1.1 Protecting Access Manager through Firewall
Access Manager should be used with firewalls. Figure 1-1 illustrates a simple firewall setup for a basic Access Manager configuration of Identity Server, Access Gateway, Analytics Server, and Administration Console.
Figure 1-1 Access Manager Components between Firewalls
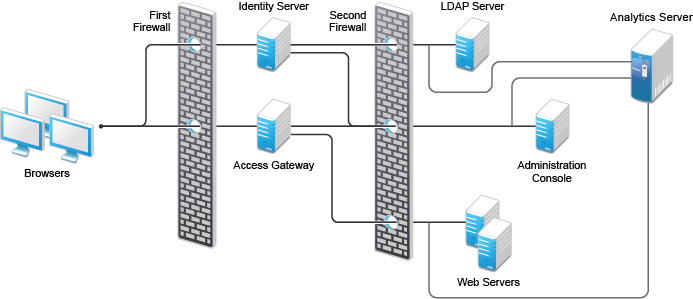
1.1.1 Access Gateway and Identity Server in DMZ
First Firewall: If you place a firewall between browsers and Access Gateway and Identity Server, you need to open ports so that browsers can communicate with Access Gateway and Identity Server and Identity Server can communicate with other identity providers.
For information about ports required to open in the first firewall, see First Firewall
in the NetIQ Access Manager 4.3 Installation and Upgrade Guide.
Second Firewall: The second firewall separates web servers, LDAP servers, Analytics Server, and Administration Console from Identity Server and Access Gateway.
For information about ports required to open in the second firewall, see Second Firewall
in the NetIQ Access Manager 4.3 Installation and Upgrade Guide.
1.1.2 A Firewall Separating Access Manager Components from LDAP Servers
You can configure your Access Manager components so that Administration Console is on the same side of the firewall as other Access Manager components and have a firewall between them and LDAP servers.
Figure 1-2 A Firewall Separating Administration Console and the LDAP Server
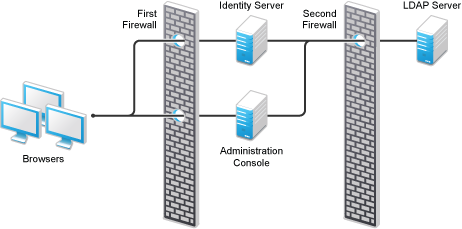
In this configuration, you need to open the required ports in the second firewall for Administration Console and Identity Server.
For information about all required ports, see Required Ports
in the NetIQ Access Manager 4.3 Installation and Upgrade Guide.