Environment
NetIQ eDirectory 9.0
NetIQ iManager 3.0
Situation
By default a new installation of eDirectory 9 will have FIPS mode enabled as well as a RSA certificate associated with the LDAP server object. High ciphers are also set which allows all high cipher RSA clients to connect. This will disable SSLv3 and allow only TLS 1.0, 1.1 and 1.2 clients to connect.
Resolution
If it is desired to only allow TLS 1.2 based LDAP clients to connect the following conditions apply:
A. FIPS mode needs to be enabled.
B. The LDAP server must use an EC (Elliptical Curve) based certificate.
C. The LDAP bind restriction value must be set to use a Suite B cipher. It can be any of the three Suite B choices: 128, 128 only and 192.
If more detail or background is required please refer to the following:
https://www.netiq.com/documentation/edirectory-9/edir_admin/data/agq8auc.html#bn5n9ae
NOTE: As a workaround, the ldapSSLConfig attribute is available from eDirectory 9.0 SP2 onwards. This allow configuring TLS 1.2 without implementing EBA and Suite B in the environment.
In eDirectory 9.0 this was a manual process of editing attributes on the LDAP group or server object. In 9.2 and using the latest plugins for iManager 3.2 there is a check box for only allowing TLS 1.2 as shown below.
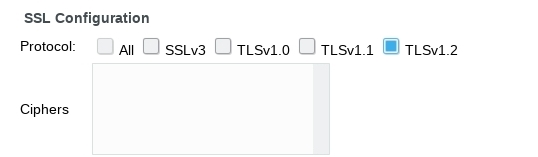
The following steps will accomplish this.
1. Ensure FIPS mode is set.
- Linux: ensure the line n4u.server.fips_tls=1 is in the /etc/opt/novell/eDirectory/conf/nds.conf
- Windows: Navigate to the HKLM\SOFTWARE\Novell\NDS\FipsMode registry value. To enable FIPS mode set this value to 1.
Once this is changed ndsd will need to be restarted.
2. Using iManager 3.0 configure the eDirectory 9.0 LDAP server to use an EC certificate. Go to LDAP - LDAP Options - View LDAP Servers tab. Select the 9.0 server then click on the Connections tab.
Before modifying the LDAP server object's certificate (default setting):
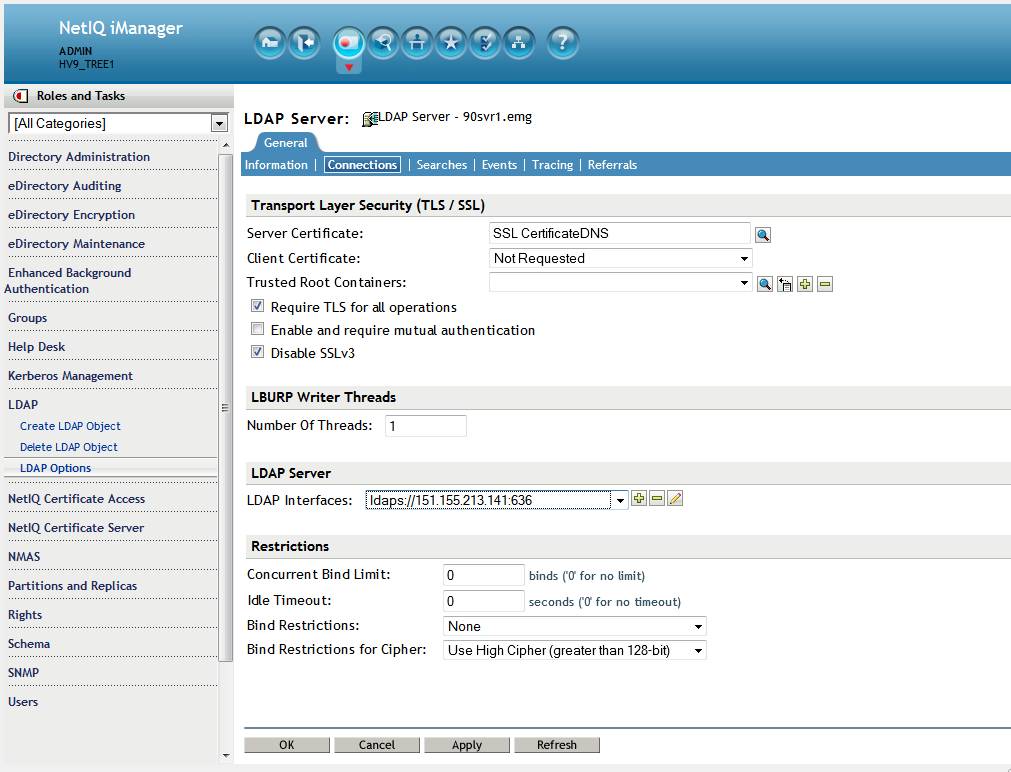
The server is using a RSA based certificate with high ciphers set.
