11.3 Setting Up LDAP Authentication
-
Log in to Sentinel Log Manager as the administrator user.
-
Click the link on the top left corner of the page.
-
On the Users page, click .
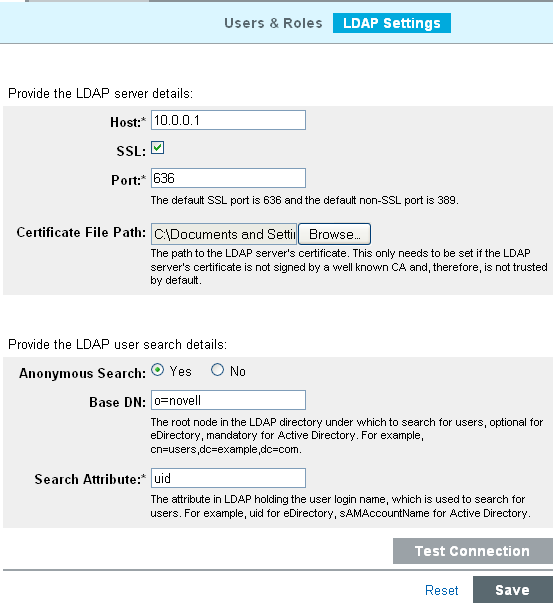
The LDAP Settings page is displayed.
-
Specify the following:
Field
Description/Action
The hostname or the IP address of the LDAP server.
Select this option if you want to connect to the LDAP server by using a Secure Socket Layer connection.
The port number for the LDAP connection. The default SSL port number is 636 and the default non-SSL port number is 389.
Path of the LDAP server CA certificate file.
This field must be set only if you selected the SSL option and if the LDAP server certificate is not signed by a well-known CA and, therefore, is not trusted by default.
Selectto perform anonymous searches or select if you do not want perform anonymous searches on the LDAP directory.
-
If Anonymous Search is Yes: The root node in the LDAP directory under which to search for users.
This is optional for eDirectory, and mandatory for Active Directory. For eDirectory, if the Base DN is not specified, the entire directory is searched to locate the users.
-
If Anonymous Search is No: The root node in the LDAP directory that contains the users.
This is mandatory if you are using Active Directory and if you set a domain name. For all other cases, this is optional.
The following are examples for specifying the Base DN:
-
eDirectory:
o=novell
-
Active Directory:
cn=users,dc=example,dc=com
The attribute in LDAP holding the user login name, which is used to search for users.
For example:
-
eDirectory:
uid
-
Active Directory:
sAMAccountName
This field is available only if you had selected for Anonymous Search.
The name of the Active Directory domain.
There is an additional approach applicable only for Active Directory for performing LDAP authentication without using Anonymous search:
When you specify the Domain Name, username@domainname (userPrincipalName) is used to authenticate the user before searching for the LDAP user object.
For example, test.example.com
This field is applicable only for ActiveDirectory and is available only if you selected for Anonymous Search.
NOTE:If is set and is not set, the is appended to the relative user DN to construct the absolute user DN.
For example, if the Base DN is set to o=novell and the absolute user DN is cn=sentinel_ldap_user,o=novell while creating LDAP user accounts, only the relative user DN i.e cn=sentinel_ldap_user can be specified.
-
-
Click to test whether the LDAP connection is successful.
The Test the LDAP Connection page is displayed.
-
Specify the test credentials to connect to the LDAP server:
-
If Anonymous Search is Yes: Specify the username and password.
-
If Anonymous Search is No: Specify the user DN and password. The user DN can be relative to the Base DN.
-
-
Click to test the LDAP connection.
A message is displayed that indicates whether the connection is successful.
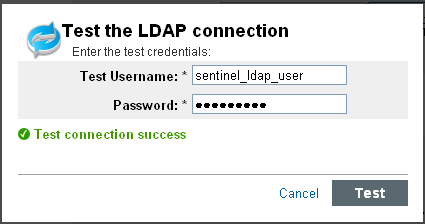
If there is any error, review the configuration details you provided and test the connection again.You can determine the cause of the failure by examining the /var/opt/novell/sentinel_log_mgr/log/server0.0.log file. You must ensure that the test connection is successful before saving the LDAP settings.
-
-
Click to save the LDAP settings.
On successful configuration:
-
The LdapLogin section of the /etc/opt/novell/sentinel_log_mgr/config/auth.login file is updated. For example:
LdapLogin { com.sun.security.auth.module.LdapLoginModule required java.naming.ldap.factory.socket="com.esecurity.common.communication.ProxyLdapSSLSocketFactory" userProvider="ldap://10.0.0.1:636/o=novell" userFilter="(&(uid={USERNAME})(objectclass=user))" useSSL=true; }; -
The LDAP server CA certificate, if provided, is added to a keystore named /etc/opt/novell/sentinel_log_mgr/config/.activemqkeystore.jks
-
After saving the LDAP settings successfully, you can create LDAP user accounts to enable users to log in to Sentinel Log Manager by using their LDAP directory credentials.
NOTE:You can also configure the Sentinel Log Manager server for LDAP authentication by running the ldap_auth_config.sh script in the /opt/novell/sentinel_log_mgr/setup directory.
The script also supports command line options. To view the command line options, run the script as follows:
/opt/novell/sentinel_log_mgr/setup/ldap_auth_config.sh --help