Secure Configuration Manager 7.0 Release Notes
Secure Configuration Manager 7.0 includes new features, improves usability, and resolves several previous issues.
Many of these improvements were made in direct response to suggestions from our customers. We thank you for your time and valuable input. We hope you continue to help us ensure our products meet all your needs. You can post feedback in the Secure Configuration Manager forum, our community website that also includes product notifications, blogs, and product user groups.
For more information about Secure Configuration Manager, see the Secure Configuration Manager website.
For the latest version of this release notes document, see the Secure Configuration Manager 7.0 documentation website.
1.0 What’s New?
The following sections outline the key features and functions provided by this version, and issues resolved in this release.
1.1 New Console for Secure Configuration Manager
This release introduces the Web console, which is a browser-based interface for accessing many of the features available for end users:
-
Get a high-level view of your IT assets, including the status of their health, compliance, and risk to your enterprise security
-
Execute security checks and run policy templates
-
Create dynamic reports that combine the results of multiple policy templates and endpoints
For more information, see Section 1.3, Enhanced View of Your Assessment Results.
-
Create and apply tags to endpoints and policy templates
For more information, see Section 1.2, Add Tags to Endpoints and Policy Templates.
-
Create and apply saved lists for security check parameters
-
Create and apply exceptions to assessment results
-
View the status of jobs
-
Launch the Dashboard without having to log in again
The new Web console replaces some functionality provided by the (legacy) Windows console. Users can log in with any supported Web browser on either a desktop computer or a tablet. The Web console also includes context-sensitive Help to provide information when you need it.
For a quick overview of using the Web console to view the current state of your assets and group endpoints into logical categories, see the video: Introduction to SCM 7.0 Web Console - Part 1. For more information about using the Web console in general, see the User’s Guide for Secure Configuration Manager and the Help in the Web console.
1.2 Add Tags to Endpoints and Policy Templates
This release introduces the ability to tag endpoints and policy templates. The tags serve as customized labels that help users identify, organize, and search endpoints or policy templates.
