1.1 Challenges of Securing an IT Environment
Securing your IT environment is a challenge due to the complexity of your environment. There are many different applications, databases, mainframes, workstations, and servers that all have logs of events. You also have the security devices and network infrastructure devices that all contain logs of what is happening in your IT environment.
Figure 1-1 What Happens in Your Environment
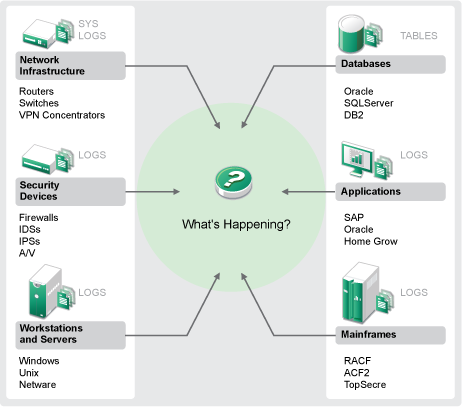
The challenges arise because of the following facts:
-
There are many devices in your IT environment.
-
The logs are in different formats.
-
The logs are stored in silos.
-
The amount of information generated in the logs.
-
You can’t determine who did what without manually analyzing all of the logs.
To make the information useful, you must be able to perform the following:
-
Collect the data.
-
Consolidate the data.
-
Normalize disparate data into events that you can easily compare.
-
Map events to standard regulations.
-
Analyze the data.
-
Compare events across multiple systems to determine if there are security issues.
-
Send notifications when the data is outside of the norms.
-
Take action on notifications to comply with business policies.
-
Generate reports to prove compliance.
After you understand the challenges of securing your IT environment, you need to determine how to secure the enterprise for and from users without treating them like malicious users, or burdening them to the point where it is impossible to be productive. Sentinel provides the solution.