After changing the LDAP server object's certificate to one that is EC based.
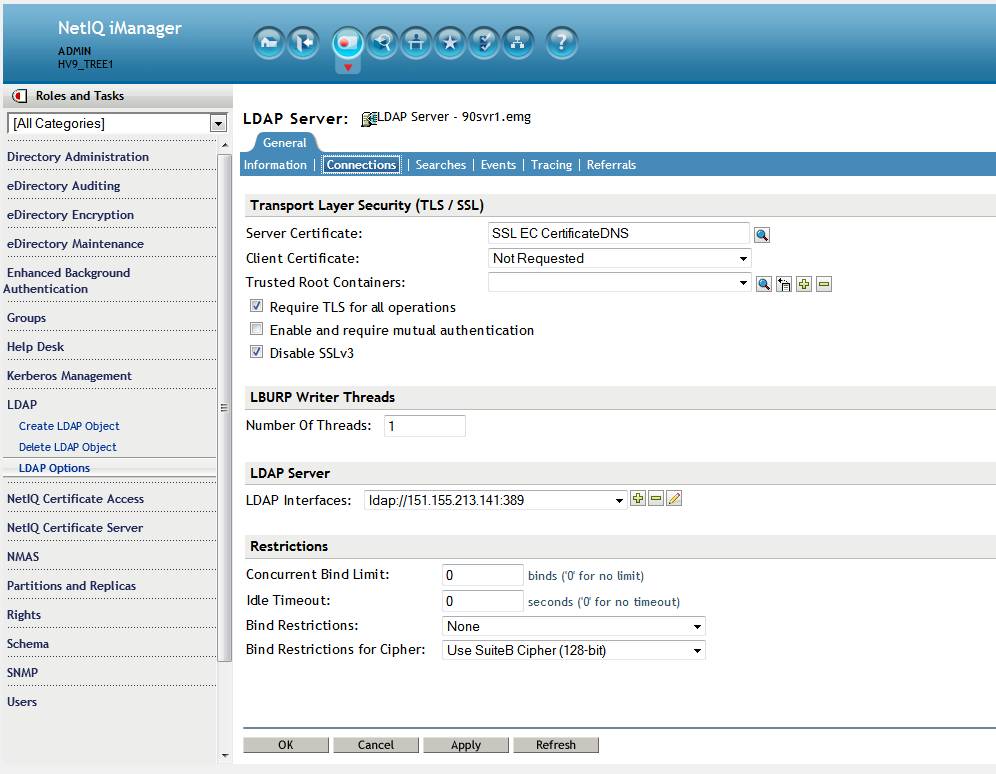
Two changes were made:
- Server Certificate: browse for and select the SSL EC CertificateDNS certificate.
- Bind Restrictions for Cipher - choose a minimum of Use SuiteB Cipher 128-bit.
It is not required to check the Disable SSLv3 box. This is turned off by default in FIPS mode. Once these changes are made and saved the LDAP server needs to be restarted.
[ndstrace -c "unload nldap]
[ndstrace -c "load nldap]
From a client running a newer version of OpenSSL the new TLS restriction can be tested:
TLS 1.0
- openssl s_client -connect 151.155.213.141:636 -tls1
Negotiation is unsupported.