If you have a console administrator role, you can create and apply an unlimited number of tags to each endpoint or policy template. For example, you might create standard tags, such as UNIX and SQL, that apply to a large number of endpoints. Then you might add more specific identifiers for particular endpoints, such as Web server to indicate the endpoint’s purpose or HIPAA to denote that an endpoint must meet the particular security policy.
All users can view and search the tags associated with endpoints or policy templates. Tagging is available in the Web console only.
For more information, see the User’s Guide for Secure Configuration Manager and the Help.
1.3 Enhanced View of Your Assessment Results
The new Web console provides two ways to determine whether your assets comply with security and system configuration policies. Both assessment reports and dynamic reports enable you to visualize the results of assessment run against endpoints and managed groups. You can view the compliance, risk status, and distribution of assets, endpoints, and groups either in tables or charts and graphs. You can also delve into the results to determine which endpoints pose a risk to your environment.
For more information, see the User’s Guide for Secure Configuration Manager and the Help.
Assessment Reports
For each policy template or security check that you run, you can generate an assessment report in the Web console. Depending on the type of assessment you run, you can drill down into the report results to determine which endpoints and groups failed security checks, and how. You can select endpoints, then re-run the failed checks for those endpoints only.
Figure 1 Assessment report for a policy template run
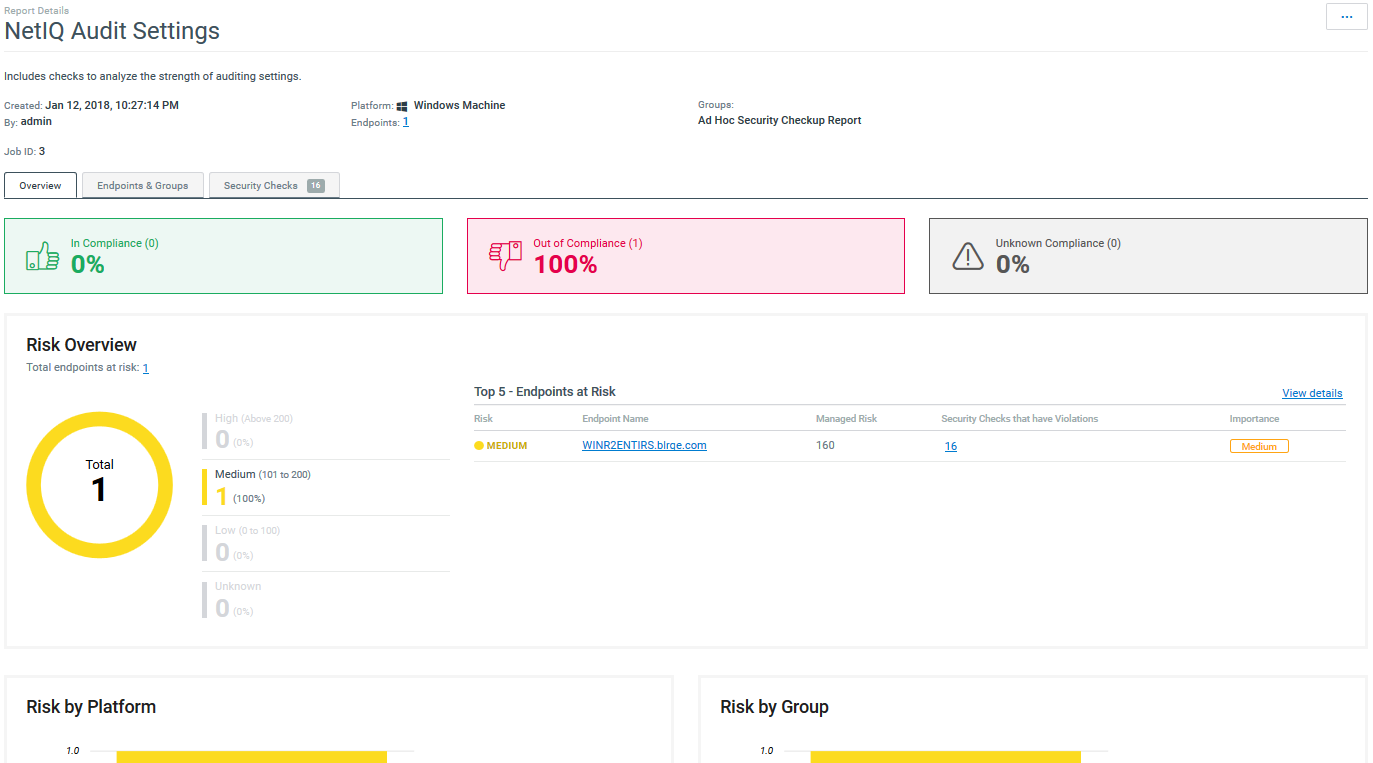
Dynamic Reports
This release introduces dynamic reports, which you create and generate in the new Web console. Dynamic reports combine the results of multiple policy templates and endpoints into a single aggregated report, so you can have a clear understanding of the state of your assets.
Each dynamic report can include the results for any set of endpoints, regardless of their operating system or application type. You can generate a dynamic report containing one or more policy templates, specify a timeframe, then the Web console will show you results for any endpoints that might have been part of those policy templates runs. If the policy template ran more than once in that timeframe, the report includes a trend graph so you can observe changes over time.
Compliance
Helps you determine how your assets comply with your organization’s security policies and technical standards. You can use this report also to compare the results of one endpoint with another.
Figure 2 Compliance reports include a section that helps you identify the endpoints that fail to comply with security policies
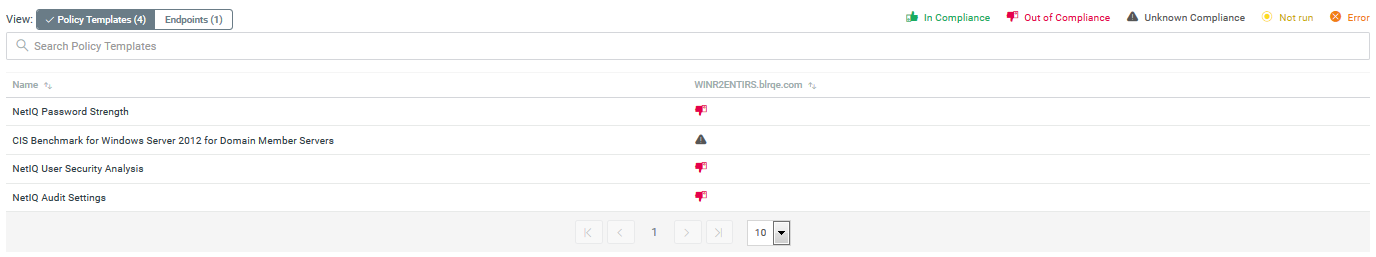
Risk
Helps you determine whether your assets pose a high, medium, or low security risk to your environment.
