4.5.11 Troubleshooting Risk Rule Configuration
The following sections describe how to troubleshoot rule configuration:
Understanding How to Use the Validate Tool to Emulate Total Risk Score and Risk Levels
After configuring a risk policy and the corresponding risk scores and actions, use Validate to emulate total risk score, risk level, and action in event of rule failure. Based on the results, you can modify the configuration, if required.
Let us consider a case where you have configured a risk policy that includes five rules. The rules and the corresponding risk scores are as follows:
Table 4-12 Sample Risk Policy Configuration: Rules
|
Risk Policy Name |
Rule |
Risk Score |
|---|---|---|
|
Demo_RiskPolicy |
Demo_InNetworkAtOfficeHours |
20 |
|
Demo_InternalUser |
20 |
|
|
Demo_KnownDevice |
20 |
|
|
Demo_PayrollSiteCookie |
20 |
|
|
Demo_UserProfile |
20 |
Table 4-13 Sample Risk Policy Configuration: Risk Scores and Risk Levels
|
Risk Score |
Risk Level |
Action |
|---|---|---|
|
Less than 30 |
Low |
Allow access |
|
Between 30 to 60 |
Medium |
Authenticate with class Trust Levels |
|
Greater than 60 |
High |
Deny access |
Now, open the risk policy for which you want to emulate total risk score, risk level, and action in event of rule failure. In the risk policy page, click Actions > Toggle Validate. Specify the rules as pass or fail to see the result along with a graphical reperesentation.
For example, specify pass and fail for rules as follows:
|
Rule |
Condition |
|---|---|
|
Demo_InNetworkAtOfficeHours |
Failed |
|
Demo_InternalUser |
Failed |
|
Demo_KnownDevice |
Failed |
|
Demo_PayrollSiteCookie |
Passed |
|
Demo_UserProfile |
Passed |
In this case, the validation result is as follows:
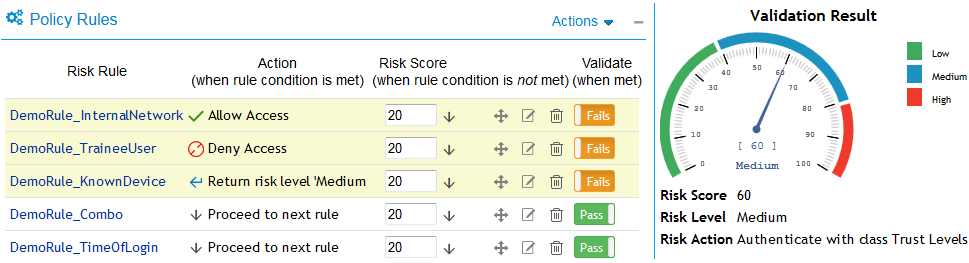
You can similarly specify any other rule as failed or passed to emulate the risk score and risk levels.
Understanding How To Use the Risk Rule Validation Utility To Troubleshoot Rule Configuration
After configuring a risk policy, you can use the Risk Rule Validation utility to evaluate the configuration of rules. This helps you understand how rules are evaluated in a risk policy.
During rule evaluation if there is a match with the values configured for the rules, the rule evaluation is successful. If no match is found, the rule evaluation fails.
Using the Risk Rule Validation Utility to Test Risk Configuration
To use the risk rule validation utility for testing risk configuration, perform the following steps:
-
In the browser address bar, type the following URL:
https://<identity-server-base-url>:port/nidp/test/risk
For example: https://10.1.1.1:8443/nidp/test/risk
-
Specify the credentials to log in.
-
Select a risk policy for evaluation. Click Submit. The risk score, risk category evaluation results and HTTP request header and related information are displayed.
-
[Optional] If you have logged in with administrator privileges, click Details to view details about risk configuration.
NOTE:The Risk Rule Validation utility does not display details if Record User History is enabled and a user profile rule is configured.
Troubleshooting Rule Evaluation Details By Using the Log File
If you encounter any error during risk-based authentication, check the log files to review the error code. The log file location is:
Linux: /opt/novell/nam/idp/logs/catalina.out
Windows: \Program Files\Novell\Tomcat\logs\stdout.log
Ensure that you have enabled logging at the application level. For more information, see Enabling Logging for Risk-Based Authentication.
By using the following rules as examples, let us try to understand how to use the details in the catalina.out file and how rules are evaluated:
|
Rule |
Risk Score |
|---|---|
|
User Profile |
30 |
|
IP Address |
25 |
|
HTTP Header |
20 |
The following are possible scenarios:
Scenario 1: User Profile Rule Fails
In this scenario, the User Profile rule fails to evaluate successfully. All other rules in the risk policy evaluate successfully.
The following tracelist detail from the catalina.out file provides information about rule evaluation, risk score, and action:
Figure 4-20 Tracelist providing information about rule evaluation

