6.1 SSL Proxy and Direct Communication
The Sentinel components that might use the SSL proxy are the Sentinel Control Center and the Collector Manager.
6.1.1 Sentinel Control Center
The Sentinel Control Center uses the SSL proxy by default. The Sentinel Control Center connects to SSL through the proxied_client port. This port is setup to use server-side SSL certificate authentication only. The client side authentication uses the Sentinel Control Center user’s username and password.
To Log into Sentinel Control Center for the First Time:
-
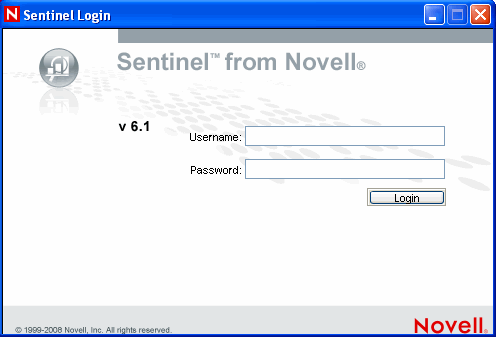
Go to Start > Programs > Sentinel and select Sentinel Control Center. Sentinel Login window displays.
-
Provide the user credentials you are provided with to log-in to Sentinel Control Center.
-
Username and password, if using SQL Server authentication, OR
-
Domain\username and password, if using Windows authentication
-
-
Click Login.
-
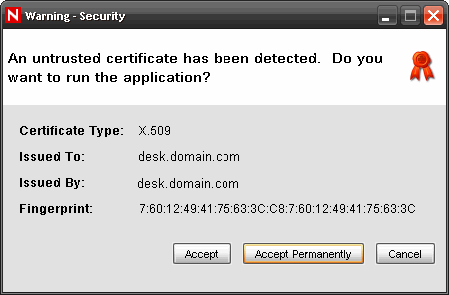
A warning message displays as shown in the figure below, for the first logon attempt.
-
If you select Accept, this message displays every time you try to open Sentinel on your system. To avoid this, you can select Accept permanently.
To Start the Sentinel Control Center on Linux and Solaris:
-
As the Sentinel Administrator User (esecadm), change directory to:
$ESEC_HOME/bin
-
Run the following command:
control_center.sh
-
Provide your username and password and click OK.
-
A Certificate window displays, click Accept.
The Sentinel Control Center users will need to repeat the procedure above to accept a new certificate under these circumstances:
-
The Sentinel communication server is reinstalled
-
The Sentinel communication server is moved to a new server
6.1.2 Collector Manager
Collector Manager can be installed in either proxy mode (using the SSL proxy) or direct mode (connecting directly to the message bus).
-
For Collector Managers that could be more easily compromised (for example, a machine in the DMZ), the SSL proxy is the more secure method of communication.
-
For Collector Managers in a more secure environment or where high event throughput is important or installed on the same machine as the Data Access Service (DAS), direct communication to the message bus is recommended.
The Collector Manager connects to SSL through the proxied_trusted_client. To enable Collector Manager to restart without human intervention after a reboot, this port is set up to use both server and client SSL certificate authentication. A trust relationship is established between the proxy and Collector Manager (certificate exchange), with future connections using the certificates to authenticate. This trust relationship is set up automatically during installation.
The trust relationship will need to be reset for every Collector Manager using the SSL proxy if the following circumstances apply:
-
The Sentinel communication server is reinstalled
-
The Sentinel communication server is moved to a new server
This procedure can also be used to change a Collector Manager from direct mode to proxy mode.
To Reset Trust Relationship for a Collector Manager:
-
Log into the Collector Manager server as the Sentinel Administrator (esecadm by default).
-
Open the configuration.xml file in $ESEC_HOME/config or %ESEC_HOME%\config in a text editor.
-
Modify "Collector_Manager", "agentmanager_events", and "Sentinel" services in configuration.xml to use "proxied_trusted_client" strategy ID. Here is an excerpt from a sample file:
<service name="Collector_Manager" plugins="" strategyid="proxied_trusted_client"/> <service name="agentmanager_events" plugins="" strategyid="proxied_trusted_client"/> <service name="Sentinel" plugins="" strategyid="proxied_trusted_client"/>
-
Save the file and exit.
-
Run %ESEC_HOME%\bin\register_trusted_client.bat (or .sh file if on UNIX). You will see output similar to this:
E:\Program Files\novell\sentinel6>bin\register_trusted_client.bat Please review the following server certificate: Type: X.509 Issued To: foo.bar.net Issued By: foo.bar.net Fingerprint (MD5): A8:DF:BA:B2:F3:21:C9:27:28:48:13:B3:FE:F8:B4:AD Would you like to accept this certificate? [Y/N] (defaults to N): Y Please enter a Sentinel username and password that has permissions to register a trusted client. Username: esecadm Password:********* *Writing to keystore file: E:\Program Files\Novell\Sentinel6\config\.proxyClientKeystore
-
Restart the Sentinel Service on the server hosting the Collector Manager.
-
Repeat these steps on all Collector Managers using the proxy communication.