Figure 3 Risk reports include a section that shows you which policy template results indicate the areas of highest risk to your environment
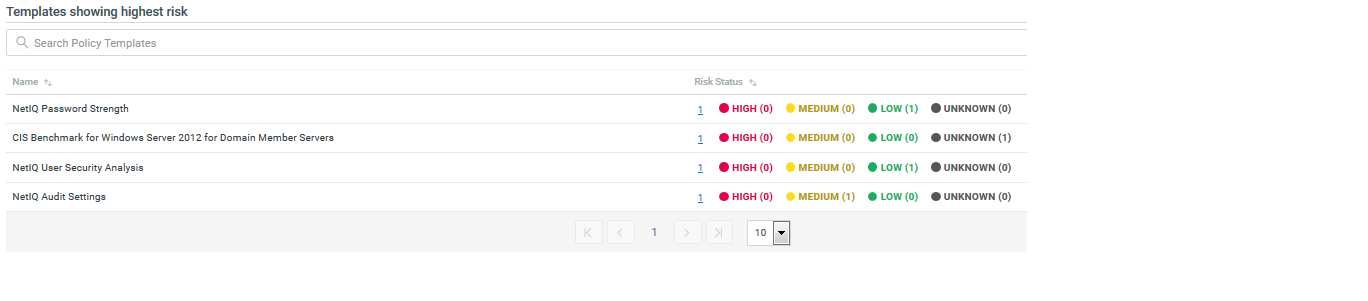
Snapshot
Gives you a high-level view of the state of risk and compliance for your assets. The snapshot report is similar to an assesment report, but can include multiple policy templates and endpoint types.
Figure 4 Snapshot reports include both the percentage of endpoints out of compliance as well as which endpoints pose the highest level of risk to your environment
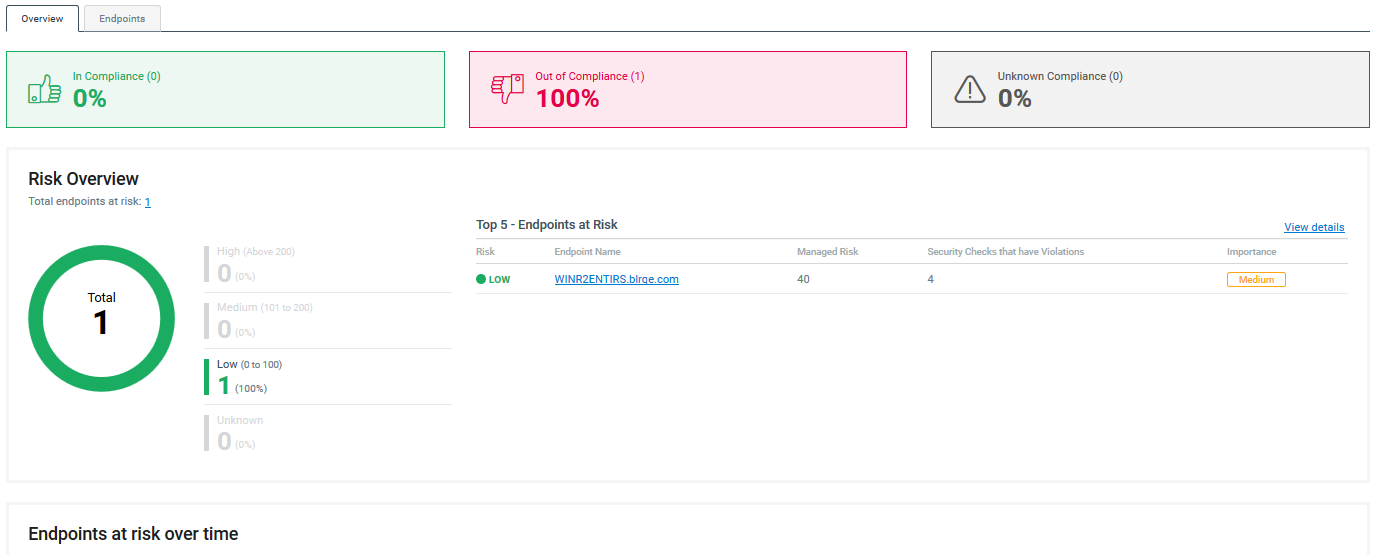
1.4 Java Upgrade
Secure Configuration Manager 7.0 includes Java 8 update 112, which includes fixes for several security vulnerabilities and also improves the performance.
1.5 Updated Agent Support for Windows
This release adds support for the Secure Configuration Manager Windows Agent 7.0 (Windows Agent 7.0), including updated objects and attributes in the Windows namespace.
For more information about the endpoints that you can manage with the new agent, see New Windows Endpoints and the Installation and Configuration Guide for Secure Configuration Manager Windows Agent.
1.6 SCAP 1.2 Inside
This release embeds NIST SCAP 1.2 certified binaries in the SCAP Module for Secure Configuration Manager 7.0 (SCAP Module). You must purchase the SCAP Module separately. Contact your sales representative.
For more information about the SCAP Module, see the Secure Configuration Manager SCAP Module User’s Guide .
