An online cyberthreat experience
Build a reusable set of access management services (Access Security Layer) for both your new and existing applications.
Raise the security level and provide a user-friendly experience.
Retain and attract new customers with agile responsiveness.
Enforce adaptive, purpose-based access controls.
Simplified access experience for any mix of users in any location, using any technologies.
Deliver continuous authentication to protected resources and adapt verification to the current risk.
Create a seamless, secure user experience from a complex amalgamation of resources and processes.
Master the challenge of effective and consistent application of security policies across a wide variety of resources.
Set your brand apart with the superior customer experience and capabilities of your digital application interactions.
Leverage and simultaneously protect personal data across legacy, cloud-based, mobile, and consumer-facing applications.
A single bad actor can wreak havoc by stealing intellectual property and deleting admin accounts and protected records.
Vulnerabilities in today’s multi-cloud, multi-device environment are a bonanza for hackers seeking protected customer data.
Scalability to deliver great experiences requires data residing in your organization and in remote locations.
Provides SSO user experience through a centralized policy engine for SAML, OAuth, OpenID Connect, WS-Federation, and others.
Extend your infrastructure via out-of-the-box integration with Microsoft SharePoint and Office 365 Enterprise.
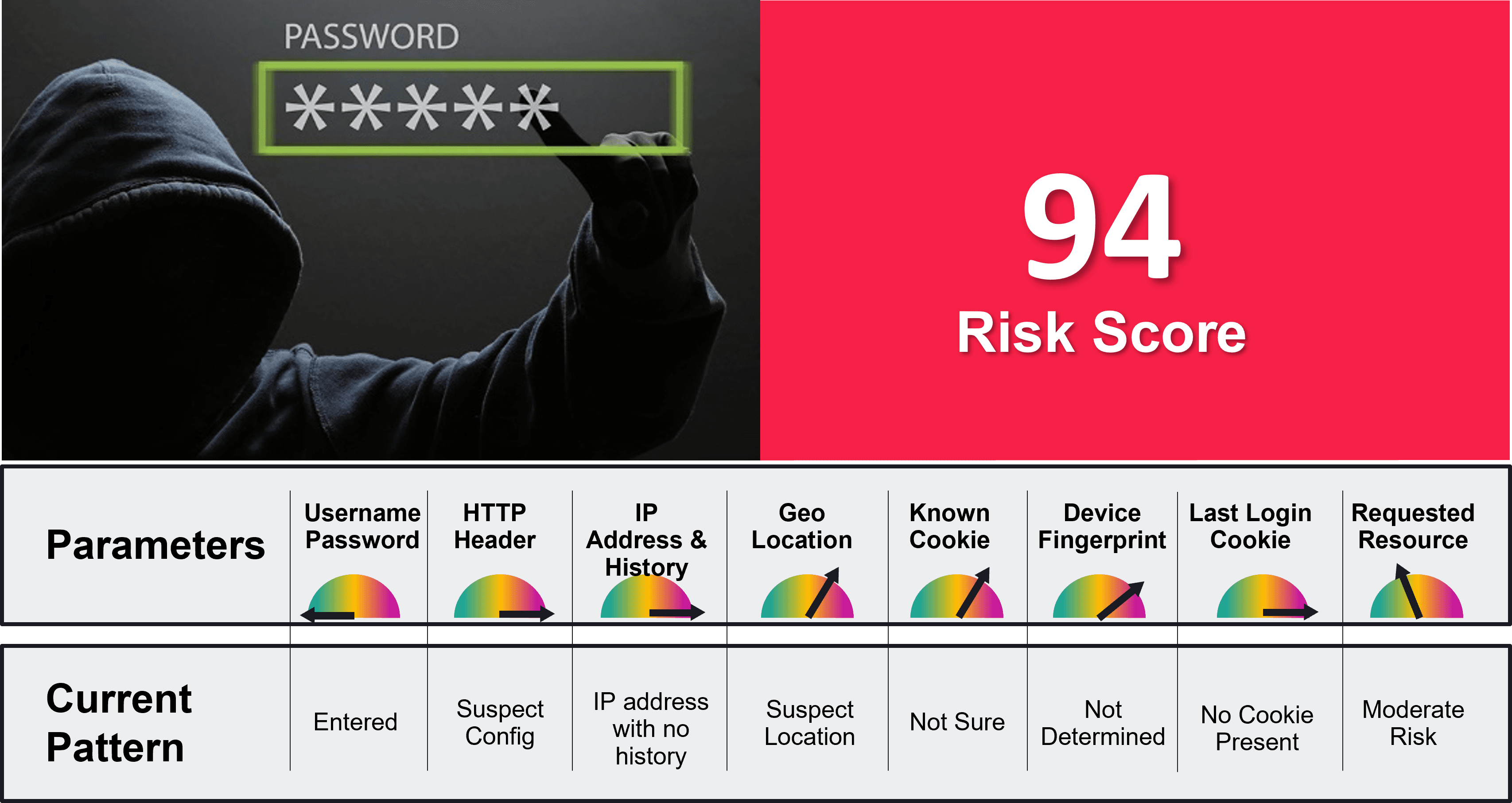
A built-in, risk-based authentication engine provides scoring and selective authentication based on threat level.
