1.1 Key Terms
1.1.1 Identity Manager
NetIQ Identity Manager is a service that synchronizes data among servers in a set of connected systems by using a robust set of configurable policies. Identity Manager uses the Identity Vault to store shared information, and uses the Identity Manager engine for policy-based management of the information as it changes in the vault or connected system. Identity Manager runs on the server in which the Identity Vault and the Identity Manager engine are located.
1.1.2 Connected System
A connected system is any system that can share data with Identity Manager through a driver. PUM is a connected system.
1.1.3 Identity Vault
The Identity Vault is a persistent database powered by eDirectory. Identity Manager uses Identity Vault to hold data for synchronization with a connected system. The vault can be viewed as a private data store for Identity Manager, or as a metadirectory that holds enterprise-wide data. Data in the vault is available to any protocol supported by eDirectory, including the NetWare Core Protocol (NCP), which is the traditional protocol used by iManager, LDAP, and DSML.
Because the vault is powered by eDirectory, Identity Manager can be easily integrated into your corporate directory infrastructure by using your existing directory tree as the vault.
1.1.4 Identity Manager Engine
The Identity Manager engine is the core server that implements the event management and policies of Identity Manager. The engine runs on the Java Virtual Machine in eDirectory.
1.1.5 Privileged User Manager Driver
The Identity Manager Driver for NetIQ Privileged User Manager (PUM) lets you automate access control to privileged accounts in Windows and Unix/Linux servers. You can now utilize the self-service request and approval workflow capabilities of Identity Manager to provide self-service access to privileged accounts on servers managed by PUM.
PUM helps IT administrators to provide controlled access to super-user and root accounts, allowing them to perform jobs without needlessly exposing administrative account credentials. PUM delegates privileged access to users and the access control policies are authorized via a centralized database. The PUM driver automates authorization of users into PUM based on the Identity Manager Entitlement grant.
NOTE:While the PUM driver controls privileged access to users on Windows and UNIX/Linux servers, you can use the Drivers for Linux and UNIX to create the user accounts on UNIX/Linux servers.
For more information about PUM, see the NetIQ Privileged User Manager Documentation Web site.
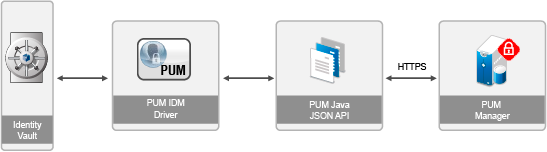
Figure 1-1 illustrates the data flow between Identity Manager and PUM, through the driver.
Figure 1-1 Data Flow between Identity Manager and PUM
1.1.6 Driver Shim
A driver shim is the component of a driver that converts the XML-based Identity Manager command and event language (XDS) to the protocols and API calls needed to interact with a connected system. The shim is called to execute commands on the connected system after the Output Transformation runs. Commands are generated on the Subscriber channel.
The PUM driver shim is implemented in Java and the name of the shim is NPUMDriverShim.jar. The PUM driver shim communicates with PUM through NPUM_api.jar. These APIs require PUM authentication to succeed.
If you use the Remote Loader, NPUMDriverShim.jar and NPUM_api.jar run on the server where the Remote Loader is running. Otherwise, it runs on the server where the Identity Manager engine is running.
The driver communicates with the PUM server via HTTPS protocol using the JSON API provided by PUM.
1.1.7 Remote Loader
A Remote Loader enables a driver shim to execute outside the Identity Manager engine (perhaps remotely on a different machine).
The Remote Loader is a service that executes the driver shim and passes information between the shim and the Identity Manager engine. When you use a Remote Loader, you install the driver shim on the server where the Remote Loader is running, not on the server where the Identity Manager engine is running. You can choose to use SSL to encrypt the connection between the Identity Manager engine and the Remote Loader. For more information, see the Identity Manager 4.0.2 Remote Loader Guide.
When you use the Remote Loader with the PUM driver shim, two network connections exist:
-
Between the Identity Manager and the Remote Loader
-
Between PUM and the PUM driver shim