1.7 End of Support for iSeries Agents and Endpoints
This release does not include support for iSeries agents or endpoints. To monitor your iSeries assets using the latest release of Secure Configuration Manager, NetIQ recommends that you use TGAudit, which provides enhanced capabilities and reporting. If you are entitled to NetIQ Security Solutions for iSeries, you can use TGAudit at no extra cost. You can download TGAudit from the download page https://download.microfocus.com/Download?buildid=ZoH3ukkXcTc~. For more information about TGAudit or migrating your data, contact your Sales Representative or Technical Support.
If you want to continue monitoring your iSeries assets using your existing agents and endpoints, you will need to use a prior version of Secure Configuration Manager installed on a separate server. You must also maintain separate databases for each version.
1.8 Updates to Certified Platforms
This release adds support for several platforms, either for running the product or managing agents and endpoints.
For more information, see the system requirements for each component in the
SQL Server 2016
The Secure Configuration Manager database and the Analytics Database (Dashboard and Web console) can now run on Microsoft SQL Server 2016.
Microsoft Windows Server 2016
You can now install the following Secure Configuration Manager components on Microsoft Windows Server 2016:
-
Analytics Database, which is part of the Dashboard installation
-
Core Services
-
Dashboard
-
Secure Configuration Manager database
-
Windows agent
-
Windows console
New Windows Endpoints
In addition to the previously supported Windows endpoints, the new Windows Agent 7.0 can monitor the following Microsoft platforms:
-
IIS 10.0
-
SQL Server 2016
-
Windows 10
-
Windows 8.1
-
Windows Server 2016
For more information, see the Release Notes for Secure Configuration Manager Windows Agent 7.0.
Endpoints No Longer Supported
Windows Agent 7.0 cannot manage the following endpoints:
-
Active Directory on Windows Server 2008
-
Active Directory on Windows Server 2012
-
Oracle 9i
-
Windows 7
-
Windows Server 2012
-
Windows Vista
To continue managing these endpoints in your environment, ensure that you keep at least one older version of the Windows agent.
1.9 Enhancements
Secure Configuration Manager 7.0 includes the following enhancements.
Ability to Distribute Reports Only if the Score is Greater Than Zero
You can now configure Secure Configuration Manager to distribute reports only if the score is greater than zero. For more information, see Enabling the Ability to Distribute Reports Only if the Score is Greater than Zero
in the User's Guide for Secure Configuration Manager. (Bug 883100)
Improved Assessment Report Results when an Error Occurs
If you run an assessment that results in an error for an endpoint, the Web console displays a compliance or risk score of -1 for the endpoint / security check combination that caused the error. The error might indicate that the endpoint needs to be re-registered, the security check failed to function appropriately, or the agent lost communication with the endpoint or Core Services.
In the Windows console, you will continue see a compliance or risk score of 0 for the endpoint / security check combination.
For more information, see the User’s Guide for Secure Configuration Manager. (Bug 1070969)
Users with NetIQ Exceptions Approval Manager Role Receive Notification Emails Whenever Exceptions are Created
If exception approval is enabled, Secure Configuration Manager now sends notification emails to the users with the NetIQ Exception Approval Manager role whenever exceptions are created. The user who has created the exception also get a notification email whenever there is a change in the approval status of the exception. For more information, see Approving Exceptions
in the User's Guide for Secure Configuration Manager. (Bug 887814)
Enhancement to Configure Scheduled Jobs Behavior when Core Services Restarts after a Downtime
You can configure scheduled jobs to not run immediately when the Core Services restarts after a downtime. This helps you to avoid too many jobs simultaneously running after Core Services starts.
For example, if the Core Services computer has stopped at 9 a.m. because of an outage and restarts at 10.30 a.m., and you have scheduled 25 jobs to run at 10 a.m., those jobs might run immediately after Core Services restarts.
To configure scheduled jobs to not run immediately after Core Services restarts following a downtime, see Configuring Scheduled Jobs Behavior when Core Services Restarts after a Downtime
in the User's Guide for Secure Configuration Manager.
1.10 Software Fixes
Secure Configuration Manager 7.0 includes software fixes that resolve several issues.
Incorrect Time Displayed in Reports
This release resolves an issue where delta reports and security check reports displayed incorrect time. (Bug 1005719)
2.0 System Requirements
This release requires that the Secure Configuration Manager Dashboard (the Dashboard) be installed in your environment and connected to Core Services. The new Web console requires the Analytics Database, which is installed with the Dashboard. For more information, see Section 4.1, Considerations for Installation and Upgrade.
NOTE:If you installed the Dashboard with Secure Configuration Manager 6.1 or 6.2, you are not required to upgrade the Dashboard.
