1.7 Protecting an Identity Server Through the Access Gateway
For security reasons, you might want to set up your Access Manager configuration so that the Identity Server is a resource protected by an Access Gateway. This configuration reduces the number of ports you need to open between the outside world and your network. Figure 1-10 illustrates such a configuration.
Figure 1-10 Identity Servers behind an Access Gateway
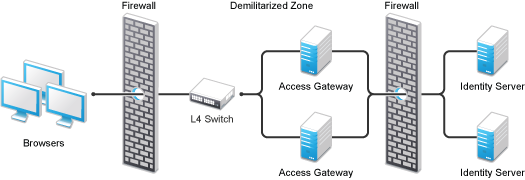
With this configuration, you need an L4 switch to cluster the Access Gateways. However, you do not need an L4 switch to cluster the Identity Servers. When the Identity Server is configured to be a protected resource of the Access Gateway, the Access Gateway uses its Web server communication channel. Each Identity Server in the cluster must be added to the Web server list, and the Access Gateway uses its Web server load balancing and failover policies for the clustered Identity Servers.
Limitations: The following features are not supported with this configuration:
-
The Identity Server cannot respond to Identity Provider introductions.
-
Federation to an external service provider that requires the artifact profile with SOAP/Mutual SSL binding cannot be supported with this configuration.
-
The proxy service that is protecting the Identity Server cannot be configured to use mutual SSL. For example with this configuration, X.509 authentication cannot be used for any proxy service. To perform X.509 authentication (which is a form of mutual SSL), a user's browser must have direct access to the Identity Server.
-
The proxy service that is protecting the Identity Server cannot be configured to use NMAS.
For configuration details, see Configuring a Protected Identity Server Through Access Gateways in the NetIQ Access Manager 4.2 Administration Guide .