1.4 How SaaS Account Management Works
SaaS Account Management (SAM) is an appliance that integrates seamlessly with NetIQ Access Manager. To use the account management functions in SaaS Account Management, you must have an Access Manager setup, a SAM appliance, and SaaS-specific SAML/Account Management connectors that are downloaded from the NetIQ public connector catalog.
The difference between SaaS Account Management connectors and SAML connectors is that the SaaS Account Management connectors automatically provision mapped users from the user store into the SaaS application (either by creating new users if necessary or claiming existing accounts), whereas SAML connectors require administrators to manually create the same user accounts in the user store of the application (for example, Salesforce).
NOTE:The connectors in the connector catalog that are capable of account management can be configured either for SAML only (to provide single sign-on for existing user accounts) or for SAML with Account Management to get the additional benefits of user provisioning.
SaaS Account Management currently supports only SAML2 applications.
The following graphic illustrates the SaaS Account Management architecture within the NetIQ Access Manager environment.
Figure 1-2 SAM Architecture
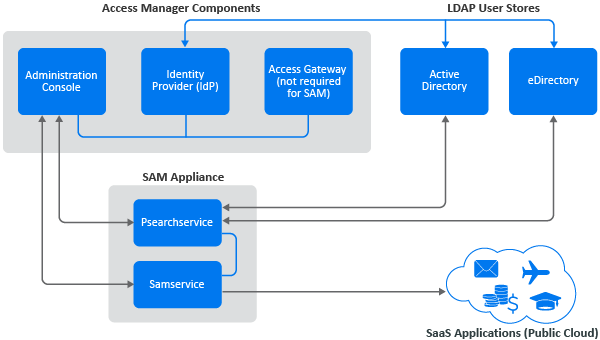
Once you have deployed SaaS Account Management in your Access Manager environment, you must provide information for each of your SAML applications to enable the service to provision user accounts to the SaaS providers. You map groups selected from your LDAP user stores in Access Manager to determine which users will be provisioned, and you can also map specific SaaS authorizations to those user groups.
The LDAP persistent search module (Psearchservice) handles provisioning, deprovisioning, and LDAP account changes for SaaS Account Management. After you configure a SAML2/Account Management application and save your configuration, the first time Psearchservice runs, it reads the LDAP directory and imports the mapped users from the user store into the specified SaaS application. Psearchservice then runs periodically (at a polling interval that you specify) to check for any changes in the LDAP directory.