3.6 Correlation Actions
The Action Manager allows you to configure repeatable Actions. There are several different types of Actions that can be configured and then associated with a correlation rule deployment:
-
Configure a Correlated Event
-
Add to Dynamic List
-
Remove from Dynamic List
-
Execute a Command
-
Send an Email
-
Create an Incident
-
Any Imported JavaScript Action Plugin that is marked by the plugin developer as requiring a Correlated Event as input
NOTE:Although all of these actions can be used in correlation rule deployments, only the JavaScript Actions can be used in other areas of the Sentinel Control Center. For more information, see Section 16.0, Actions and Integrator.
Actions associated with a Correlation Rule are executed when the deployed correlation rule fires (with the frequency of their execution determined by settings on the Update Criteria window of the Correlation Rule Wizard).
If no Action is specifically selected when deploying a correlation rule, a correlated event with the following default settings is created:
Table 3-3 Default Settings
|
Field Name |
Default Values |
|---|---|
|
Severity |
4 |
|
Event Name |
Final Event Name |
|
Message |
<message> |
|
Resource |
Correlation |
|
SubResource |
<Rule Name> |
3.6.1 Configure Correlated Event
Figure 3-2 Configure Correlated Event

NOTE:This type of action can only be used in Correlation deployments.
To override the default values for the correlated event created when a rule fires, an action can be created to populate the following fields in the correlated event:
-
Severity
-
Event Name
-
Message
-
Resource
-
SubResource
3.6.2 Add to Dynamic List
Figure 3-3 Adding to Dynamic List

NOTE:This type of action can only be used in Correlation deployments.
This action type can be used to add a constant value or the value of an event attribute (such as Target IP or Initiator User Name) to an existing Dynamic List. Any values that are repeated across multiple events are only be added to the dynamic list once. The various parameters available are:
Table 3-4 Parameters
If there are entries for both Element Values and Attribute Names, both are added to the Dynamic List when the rule fires. If the Element Value is filled in and the Element Type is Transient, the timestamp for the element in the Dynamic List is updated each time the rule fires.
3.6.3 Remove from Dynamic List
Figure 3-4 Removing from Dynamic List
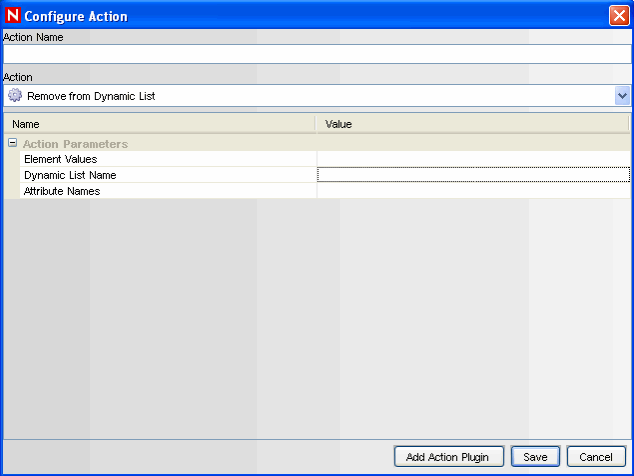
NOTE:This type of action can only be used in Correlation deployments
This action type can be used to add a constant value or the value of an event attribute (such as Target IP or Initiator User Name) from an existing Dynamic List. The various parameters available are:
Table 3-5 Parameters
3.6.4 Execute a Command
Figure 3-5 Executing a Command

NOTE:This type of action can only be used in Correlation deployments.
This action type can be used to execute a command when a correlated event triggers. You can set the following parameters:
-
Command
NOTE:For actions that execute a command or run a script, the command or script must reside in the $ESEC_HOME/config/exec or %ESEC_HOME%\config\exec folder on the Correlation Engine. Symbolic links on UNIX are not supported.
-
Arguments: This can include constants or references to an event attribute in the last event, the one that caused the rule to fire.
NOTE:References to event attributes must use the values in the metatag column enclosed in % or $ symbols. For example, %InitIP% represents the Initiator IP address value from the Correlated Event, except in the Configure Correlated Event action. Because the correlated event has not been created before the action is executed, the InitIP value comes from the trigger event. $InitIP$ always represents the value from the current event.Both %all% and $all$ are the same, and they pass information (a limited set of attributes from both the trigger event and the correlated event along with some correlation rule data) to a correlation action. They are provided primarily for backward compatibility with existing correlation actions. They cannot be used in JavaScript actions or in the Configure Correlated Event action. For more information on metatags, see
Sentinel Event Fields
in Sentinel 6.1 Reference Guide.
Command actions can be created to perform a non-interactive action, such as modifying a firewall policy, entering a record in a database, or deactivating a user account. For an action that generates output, such as a command to run a vulnerability scan, the command should refer to a script that runs the command and then writes the output to a file.
NOTE:By default, the action output is stored to the working directory, $ESEC_HOME/data. The action output can be written to a different directory by specifying a different storage location of the output file in the script
3.6.5 Create Incident
Figure 3-6 Configure Action- Create Incident
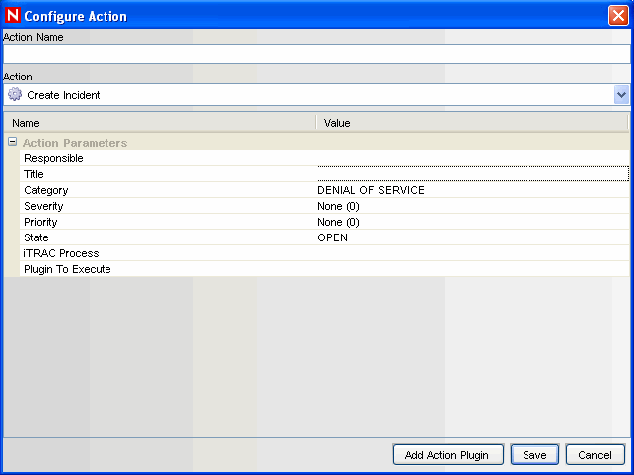
NOTE:This type of action can only be used in Correlation deployments
This action type create an incident whenever a correlated event fires. You can also initiate an iTRAC workflow process for remediation of that incident. For more information about the values of the following parameters, see Section 4.0, Incidents Tab.
-
Responsible
-
Title
-
Category
-
Severity
-
Priority
-
State
-
[Optional] iTRAC Process: dropdown of configured iTRAC processes
-
[Optional] Action Plugin to Execute: dropdown of configured JavaScript Actions
WARNING:Do not enable the Create Incident action until the correlation rule has been tuned. If the rule fires frequently, the system can create more incidents or initiate more iTRAC workflow processes than desired.
3.6.6 Send Email
Figure 3-7 Configure Action- Send Email

NOTE:This type of action can only be used in Correlation deployments
This action type can be used to send an Email when a correlated event triggers. The various parameters available are:
3.6.7 Imported JavaScript Action Plugins
For information on the JavaScript related actions and how to debug them, see Section 16.2, Action Manager in Section 16.0, Actions and Integrator. The JavaScript Actions can be used in many places throughout the Sentinel interface.