1.1 How Access Manager Solves Business Challenges
As networks expand to connect people and businesses throughout the world, secure access to business resources becomes increasingly important and more complex. Today, employees work from corporate, home, and mobile offices using mobile devices. Besides employees, customers and partners also require access to resources on your network, and your employees require access to resources on partners’ networks or at service providers.
Access Manager lets you provide employees, customers, and partners with secure access to your network resources using any type of device. Access Manager helps you if your business faces any of the following access-related challenges:
-
Protecting resources so that only authorized users can access them whether those users are employees, customers, or partners.
-
Ensuring that the users who are authorized to use a resource can access that resource regardless of users’ location or type of device they use.
-
Requiring users to manage multiple passwords for authentication to web applications.
-
Ensuring that users have access only to the resources required for their jobs.
-
Revoking network access from users faster.
-
Protecting users’ privacy and confidential information as they access company resources or partners’ resources.
-
Proving compliance with your business policies, privacy laws such as Sarbanes-Oxley, HIPAA, or European Union, and other regulatory requirements.
-
Providing facility to access protected resources by using token-based protocols.
-
Providing facility to use your existing credentials to access services from different service providers such as Office 365 and Salesforce.
The following sections expand on these challenges and introduce the solutions provided by Access Manager.
1.1.1 Protecting Resources While Providing Access
The primary purpose of Access Manager is to protect resources by allowing access only to users you have authorized. As shown in the following illustration, those users who are authorized to use the protected resources, are allowed access, while unauthorized users are denied access.
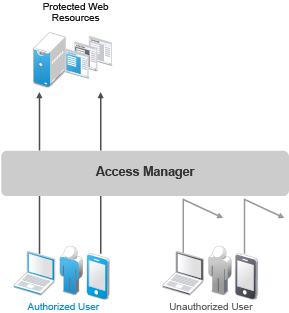
Access Manager secures your web resources from Internet hackers. Addresses of the servers that host the protected resources are hidden from both external and internal users. The only way to access the resources is by logging in to Access Manager with authorized credentials, no matter what device you use.
Access Manager protects only the resources you have set up as protected resources. It is not a firewall and should always be used in conjunction with a firewall product.
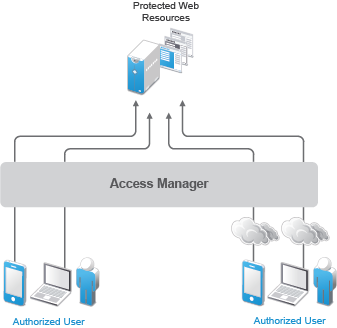
Access to resources is independent of a user’s location, as shown in the following illustration. Access Manager provides the same secure access and same experience whether the user is accessing resources from your local office, from home, or from any other place with any type of device.
1.1.2 Managing Passwords with Single Sign-On
Authentication through Access Manager not only establishes authorization to applications (see Protecting Resources While Providing Access), but it can also provide authorization to those same applications. With Access Manager serving as the front-end authentication, you can deploy standards-based web single sign-on. With single sign-on, your employees, partners, and customers only need to remember one password or login routine to access all corporate and web-based applications they are authorized to use. That means fewer help desk calls and the reduced likelihood of users resorting to vulnerable written reminders.
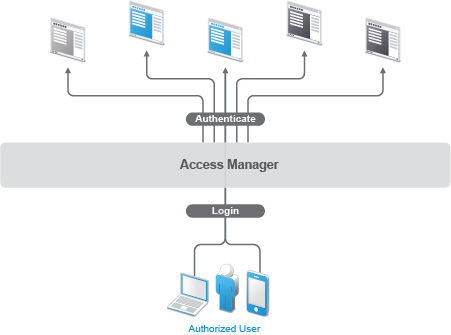
By simplifying the use and management of passwords, Access Manager helps you enhance users' experience, increase security, streamline business processes, and reduce system administration and support costs.
1.1.3 Enforcing Business Policies
Determining the access policies for an organization is often complicated and difficult, but the difficulty pales in comparison to enforcing the policies. Your IT personnel can spend hours attempting to give users the correct access to resources, and hours more retracing their steps to see why authorized users cannot access resources. You might never know about the situations where users access resources they should not be accessing.
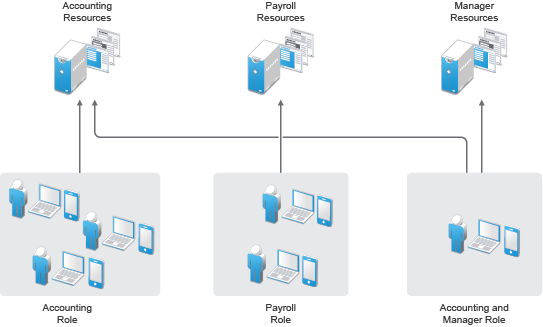
Access Manager automates the granting and revoking of access through the use of roles and policies. As shown in the following illustration, users are assigned to roles that have access policies associated with them. Each time a user authenticates through Access Manager, the user’s access is determined by the policies associated with the user’s roles.

In the following example, users assigned to the Accounting role receive access to the Accounting resources, Payroll users receive access to the Payroll resources, and Accounting managers receive access to both the Accounting and Manager resources.
Because access is based on roles, you can grant access in minutes and be certain that the access is consistent with your business policies. You can revoke access in minutes by removing role assignments from users.