Gateway and portal for smartphone users who need access to legacy and third-party apps (mobile SDK for integrations).
Out-of-the-box integration with NetIQ Advanced Authentication offers a wide range of authentication methods.
A simple, single sign-on and access control experience for all your users, whether they are internal, contractors, mobile, or remote.
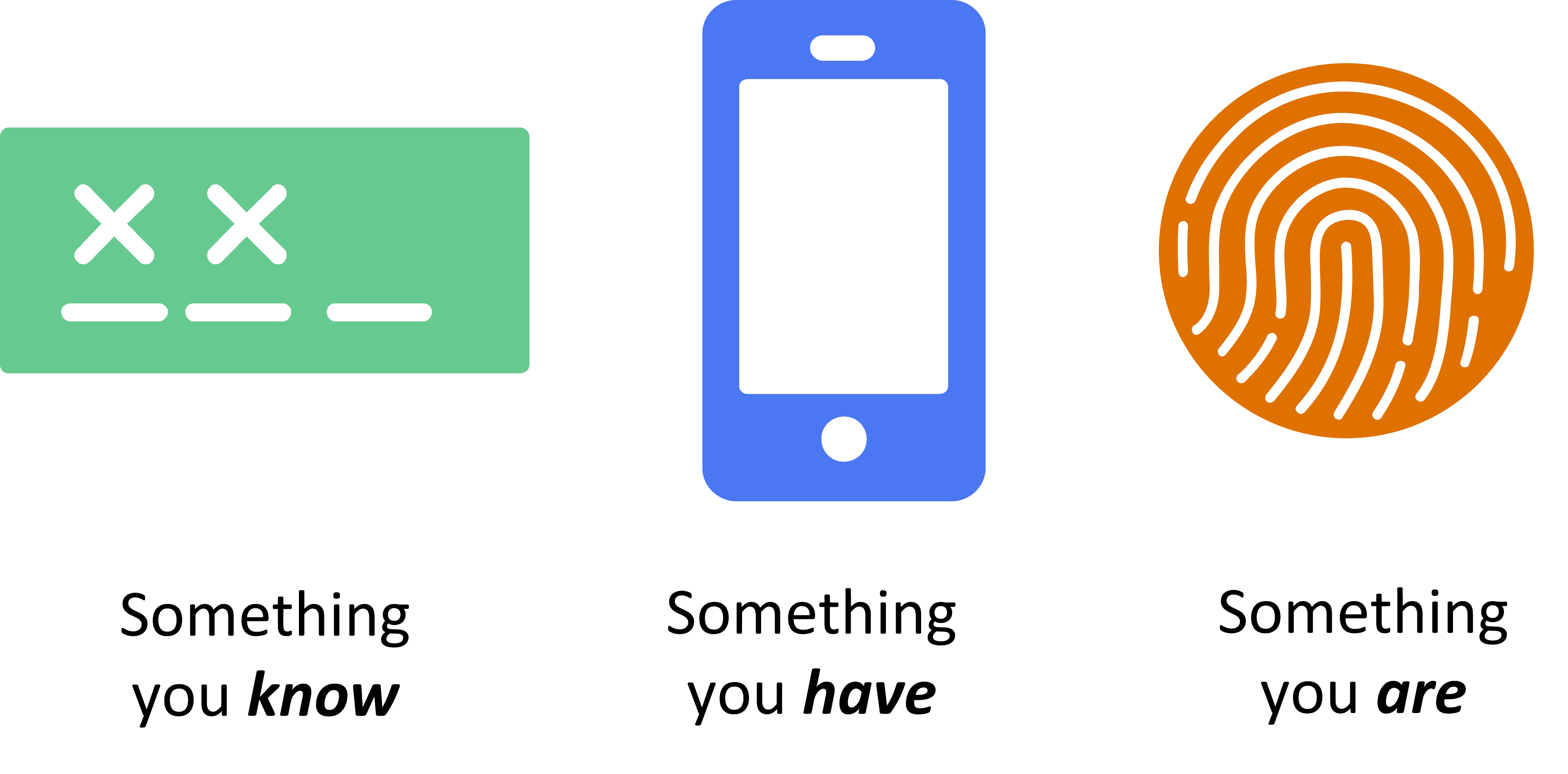
Move beyond username and passwords and securely protect data and applications.
Centralized management of elevated credentials using flexible, policy-based methods that enforce least privilege access.
Adapt the authentication and access experience to the risk at hand.
Administer and enforce strong credential policies and provide self-administration for end users.
A simple, single sign-on and access control experience for all your users, whether they are internal, contractors, mobile, or remote.
Move beyond username and passwords and securely protect data and applications.
Centralized management of elevated credentials using flexible, policy-based methods that enforce least privilege access.
Adapt the authentication and access experience to the risk at hand.
Administer and enforce strong credential policies and provide self-administration for end users.
Head of Section
Head of Systems
Sr. Manager, IT Risk, IAM