For more information about hardware requirements, supported operating systems, and browsers, see the following resources:
For more information about the security agents that you can use with this release, see Section 3.0, Security Agent Requirements.
3.0 Security Agent Requirements
This release supports the following security agent versions:
- UNIX agents
-
7.5.1
7.5
- Windows agents
-
7.0
6.2
6.1
4.0 Installing or Upgrading to This Release
You can upgrade to Secure Configuration Manager 7.0 from the following previous versions:
-
6.2 or later
-
6.1
For more information, see Installing
and Upgrading
in the Secure Configuration Manager Installation Guide.
4.1 Considerations for Installation and Upgrade
Before installing or upgrading to this version, review the considerations for the following components and features:
Installing on Windows 10
Security settings on Windows 10 computers might prevent you from launching the Secure Configuration Manager installation program. The launch might either fail with an error indicating that another user canceled the operation or fail without displaying an error.
To install on Windows 10, complete one of the following steps:
- If you have not downloaded the installation files to the computer
-
Have your system administrator enable Do not preserve zone information in file attachments in the gpedit.msc group policy on the desired computer. Then download and run the installation program.
- If you already downloaded the installation files to the computer
-
Manually modify the installation files.
-
Right-click the file, then select Properties.
-
In the General tab, select Unblock.
-
For more information, see the following explanations of this Microsoft issue:
.NET Framework 4.6.1
This version requires .NET Framework 4.6.1. When you upgrade or install the Windows console for Secure Configuration Manager, the setup.exe program automatically installs the .NET software. However, Microsoft has a known issue related to installing .NET Framework on certain operating systems. For more information, see Section 4.2, Installing or Upgrading to .NET 4.6.1.
NOTE:You must restart the server after installing .NET Framework with the setup.exe program. Then you can continue installing other Secure Configuration Manager components on the server.
Analytics Database for the Web Console and Dashboard
The Analytics Database has always been a component of and installed with the Dashboard. The new Web console also requires this database. However, you might not have installed the Dashboard for Secure Configuration Manager 6.2 or earlier.
When you run the setup.exe file to install or upgrade Core Services, the program asks you whether the Dashboard is already installed. The process wants the IP address and port for the Analytics Database. You can proceed in one of the following ways:
-
Dashboard is not installed, so you do not specify values for the Analytics Database.
In this case, install the Dashboard after you upgrade Secure Configuration Manager. To specify the settings for the Analytics Database, log in to the Web console. Then go to Settings > Analytics Database.
-
Dashboard is not installed but you know the IP address and port where you plan to install the Analytics Database.
In this case, specify the values. Then install the Dashboard after you upgrade Secure Configuration Manager.
-
Dashboard is installed, so you can specify the values for the Analytics Database.
You can continue using your existing Dashboard if you installed it with Secure Configuration Manager 6.1 or 6.2. Otherwise, upgrade the Dashboard to this release.
For more information about the Dashboard requirements, see ”Planning to Install the Dashboard” in the Secure Configuration Manager Installation Guide.
For more information about updating the Dashboard settings in the Web console, see “Configuring the Web Console” in the Web console Help.
Secure Configuration Manager Windows Agent
The NetIQ Secure Configuration Manager Windows Agent (Windows agent) gathers data about Windows endpoints and network devices.
-
To deploy a Windows agent version 7.0 to Windows agents already registered with Secure Configuration Manager, you must locally upgrade at least one agent in each domain. Secure Configuration Manager uses the first upgraded agent as a Deployment Agent for the domain. Once an agent is upgraded, Secure Configuration Manager can automatically assign it as a Deployment Agent. For more information about deployment and Deployment Agents, see the Secure Configuration Manager Windows Agent Installation and Configuration Guide and the User’s Guide for Secure Configuration Manager.
-
The setup program automatically adds a Windows agent to the Core Services computer, if no agent previously existed on the computer. If a Windows agent exists on the computer, the setup program upgrades the agent to version 7.0. Secure Configuration Manager assigns this agent as the default Deployment Agent. During installation, you should ensure that the run-as account specified for the NetIQ Security Agent for Windows service has the credentials to deploy to remote computers. For example, specify a domain administrator account.
-
To immediately upgrade your Windows agents to version 7.0, you might need to re-register the agents before using the Deployment feature in the console. Secure Configuration Manager requires that the Properties window for each agent specifies a fully qualified host name (FQHN) for the agent computer. Secure Configuration Manager needs to know in which domain each agent resides so that Core Services can assign a Deployment Agent to use for deploying version 7.0 to the agents.
However, if you upgrade your Windows agents more than 30 days after upgrading the Secure Configuration Manager infrastructure to version 7.0, you might not need to re-register your Windows agents. The Asset Details and Discovery job might collect the FQHN during a regularly scheduled run since this job enables Core Services to update agent and endpoint properties. You can also run this job manually from the Scheduled Jobs queue.