For security-minded organizations, it comes down to this simple fact: you set the policies by which users gain access, and Access Manager enforces them consistently and quickly. There are no surprises and no delays.
You can also securely grant access to user’s private resources such as web applications, mobile phones, handheld devices, and desktop using access tokens.
1.1.4 Sharing Identity Information
In today’s business environment, few organizations stand alone. More than likely, you have trusted business partners with whom you need to share resources in a secure manner. Or, you have business services, such as a 401k management system, to which you need to provide employee access. Or, maybe your organization is the one providing services to another business. Access Manager provides federated identity management to enable users to seamlessly and securely authenticate across autonomous identity domains.
For example, assume that you have employees who need access to your corporate applications, several business partners’ applications, and their 401k service, as shown in the following figure:
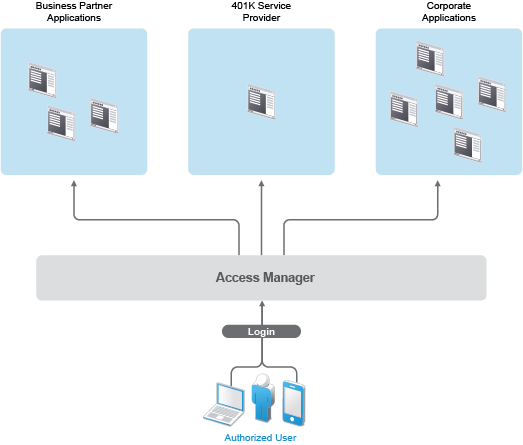
Each identity domain (your organization, your partner’s organization, and 401k service) requires an account and authentication to that account to access the resources. However, because you have used Access Manager to establish a trust relationship with the business partner and the 401k service, your employees can log in through Access Manager to gain access to the authorized resources in all three identity domains.
Access Manager enables your employees to access resources from business partners and service providers. It also lets business partners access authorized resources on your network. The following figure illustrates this type of access.
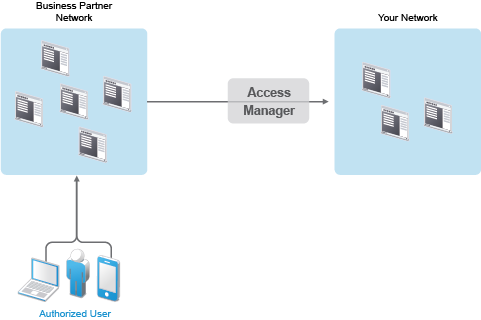
In addition to simply linking user accounts in different identity domains, Access Manager also supports federated provisioning, which means that new user accounts can be automatically created in your trusted partner’s (or provider’s) system. For example, a new employee in your organization can initiate the creation of an account in your business partner’s system through Access Manager rather than relying on the business partner to provide the account. Customers or trusted business partners can automatically create accounts in your system.
Access Manager leverages identity federation standards including Liberty Alliance, WS-Federation, WS-Trust, and SAML. It also provides a facility to identify risk associated with login attempts, mitigate the risk and take action based on risk severity.This foundation minimizes—or even eliminates—interoperability issues among external partners or internal workgroups. In fact, Access Manager features an identical configuration process for all federation partners whether they are different departments within your organization or external business partners.
1.1.5 Protecting Identity Information
Whenever you exchange identity information with other businesses or service providers, you must be concerned with protecting the privacy of your employees, customers, and partners. It is an integral part of trusted business partnerships and regulatory compliance: the ability to establish policies on the exchange of identity information.
Access Manager enables you to determine which business and personal information from your corporate directory to share with others. As shown in the following illustration, you can choose to share only the information required to establish the account at the service provider or trusted partner:
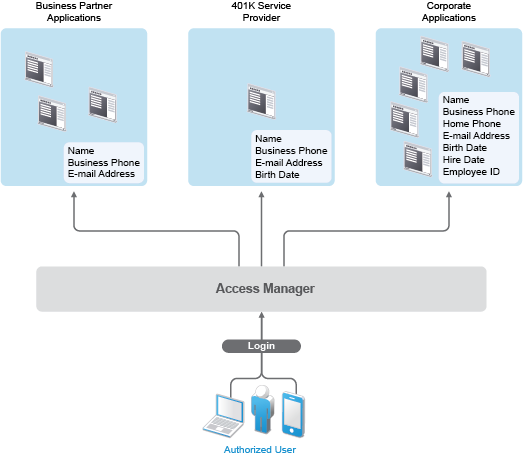
Access Manager offers this built-in privacy protection for your employees, partners, and customers alike, wherever they are working. With Access Manager in place, your organization can guarantee user confidentiality. For federated provisioning, Access Manager adheres to those same policies and protections.
1.1.6 Complying with Regulations
Regulations can be a hassle, but an agile, automated IT infrastructure substantially cuts costs and reduces the pain of compliance. By implementing access based on user identities, you can protect users’ privacy and confidential information. At the same time, you can reduce the amount of paperwork needed to prove that proper access control measures are in place. Compliance assurance and documentation is an inherent benefit of Access Manager.
Specifically, Access Manager helps you stay in compliance with Sarbanes-Oxley, HIPAA, European Union privacy laws, and other regulatory requirements. For an internal assessment or an external auditor, Access Manager can generate the reports you need, turning compliance requirements into opportunities to develop and implement processes that improve your business practices.