Environment
Novell GroupWise 2012
Novell GroupWise 8
Novell GroupWise 2014.x
Novell GroupWise 8
Novell GroupWise 2014.x
Situation
How to configure LDAP certificates for a GroupWise system using LDAP authentication.
How to validate LDAP certificates for a GroupWise POA.
How to export the Trusted Root Certificate.
How to configure the GroupWise system to use the valid trusted root certificate.
Users unable to authenticate to GroupWise POA.
Some users can't login to GroupWise Client.
How to validate LDAP certificates for a GroupWise POA.
How to export the Trusted Root Certificate.
How to configure the GroupWise system to use the valid trusted root certificate.
Users unable to authenticate to GroupWise POA.
Some users can't login to GroupWise Client.
Resolution
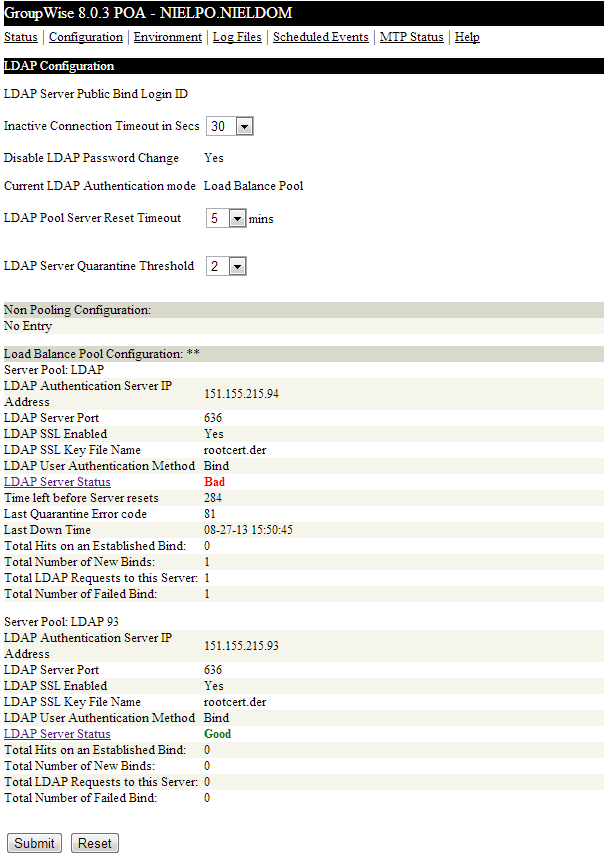
- Validate the certificates used for the GroupWise Post Office Agent (POA).
- From the GroupWise POA WebConsole - select Configuration | LDAP Authentication.
- The LDAP Server Status will appear as Starting until a user attempts to login to that LDAP server.
- The LDAP Server Status will then switch to either Good or Bad.
Note: If Bad, the certificate is invalid or expired and needs to be reimported/replaced. See the subsequent steps.
- From the GroupWise POA WebConsole - select Configuration | LDAP Authentication.
- Export the Trusted Root Certificate.
- Using iManager:
- Login to iManager as admin | Roles & Tasks | Novell Certificate Server | Configure Certificate Authority
- Select Next to skip pass the CRL configuration.
- Select Certificates | Check the Self Signed Certificate | Select Validate
- If the Certificate is invalid, see the steps provided from TID 7013047 to recreate the expired CA.
If the Certificate status is valid, then check the certificate again and select Export. - Uncheck Export private key. Verify Export format is DER.
- Select Next. Save the exported certificate to the GroupWise server(s).
- Using ConsoleOne: see Trusted Root Certificates and LDAP Authentication.
- Configure the GroupWise System to use the valid trusted root certificate.
For GroupWise 2014.x: see Setting Up an LDAP Directory
For GroupWise 2012 and older: Please see documentation for Providing LDAP Authentication for GroupWise Users- Information regarding LDAP Server Configuration is provided in documentation in great detail.
Note: If the LDAP server requires an SSL connection, select Use SSL, then browse to and select the trusted root certificate of the LDAP server. If you do not specify a full path, the POA looks in the following locations for the trusted root certificate:
- Information regarding LDAP Server Configuration is provided in documentation in great detail.
- Linux: /opt/novell/groupwise/agents/bin
- Windows: POA installation directory
- Restart the GroupWise POA(s).
Cause
Expired or invalid LDAP certificates prevent GroupWise POA from authenticating users.