-
When the upgraded agent registers with Core Services, the default communication port changes from 1626 to 1627. If you upgrade an agent that communicates with Core Services on a port other than the default ports, you must manually re-register the upgraded agent.
-
If you want to re-deploy an agent that has already been successfully deployed to a remote computer, you must uninstall the agent first. For example, you might want to change the credentials of the NetIQ Security Agent for Windows service or resolve issues with the agent. The Deployment wizard does not change the settings for a previously installed agent, even though you modify the settings as part of the deployment process. The Windows agent setup program prevents you from installing an agent when the same version already exists on the computer, but the Deployment wizard does not.
Discovered Systems
The upgrade process removes all existing records from the Discovered Host table in the database. This means that the upgrade also removes all systems from the Discovered Systems content pane.
-
After you successfully upgrade or install Secure Configuration Manager and register your agents, the Asset Details and Discovery job automatically adds application endpoints discovered on currently registered Windows and UNIX systems.
To manually repopulate Discovered Systems with unmanaged systems, update the Discovery settings in the Core Services Configuration Utility, and then initiate the discovery process. For more information about discovery, see the Help and the User’s Guide for Secure Configuration Manager.
-
To discover systems in Active Directory, you must update the settings on the Discovery tab of the Core Services Configuration Utility.
4.2 Installing or Upgrading to .NET 4.6.1
Applies to Windows 8.1 and Windows Server 2012 R2, or later, operating systems
The Windows console for this release requires .NET Framework 4.6.1. The setup.exe program for this release automatically installs the .NET Framework. However, the installation process for .NET might stall or end unexpectedly.
To mitigate these issues, ensure that you apply Microsoft KB2919442 and KB2919355, and any related KBs, in the order described in the installation instructions for the KB articles. Also, after installing .NET 4.6.1 with the setup.exe program, you might need to restart the computer before you can continue installing the other components.
To find the .NET 4.6.1 installation program, navigate to the \CDImage\CDImage\Intel\redist directory of the Secure Configuration Manager installation package.
For more information about these issues, see .Net 4.6 will not install on Server 2012 R2
.
5.0 Known Issues
NetIQ Corporation strives to ensure our products provide quality solutions for your enterprise software needs. The following issues are currently being researched. If you need further assistance with any issue, please contact Technical Support.
-
Section 5.3, Windows 32-bit Server Unexpectedly Restarts after Dashboard Installation
-
Section 5.4, Issues with Security Agent for UNIX and Change Guardian
-
Section 5.5, Exporting Full Delta Reports to Microsoft Excel Format Fails
-
Section 5.6, Problem with Clicking the Back Button While Upgrading in Distributed Setup
-
Section 5.8, Cannot Create, Install, or View Security Certificates Using the sslkey.bat File
-
Section 5.10, Endpoint Registration Fails after Regenerating Crypto Keys
-
Section 5.12, Issues with Check Output View when the Data is High
5.1 Issues that Affect Only the Web Console
The following issues apply only to the Web console, which this release introduces:
Some Security Checks Require the Wrong Parameter Value Type
Issue: In the Web console, the following security checks erroneously require you to specify an integer instead of alpha-numeric characters to indicate an enabled/disabled value for a parameter:
|
Platform |
Security Check |
|---|---|
|
IIS |
FTP logging enabled |
|
UNIX |
Ownership and permissions of files under /etc Minimum Password length restrictions |
|
Windows |
Service status User list by status |
(Bug 1068913)
Workaround: When you run these security checks, enter 1 to represent enabled and 0 for disabled.
Alternatively, you can use the Windows console to run the security checks.
Anomalies when Viewing Jobs in Progress
The Web console might display the following anomalous behavior when you view a job that is in progress:
Fails to Display an Endpoint’s Status while the Job is in Progress
Some jobs might take longer than others to complete due to the number of security checks or endpoints being assessed. You can select a job that is still in progress to view its progress. However, the Web console might fail to display the status for one or more endpoints within the job. (Bug 1051613)
Displays an Erroneous Number of Endpoints
If you open a job that is in progress, the Web console might display an erroneous number of endpoints associated with the job. To determine the appropriate number of endpoints, check the value listed in the Name & Endpoints column of the Jobs > In Progress list. (Bug 1067395)
Cannot View Delta or Task Reports
Although the Web console can display all jobs in the jobs queue for Secure Configuration Manager, the console cannot generate a report for tasks or delta reports. To view those reports, use the Windows console.
