6.5 Custom Check Examples
This section provides custom check examples you can create using the wizard.
6.5.1 Accounts with Passwords More than 60 Days Old
Secure Configuration Manager provides the Accounts with Passwords More than 90 Days Old security check. You can edit this check to create the Accounts with Passwords More than 60 Days Old custom check.
The Accounts with Passwords More than 60 Days Old custom check has the following properties:
|
Description |
Lists accounts with passwords older than 60 days. |
|
Explanation |
Users should change account passwords frequently to prevent passwords from being stolen or viewed. |
|
Risks |
Once malicious users have guessed a password, they can use that password until it is changed. The longer the interval between password changes, the more damage is possible by a compromised password. |
|
Remedies |
Require users to change their passwords every 60 days at a minimum. |
To create the Accounts with Passwords More than 60 Days Old custom check:
-
In the left pane, click Security Knowledge.
-
In the Security Knowledge tree pane, expand Security Checks > NetIQ Checks > Windows.
-
Select User/Groups.
-
In the content pane, right-click Accounts with Passwords more than 90 days old, and then click Edit Security Check.
-
In the left pane, click Attributes.
-
Select Password Policy in the Available Attributes pane.
-
Click the right arrow to move Password Policy to the Attributes to Check field.
-
In the left pane, click Filter.
-
Type 5184000 in the Criteria list.
-
Click Save As.
-
Type Accounts with passwords more than 60 days old.
-
Click OK.
6.5.2 Kernel Parameters
The following example shows how to create a simple informational check for a UNIX or Linux computer.
The Kernel Parameters custom check has the following properties:
|
Description |
Lists kernel parameters. |
|
Explanation |
Provides a list of editable kernel parameters. |
|
Risks |
This security check is for information only. |
|
Remedies |
This security check is for information only. |
To create the Kernel Parameters custom check:
-
In the left pane, click Security Knowledge.
-
In the Security Knowledge tree pane, expand Security Checks.
-
Right-click My Checks, and then click New Security Check.
-
Select UNIX in the Platform field.
-
Expand Host in the Object field to show the list of child objects.
-
Select Kernel Parameter.
-
Click Next.
-
Click the right double arrow button.
-
To create an unfiltered security check, click Next.
-
Click Next.
-
In the Scoring Method field, select Information Only.
-
Click Next.
-
Type Kernel Parameters in the Check Name field.
-
Select System in the Category field.
-
Type a description of your custom check in the Brief Description field.
-
Click Next.
-
Review the summary of your custom check.
-
Click Finish.
6.5.3 Registry Keys Modified Since Date
The following example shows how to create a custom check for registry keys on a Windows computer.
The Registry Keys Modified Since Date custom check has the following properties:
|
Description |
Checks for registry keys modified since specified date. |
|
Explanation |
Checks to identify any registry keys that have been modified since a specified date. |
|
Risks |
Unapproved modified registry keys may indicate an intruder or virus has tampered with your computer. |
|
Remedies |
Verify that all modified registry keys are from approved processes. Follow with other security checks to identify other evidence of tampering. |
To create the Registry Keys Modified Since Date custom check:
-
In the left pane, click Security Knowledge.
-
In the Security Knowledge tree pane, expand Security Checks.
-
Right-click My Checks, and then click New Security Check.
-
Select Windows in the Platform field.
-
Expand Workstation in the Object field to show the list of child objects.
-
Select Registry Key.
-
Click Next.
-
Select Key Name and Modification Date and click the right arrow button.
-
Click Next.
-
Select Modification Date in the Attribute list.
-
Select greater than in the Operator list.
-
Select User Parameter in the Type list.
-
Click the Criteria field to open the User Parameter window.
-
Type MODIFIED SINCE in the Name field.
-
Type Modified keys since this date in the Description field.
-
Click the checkmark button.
-
Click Next.
-
Type a default date in the Modified Since field using the MM/DD/YY HH:MM:SS format.
-
In the Registry Key Name field, type an asterisk (*), and then click Next.
-
Select Unique Count in the Scoring Method field.
-
Click Next.
-
Type Registry Keys Modified Since Date in the Check Name field.
-
Select System in the Category field.
-
Type a description of your custom check in the Brief Description field.
-
Click Next.
-
Review the summary of your custom check.
-
Click Finish.
6.5.4 Password Policy Violations
The following example shows how to create a custom check with multiple filters.