Table 4-14 Description of details recorded in the catalina.out file
|
Entry |
Description |
|---|---|
|
user-profile~result~false |
Indicates that user profile rule failed and the risk score of 30 is added to the total risk score. |
|
http-header~result~true |
Indicates that the HTTP header rule evaluated successfully. |
|
ip-rule~result~true |
Indicates that the IP address rule evaluated successfully. |
Figure 4-21 Tracelist providing information about risk level and action

This log entry indicates that the as per the risk level/action configuration, the action taken is to allow authentication to the user and the risk score is 30.
Scenario 2: User Profile Rule Evaluates Successfully
In this scenario, the User Profile rule evaluates successfully. As this rule is a configured to exit when the condition is met, all other rules in the risk policy are not considered for evaluation.
The following tracelist detail from catalina.out file provides more information about the rule evaluation, risk score, and action:
Figure 4-22 Tracelist providing information about rule evaluation
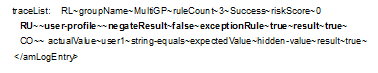
Table 4-15 Description of details recorded in the catalina.out file
|
Entry |
Description |
|---|---|
|
user-profile~result~true |
Indicates that user profile rule evaluated successfully. |
Figure 4-23 Tracelist providing information about risk level and action

This log entry indicates that the as per the risk level/action configuration, the action taken is to allow authentication to the user and the risk score is 0.
Scenario 3: Two rules fail and the user is asked to authenticate using additional authentication
In this scenario, the User Profile rule and the IP address rule fail to evaluate successfully. The HTTP Header rule evaluates successfully.
The following tracelist detail from the catalina.out file provides more information about the rule evaluation, risk score, and action:
Figure 4-24 Tracelist providing information about rule evaluation
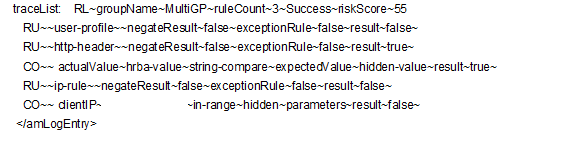
Table 4-16 Description of details recorded in the catalina.out file
|
Entry |
Description |
|---|---|
|
user-profile~result~false |
Indicates that user profile rule failed and the risk score of 30 is added to the total risk score. |
|
http-header~result~true |
Indicates that the HTTP header rule evaluated successfully. |
|
ip-rule~result~false |
Indicates that the IP address rule failed and the risk score of 25 is added to the total risk score. |
Figure 4-25 Tracelist providing information about risk level and action

This log entry indicates that the as per the risk level/action configuration, the action taken is additional authentication and the risk score is 55.
Scenario 4: All Rules Fail
In this scenario, all rules fail to evaluate successfully.
The following tracelist detail from the catalina.out file provides more information about the rule evaluation, risk score, and action:
Figure 4-26 Tracelist providing information about rule evaluation
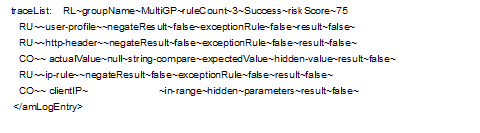
Table 4-17 Description of details recorded in the catalina.out file
|
Entry |
Description |
|---|---|
|
user-profile~result~false |
Indicates that user profile rule failed and the risk score of 30 is added to the total risk score. |
|
http-header~result~false |
Indicates that the HTTP header rule failed and the risk score of 20 is added to the total risk score. |
|
ip-rule~result~false |
Indicates that the IP address rule failed and the risk score of 25 is added to the total risk score. |
Figure 4-27 Tracelist providing information about risk level and action

This log entry indicates that as per the risk level/action configuration, the action is to deny access to the user and the risk score is 75.