The Web console does provide enhanced views of assessment reports, as well as dynamic reporting. For more information, see the Help for the Web console and the User’s Guide for Secure Configuration Manager. (Bug 1069002)
Cannot Generate Dynamic Reports in FIPS Mode
The Web console cannot generate dynamic reports when Secure Configuration Manager is in FIPS mode. In the console, you might see the following message:
fips mode: only sunjsse trustmanager may be used
For more information about configuring FIPS mode, see Enabling FIPS Communication
in the User’s Guide for Secure Configuration Manager. (Bug 1073056)
Getting Started Tour Fails to Respond to Keyboard Arrow Keys
The Web console provides a Getting Started tour to help you explore new features in the product. To move from one page in the tour to the next, you must click the left or right arrows in the interface. The tour does not respond to presses of the keyboard arrows. (Bug 1069547)
Cannot View Some Reports Listed in the Jobs Queues
Issue: When you click View Report for a desired report, the Web console might display the following message:
Cannot display the report because it does not exist.
This message occurs in the following circumstances:
-
Someone deleted the report in the Web console. For example, a different user deleted the report, and your browser had not refreshed the list of reports.
-
The report existed in a previous version of Secure Configuration Manager. However, either no one had opened the report in that version or the report’s schedule expired before you upgraded to this release.
(Bug 1071856)
Workaround: Try opening the report in the Windows console. Once Secure Configuration Manager generates the report in the Windows console, you can view it in the Web console.
Internet Explorer 11 Might Fail to Display Icons in the Web Console
Issue: When you use Internet Explorer 11, the Web Console occasionally might fail to display icons or images. For example, the images that indicate Online and Offline endpoints might disappear. However, the text indicating the status of the endpoints continues to be visible. (Bug 1070011)
Workaround: If this issue occurs, clear the cache in Internet Explorer. Alternatively, use one of the other supported Web browsers, such as Firefox, Edge, or Chrome.
Navigation Issues When Using a Screen Reader or the Keyboard
To support accessibility, you can use a screen reader or keyboard to navigate the Web console. However, some fields in the Web console might not behave as expected for your chosen navigation method:
-
To activate a dropdown menu, you might need to use the enter key rather than the spacebar key.
-
To select items in a dropdown menu, you might need to use the tab key, even though the screen reader prompts you to use the arrow key.
-
The screen reader cannot provide information about the contents of charts and graphs. However, it can read the legends associated with each chart or graph, which provide the same information in text format.
-
When you run a policy template or security check, you cannot use the keyboard to modify the Time Range value under Run Options.
(Bug 1069370, Bug 1068850)
Cannot Start Web Console while Core Services is Initializing
When you install Core Services, the initialization process for Core Services continues in the background even though you have completed and closed the installation program. A shorter initialization period occurs after you restart the NetIQ Core Services service.
If you attempt to launch the Web console before the initialization process completes, the console displays an error. You can refresh the page to establish a connection to Core Services. (Bug 1073053)
NOTE:The console can display some content without communication with Core Services. However, most content requires Core Services. For example, endpoint status.
Fails to Cancel All Selected Jobs
Issue: In the In Progress job queue, you can select multiple jobs then click Cancel to cancel the jobs. However, the Web console cancels only the most recent job. (Bug 1054179)
Workaround: To cancel jobs that are in progress, select only one job, then click Cancel. Then repeat the process for each job that you want to cancel.
5.2 Sentinel Cannot Retrieve Event-only Data
Sentinel fails to retrieve the data when you configure Secure Configuration Manager to send events only. This issue occurs only when both Sentinel and Secure Configuration Manager are in FIPS mode.
For more information about configuring FIPS mode, see Enabling FIPS Communication
in the User’s Guide for Secure Configuration Manager. (Bug 1068366)
5.3 Windows 32-bit Server Unexpectedly Restarts after Dashboard Installation
When you install the Dashboard on a Windows 32-bit system, the server might restart unexpectedly or you might see an error after closing the installation program. In these instances, the Dashboard usually remains functional, with services running and the Dashboard accessible after the server restart. (Bug 1073734)
5.4 Issues with Security Agent for UNIX and Change Guardian
The following issues occur if you use the Security Agent for UNIX 7.5 SP1 (UNIX agent) with both Change Guardian 5.0 and Secure Configuration Manager on the same server, and you use Change Guardian AM to upgrade or install the UNIX agent:
Agent Registration Fails in a New Installation of the Agent
When you install Security Agent for UNIX 7.5 SP1 as part of a new installation of Change Guardian 5.0 on the same computer as Secure Configuration Manager, the agent registration fails in Secure Configuration Manager because of the dynamic certificate changes. (Bug 1045613)
Agent Registration Fails after Upgrading the Agent
Issue: Secure Configuration Manager fails to register the UNIX agent if you upgrade the agent from version 7.5 to 7.5 SP1 using Change Guardian AM. (Bug 1001599)
Workaround: Perform the following steps from UAM to re-register the UNIX agent in Secure Configuration Manager:
-
Go to Configure > SCM Options.