The Password Policy Violations custom check has the following properties:
|
Description |
Checks for simple password violations. |
|
Explanation |
Checks for users’ passwords being too short, empty, or in the dictionary. |
|
Risks |
Passwords that violate simple policy regulations are easy to break and are considered system vulnerable. |
|
Remedies |
Identify users with password violations and force password changes. |
To create the Password Policy Violations custom check:
-
In the left pane, click Security Knowledge.
-
In the Security Knowledge tree pane, expand Security Checks.
-
Right-click My Checks, and then click New Security Check.
-
Select Windows in the Platform field.
-
Expand Workstation in the Object field to show the list of child objects.
-
Select Password.
-
Click Next.
-
Click the right double arrow button.
-
Click Next.
-
Select Password found in dictionary in the Attribute list.
-
Select equals in the Operator list.
-
Select Value in the Type list.
-
Select True in the Criteria list.
-
Select Or in the AND/OR list.
-
On the next line, select Password is blank in the Attribute list.
-
Select equals in the Operator list.
-
Select Value in the Type list.
-
Select True in the Criteria list.
-
Click Next.
-
Click Next.
-
Select Count in the Scoring Method field.
-
Click Next.
-
Type Password Policy Violations in the Check Name field.
-
Select User/Groups in the Category field.
-
Type a description of your custom check in the Brief Description field.
-
Click Next.
-
Review the summary of your custom check.
-
Click Finish.
6.5.5 Suspicious User
The following example shows how to create a custom check with multiple filters combined in complex ways.
The Suspicious User custom check has the following properties:
|
Description |
Checks for remote suspicious users. |
|
Explanation |
Checks for remote users with poor password protection. |
|
Risks |
These accounts may be compromised. |
|
Remedies |
Verify accounts belong to trusted users and ensure that password policies are enforced. |
To create the Suspicious User custom check:
-
In the left pane, click Security Knowledge.
-
In the Security Knowledge tree pane, expand Security Checks.
-
Right-click My Checks, and then click New Security Check.
-
Select UNIX in the Platform field.
-
Expand Host in the Object field to show the list of child objects.
-
Select User.
-
Click Next.
-
Select User name, Primary Group ID, umask Value, Last logon date and time, and Password strength in the Available Attributes pane.
-
Click the right arrow button.
-
Click Next.
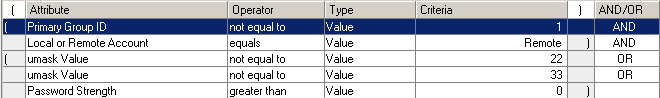
NOTE:The following filters are the logical equivalent to the following statement: “Check for all remote users without administrative accounts who have either umask values not equal to 022 or 033, or whose password strength is greater than 0.”
-
Select Primary Group ID in the Attribute list.
-
Select not equal to in the Operator list.
-
Select Value in the Type list.
-
Type 1 in the Criteria field.
-
Select AND in the AND/OR list.
-
On the next line, select Local or Remote Account in the Attribute list.
-
Select equals in the Operator list.
-
Select Value in the Type list.
-
Select Remote in the Criteria list.
-
Select AND in the AND/OR list.
-
To select the first two filters, click in the ( or ) column of the first filter, press and hold Shift, and click in the ( or ) column of the second filter.
-
To enclose the selected filters in parentheses, right click the highlighted area, and select Add ( ).
-
On the next line, select umask Value in the Attribute list.
-
Select not equal to in the Operator list.
-
Select Value in the Type list.
-
Type 022 in the Criteria field.
-
Select AND in the AND/OR list.
-
On the next line, select umask Value in the Attribute list.
-
Select not equal to in the Operator list.
-
Select Value in the Type list.
-
Type 033 in the Criteria field.
-
Insert parentheses to group the second and third filters.
-
Select OR from the AND/OR list.
-
On the next line, select Password Strength from the Attribute list.
-
Select greater than from the Operator list.
-
Select Value from the Type list.
-
Type 0 in the Criteria field.
-
To select the remaining filters, click in the ( or ) column of the umask Value filter, hold Shift, and click in the ( or ) column of the Password Strength filter.
-
To enclose the selected filters in parentheses, right click in the highlighted area, and then select Add ( ).
-
Click Next three times.
-
Type Suspicious User in the Check Name field.
-
Select User/Groups in the Category field.
-
Type a description of your custom check in the Brief Description field.
-
Click Next.
-
Review the summary of your custom check.
-
Click Finish.