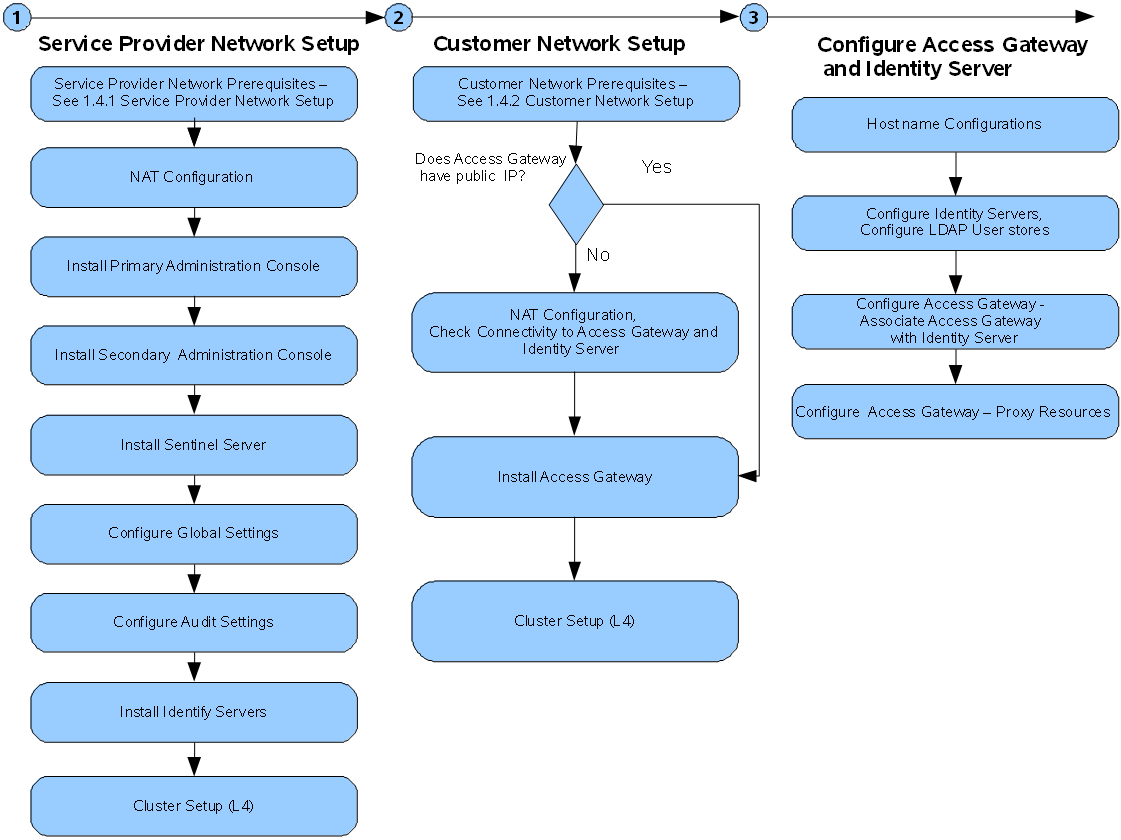
1.7.3 Installing Access Manager Components in NAT Environments
Installing Access Manager in the NAT environment consists of the following steps:
Installing Administration Console
For installation requirements, see Installing Administration Console.
-
Before installing Access Manager components, check the network connectivity across these machines.
-
Verify the link latency and ensure that it is less than 100 milliseconds.
If the link latency is greater than 100ms, it might lead to performance degradation.
-
Synchronize time across all Access Manager components.
The primary Administration Console should be configured to synchronize time with the corporate Network Time Protocol (NTP) server. The remaining machines should be configured to synchronize time with the primary Administration Console.
-
Configure the NTP server in the /etc/ntp.conf file.
For information about how to configure the NTP server, see Configuring NTP.
-
Run the following commands on the primary Administration Console to start the NTP server:
systemctl start ntpd
systemctl enable ntpd
-
Run the ntpdate pool.ntp.org command on the primary Administration Console to synchronize devices.
NOTE:The ntpd process must be running to keep the time in sync among devices.
-
-
Install the primary Administration Consoles by providing the listening IP address for the primary Administration Console.
For more information about installing Administration Console, see the Installing Administration Console on Windows.
-
Install the secondary Administration Console and repeat the above procedures for secondary Administration Console IP address.
-
Continue with Configuring Global Settings to add both the primary and secondary Administration Consoles to the Global Settings configuration.
Configuring Global Settings
You need to map the private IP address of Administration Console and to the public NAT IP address. You need to specify the NAT IP addresses before importing Identity Server and Access Gateway. You need to specify the NAT IP Addresses prior to importing devices. The devices that cannot reach the Private Administration Console IP address will use the NAT IP address.
-
Log in to Administration Console.
-
Select Access Manager > Global Settings.
-
Click New.
-
Select Administration Console Listening IP address from the drop-down list.
-
Specify the corresponding Public NAT IP address.
If you do not specify a Public NAT IP address or if a mapping already exists for the selected Administration Console IP address, the following message is displayed:
IP Address is not valid
-
Click OK to continue and apply the configuration changes.
Installing and Configuring Identity Server
For information about how to install Identity Server, see Installing Identity Server.
User stores are LDAP directory servers to which end users authenticate. You must specify an initial user store when creating an Identity Server configuration. You use the same procedure for setting up the initial user store, adding a user store, or modifying an existing user store.
For information about how to configure Identity Server, see Configuring Identity Servers Clusters in the Access Manager 4.5 Administration Guide.
Installing and Configuring Access Gateway
For information about how to install Access Gateway, see Installing Access Gateway.
When you are setting up Access Gateway to protect web resources, you create and configure reverse proxies, proxy services, and protected resources. The authentication contract, authentication procedure, Authorization policy, Identity Injection policy, and Form Fill policy are configured at the resource level so that you can enable exactly what the resource requires.
For information about configuring Access Gateway, see Configuring Access Gateway in the Access Manager 4.5 Administration Guide.
1.7.4 Configuring Network Address Translation
You can configure Access Manager by using Network Address Translation (NAT). NAT enables the communication between Administration Console from local network to other Access Manager devices such as Identity Server and Access Gateway. The devices can be in the external network or in another private network. You must configure the NAT address in the router.
See your router documentation for more information.
Configuring Administration Console Behind NAT
-
Log in to Administration Console.
-
Go to Access Manager > Global Settings, then click New.
-
Select an IP address from the Administration Console Public IP Address list.
This list contains primary and secondary Administration Console IP addresses.
-
Enter the respective NAT IP address for primary and secondary Administration Console in Public NAT IP Address.
NOTE:If the NAT IP address is not provided or if a mapping exists for the selected Administration Console IP, a message IP Address is not valid is displayed.
-
Click OK.
Administration Console NAT IP is shared to other Access Manager devices.
For more information about configuring NAT, see Mapping the Private IP Address to Public IP Address in the Access Manager 4.5 Administration Guide.
Configuring Identity Server and Access Gateway Behind NAT
During installation, the system prompts the following message to specify the NAT address for the component:
Is local NAT available for the <device name> y/n? [n]:
Enter Y and specify the NAT address. This enables Administration Console to use this NAT address when communicating to this device.
Alternatively, if the device is already installed, then run the reimport_nidp.sh or reimport_ags.sh script to specify the NAT address.