1.0 Understanding Security Agent for UNIX
Securing and monitoring performance of your UNIX and Linux environments can be expensive and time-consuming. The following are the most common issues that enterprise performance and security managers experience:
-
Deficits in staff knowledge concerning UNIX and Linux security and system expertise
-
Managing various operating systems including Red Hat, AIX, HP-UX, Solaris, and SUSE Linux
-
Controlling access to privileged commands and sensitive resources
-
Lacking intrusion detection and response systems to handle both real and potential security breaches
The Security Agent for UNIX (Agent) helps you effectively address these challenges by enabling NetIQ security products, such as Secure Configuration Manager, Change Guardian, and Sentinel, to monitor the configuration and risk compliance of your UNIX and Linux environments.
The Agent validates the configuration of UNIX and Linux endpoints to ensure that compliance with corporate security policies and find potential vulnerabilities. An endpoint represents an Agent-monitored operating system, application, web server, or database instance.
It collects security compliance information from one or more endpoints in one or many domains. The Agent receives requests from NetIQ security products and runs commands or responds by returning data, status, or results. It runs locally on computers throughout your enterprise.
Figure 1-1 Security Agent for UNIX Architecture
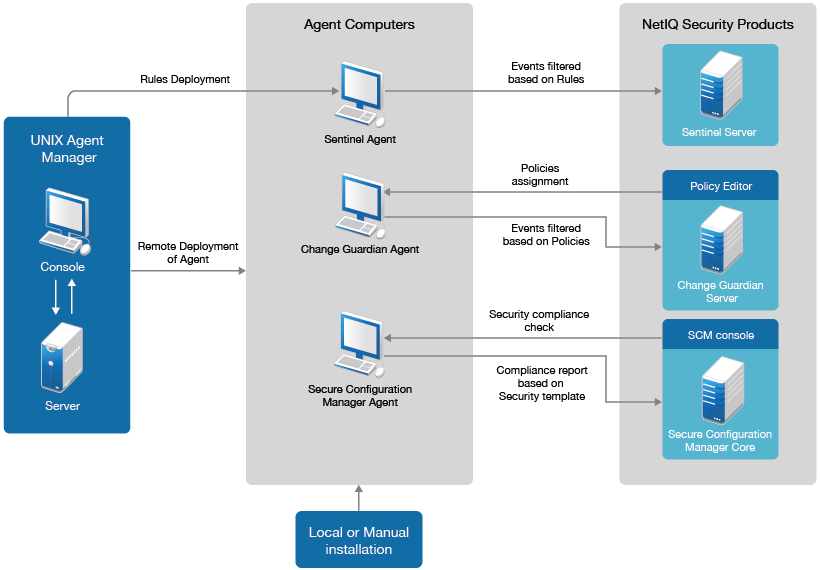
NetIQ UNIX Agent Manager is a console that you can use to manage all your Agent components across your enterprise. UNIX Agent Manager runs on Windows and Linux. You can use UNIX Agent Manager to install to several computers at the same time.
UNIX Agent Manager allows you to install and configure all your Agent components across your enterprise instead of interacting with the Agents individually. UNIX Agent Manager also allows you to see any UNIX computers that Secure Configuration Manager, Sentinel, and Change Guardian monitor. UNIX Agent Manager consists of a console and a server that stores information and communicates with the Agents. You can install numerous consoles that can connect to a single server.
The Agent communicates with the UNIX Agent Manager server. The user can install, upgrade, stop, and start the Agent through a command line interface or through the UNIX Agent Manager console. UNIX Agent Manager server communicates with the main NetIQ security products. The server stores information about where the Agents are installed, where consoles are installed, and which users have access to change what information about the Agents. The user need not interact directly with the UNIX Agent Manager Server. Users can use the UNIX Agent Manager console to install, configure, patch, monitor, start, and stop the Agents across their enterprise.
When you install an Agent, you can choose which NetIQ security products (Sentinel, Change Guardian, or Secure Configuration Manager) will monitor the computer on which the Agent resides. A single Agent can perform monitoring for one or more NetIQ security products. Each NetIQ security product has its own method for registering the Agents and configuring the Agent to send the proper data.
Each Agent sends regular communication, called a heartbeat, to verify the operation. When the Agent receives a heartbeat request, the Agent polls its monitored endpoints to verify their statuses and then responds to NetIQ security products.
For Sentinel, the rules are deployed on the Sentinel Agent via UNIX Agent Manager. The events are filtered and forwarded to the Sentinel server based on the rules deployed. You can monitor the most complex IT environments and obtain the security required to protect your IT environment.
For Change Guardian, the policies are deployed to monitor critical files on Change Guardian Agent via policy editor. The events are filtered and forwarded to the Change Guardian server based on the policies assigned. You can monitor security event details that pinpoint the who, what, when, where, and authorization status of a change or activity, including before and after details of the change.
For Secure Configuration Manager, the Agent also responds to requests for data sent from core services in the form of security checks and policy templates. Policy templates are groups of security checks to audit a specific series of IT controls that match a security policy standard. The Agent translates the security checks into queries and forwards to its monitored endpoints. Upon receiving responses to the queries, the Agent reports the results to the Secure Configuration Manager server.