8.3 Configuring SecureLogin for Smart Cards
No two organizations have the same environment and requirements, SecureLogin includes a number of options that determine SecureLogin's behavior, such as how single sign-on data is encrypted (that is, using the smart card or a passphrase question and answer) and how to handle scenarios such as lost cards.
To configure the preferences, use the iManager in eDirectory environments, MMC plug-in for Active Directory environments, and SecureLogin Manager in LDAP v3-compliant directories such as Sun, Oracle, and IBM.
-
Launch the Administrative Management utility (iManager, SLManager, or MMC snap-ins).
-
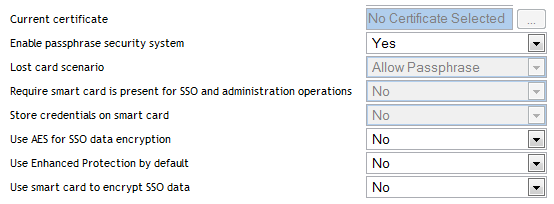
Click . The Preferences Properties table is displayed.
-
In the column, go to and select the appropriate preferences.
-
Click .
-
Click .
The following sections explain the various security preferences:
8.3.1 Using AES for SSO Data Encryption
This option determines the level and standard of encryption used to encrypt single sign-on data stored on the smart card by allowing the use of AES instead of triple DES.
Figure 8-1 Using AES for SSO Data Encryption
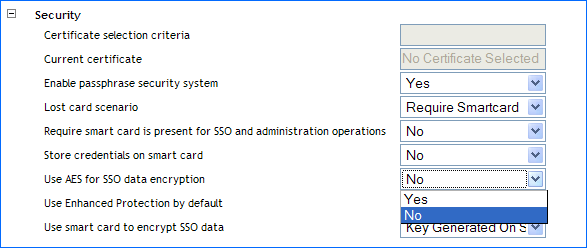
If you select , a 168-bit key used with triple DES (EDE) in Cipher-Block Chaining (CBC) mode is used to encrypt the user's single sign-on credentials.
NOTE:The input key for DES is 64 bits long and includes 8 parity bits. These 8 parity bits are not used during the encryption process, resulting in a DES encryption key length of 56 bits. Therefore, the key strength for Triple DES is actually 168 bits.
If you select , then a 256-bit key used with AES (EDE) in CBC mode is used to encrypt the user's credentials.
If a previous version of SecureLogin has been implemented with passphrases enabled and if this option is set to , users must answer with a passphrase before data can be decrypted and reencrypted by using AES.