TLS 1.1
- openssl s_client -connect 151.155.213.141:636 -tls1_1
Negotiation is unsupported.
TLS 1.2
- openssl s_client -connect 151.155.213.141:636 -tls1_2
Connects and certificate is returned.
openssl s_client -connect 151.155.213.141:636 -tls1_2
CONNECTED(00000003)
depth=1 OU = Organizational CA, O = HV9_TREE1
verify error:num=19:self signed certificate in certificate chain
verify return:0
---
Certificate chain
0 s:/O=HV9_TREE1/CN=hvaughan10.lab.novell.com
i:/OU=Organizational CA/O=HV9_TREE1
1 s:/OU=Organizational CA/O=HV9_TREE1
i:/OU=Organizational CA/O=HV9_TREE1
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFnjCCBSKgAwIBAgIkAhwR/6b92GzQXz2n4Bx2Xf29t19l2iWLil2CroeLAgIl
D6f9MAwGCCqGSM49BAMDBQAwMDEaMBgGA1UECxMRT3JnYW5pemF0aW9uYWwgQ0Ex
EjAQBgNVBAoUCUhWOV9UUkVFMTAeFw0xNjAyMDEyMjEyMDZaFw0xODAxMzEyMjEy
MDZaMDgxEjAQBgNVBAoUCUhWOV9UUkVFMTEiMCAGA1UEAxMZaHZhdWdoYW4xMC5s
YWIubm92ZWxsLmNvbTB2MBAGByqGSM49AgEGBSuBBAAiA2IABEbdnjNQClSyeg/6
N+PknVgqf33V0vW/7tB2QJ/uZ0ePNujVTmxsQ6dArBrCCZnbcIt6K8Xw3wFN7AoF
UDr5g8RFBfYWcutGmatr/0LLk2e9A1GMP49NZXMb/xRqGjUw76OCA+EwggPdMB0G
A1UdDgQWBBRJ45LhV61p2Ii7N7vGUGAacVOWDzAfBgNVHSMEGDAWgBQhqGG5iB4T
3NdZ2SH9jyU5jfgPOjAPBgNVHREECDAGhwSXm9WNMAsGA1UdDwQEAwIFoDCCAcwG
C2CGSAGG+DcBCQQBBIIBuzCCAbcEAgEAAQH/Ex1Ob3ZlbGwgU2VjdXJpdHkgQXR0
cmlidXRlKHRtKRZDaHR0cDovL2RldmVsb3Blci5ub3ZlbGwuY29tL3JlcG9zaXRv
cnkvYXR0cmlidXRlcy9jZXJ0YXR0cnNfdjEwLmh0bTCCAUigGgEBADAIMAYCAQEC
AUYwCDAGAgEBAgEKAgFpoRoBAQAwCDAGAgEBAgEAMAgwBgIBAQIBAAIBAKIGAgEX
AQH/o4IBBKBYAgECAgIA/wIBAAMNAIAAAAAAAAAAAAAAAAMJAIAAAAAAAAAAMBgw
EAIBAAIIf/////////8BAQACBAbw30gwGDAQAgEAAgh//////////wEBAAIEBvDf
SKFYAgECAgIA/wIBAAMNAEAAAAAAAAAAAAAAAAMJAEAAAAAAAAAAMBgwEAIBAAII
f/////////8BAQACBBH/pv0wGDAQAgEAAgh//////////wEBAAIEEf+m/aJOMEwC
AQICAQACAgD/Aw0AgAAAAAAAAAAAAAAAAwkAgAAAAAAAAAAwEjAQAgEAAgh/////
/////wEBADASMBACAQACCH//////////AQEAMIIBqwYDVR0fBIIBojCCAZ4wL6At
oCuGKWh0dHA6Ly8xNTEuMTU1LjIxMy4xNDE6ODAyOC9jcmwvb25lZWMuY3JsMGig
ZqBkhmJsZGFwOi8vMTUxLjE1NS4yMTMuMTQxOjM4OS9DTj1PbmVFQyxDTj1PbmUl
MjAtJTIwQ29uZmlndXJhdGlvbiUyMEVDLENOPUNSTCUyMENvbnRhaW5lcixDTj1T
ZWN1cml0eTAwoC6gLIYqaHR0cHM6Ly8xNTEuMTU1LjIxMy4xNDE6ODAzMC9jcmwv