-
Click Configure.
-
In the SCM Configuration window, ensure that the Core Services Address is same as the SCM Core IP Address, then click Save.
-
Restart the agent service by selecting Stop and Start in the Agent Controls panel.
OR
You can manually register the UNIX agent:
-
Navigate to the /usr/netiq/bin file.
-
Run the following command:
#./wcRegister
-
To restart Secure Configuration Manager services, run the following command:
#/etc/init.d/uvserv restart
5.5 Exporting Full Delta Reports to Microsoft Excel Format Fails
Issue: Secure Configuration Manager does not export full delta reports to Microsoft Excel format. (Bug 1001599)
Workaround: You can export delta reports in any other file formats such as .pdf, .tsv, .rtf, or .xml.
5.6 Problem with Clicking the Back Button While Upgrading in Distributed Setup
Issue: While upgrading Secure Configuration Manager to version 7.0 in the distributed setup in a computer where Core Services and the console are installed, the installation wizard displays incorrect screens if you click Back after the License Agreement screen. (Bug 994646)
Workaround: Cancel the upgrade process by closing the wizard, and start upgrading again.
5.7 Installation Fails on Computers that have Microsoft .Net Framework Version 4.5 Installed and Microsoft .Net Framework Version 3.5 is Not Enabled
Issue: If the computer on which you are installing contains Microsoft .NET framework version 4.5 and Microsoft .NET framework version 3.5 is not enabled, Secure Configuration Manager installation fails. (Bug 921158)
Workaround: Perform the steps specified in NetIQ Knowledgebase Article 7017878 before installing Secure Configuration Manager.
5.8 Cannot Create, Install, or View Security Certificates Using the sslkey.bat File
Issue: You cannot create, install, or view security certificates in your Core Services computer by running the sslkey tool. Secure Configuration Manager displays an error when you run the sslkey.bat file. (Bug 971532)
Workaround: You can use any third-party tool to create, install, or view security certificates.
5.9 Weekly and Daily Scheduled Jobs Do Not Save and Apply the Updated Recurrence Time Schedule
Issue: When you edit an existing weekly or daily scheduled job for recurrence time schedule and save it, Secure Configuration Manager does not save and apply the updated recurrence schedule. The next run date is not updated as per the updated recurrence schedule. (Bug 971902)
Workaround: Delete the scheduled job you intend to update and create a new schedule job with the same parameters but with the new, intended recurrence time schedule.
5.10 Endpoint Registration Fails after Regenerating Crypto Keys
Issue: While registering or reregistering an endpoint, if you regenerate the crypto key for SSH, the registration fails. This occurs because the key is not replaced in the .ssh/known_hosts file. (Bug 860552)
Workaround: Delete the .ssh/known_hosts file and register the endpoint again.
5.11 Retry Option in the Installation Program Does Not Work on Windows 7 and Windows Server 2008 R2
Issue: When you try to uninstall a Secure Configuration Manager component using the installation program on a computer that has Windows 7 or Windows Server 2008 R2, and if some files that belong to the component are in use, the installation program displays a File in Use dialog box. If you click Retry in that dialog box, ideally uninstallation should not continue and the error message should persist, but uninstallation resumes. (Bug 893069)
Workaround: Install the Microsoft KB 2649868.
5.12 Issues with Check Output View when the Data is High
Issue: The check output view in Secure Configuration Manager reports has the following issues when the amount of the data is high:
-
The output view is incomplete.
-
The scroll bar function is not supported.
(Bug 852044)
Workaround: There is no workaround at this time.
6.0 Contact Information
Our goal is to provide documentation that meets your needs. If you have suggestions for improvements, please email Documentation-Feedback@netiq.com. We value your input and look forward to hearing from you.
For detailed contact information, see the Support Contact Information Web site.
For general corporate and product information, see the NetIQ Corporate Web site.
For interactive conversations with your peers and NetIQ experts, become an active member of the Secure Configuration Manager forum, our community Web site that offers product forums, product notifications, blogs, and product user groups.
7.0 Legal Notice
For information about NetIQ legal notices, disclaimers, warranties, export and other use restrictions, U.S. Government restricted rights, patent policy, and FIPS compliance, see http://www.netiq.com/company/legal/.
Copyright © 2018 NetIQ Corporation. All Rights Reserved.
For information about NetIQ trademarks, see http://www.netiq.com/company/legal/. All third-party trademarks are the property of their respective owners.