b25lZWMuY3JsMGmgZ6BlhmNsZGFwczovLzE1MS4xNTUuMjEzLjE0MTo2MzYvQ049
T25lRUMsQ049T25lJTIwLSUyMENvbmZpZ3VyYXRpb24lMjBFQyxDTj1DUkwlMjBD
b250YWluZXIsQ049U2VjdXJpdHkwZKBioGCkXjBcMQ4wDAYDVQQDEwVPbmVFQzEf
MB0GA1UEAxMWT25lIC0gQ29uZmlndXJhdGlvbiBFQzEWMBQGA1UEAxMNQ1JMIENv
bnRhaW5lcjERMA8GA1UEAxMIU2VjdXJpdHkwDAYIKoZIzj0EAwMFAANoADBlAjAp
kq6S4Ipsd4SBF1OEreWcgxo+yPb5jV54bDHdq/H7AiE/xR/mORfP03LHIO2eGlIC
MQCW9CCNFAh8McgYTF6xEau7yo+6wqjWoQQw3rTCi/Dp1O6p727inwfLGvqASVWX
cHs=
-----END CERTIFICATE-----
subject=/O=HV9_TREE1/CN=hvaughan10.lab.novell.com
issuer=/OU=Organizational CA/O=HV9_TREE1
---
No client certificate CA names sent
---
SSL handshake has read 3000 bytes and written 419 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-ECDSA-AES256-GCM-SHA384
Server public key is 384 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-ECDSA-AES256-GCM-SHA384
Session-ID: 48BDEB6D31F5A165554F48CB002888FF2F046BD25487BE641D4C758B9C8D9D3D
Session-ID-ctx:
Master-Key: 2199C947009CE180F2457D238D941B55A51A6C6A06DE121FA4B5C86B703AAFD0E8858D8AC5974D099C0D38E43031EF2F
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - d8 47 bb 35 eb dc 51 0d-61 bd d8 08 39 4f 01 1c .G.5..Q.a...9O..
0010 - 9d 9f bd a5 77 59 b5 5b-c6 45 3e e8 c7 c2 92 4d ....wY.[.E>....M
0020 - 78 85 a7 94 7a 1d 36 51-9e 01 21 70 2a ae 64 11 x...z.6Q..!p*.d.
0030 - 53 c1 3a 84 bd 74 46 2e-e7 f8 a3 32 91 80 2e 47 S.:..tF....2...G
0040 - 78 53 de f9 0d 3f 33 4b-af 4e e2 2b 57 40 dd f7 xS...?3K.N.+W@..
0050 - 65 43 43 20 cd 58 cc 3a-a3 e0 f5 52 c8 d8 17 e9 eCC .X.:...R....
0060 - 1f 18 8b d0 f4 b4 19 8e-a7 8d 5c 53 2e 8d 5b 55 ..........\S..[U
0070 - 1a 8c ef 18 56 20 b0 f5-52 48 91 e7 63 d1 b8 b2 ....V ..RH..c...
0080 - e1 44 1a 89 8c 84 a1 7a-42 08 15 12 9c 52 2a e6 .D.....zB....R*.
0090 - 1c 85 04 d8 74 e3 6c 97-b5 38 3c 49 be f7 99 79 ....t.l..8<I...y
00a0 - e0 5b b9 e7 52 a7 d0 9c-9e d7 95 f9 21 ba ba ca .[..R.......!...
Start Time: 1464278708
Timeout : 7200 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
---
05/22/2019 - James Swallow: Added "Note" for ldapSSLConfig attribute and link to documentation