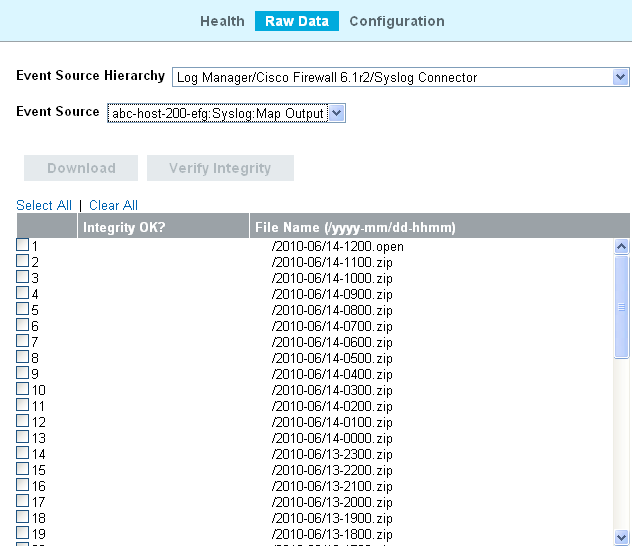
3.5 Verifying and Downloading Raw Data Files
The raw data files for each event source are compressed and moved to networked storage every hour and the file hash is computed for networked storage files. The file hash is used to check the integrity of the files in the networked storage.
-
Log in to Sentinel Log Manager as an administrator.
-
Click the link in the upper left corner of the page.
-
Click the tab.
-
In the section, select the desired Collector and Connector combination from the Event Source hierarchy drop-down list.
-
The field displays the list of associated event sources (hostnames or IP addresses). Select the event source from the drop-down list.
The table displays the list of local and networked storage raw data files for the selected event source.
-
Click to select all the files in the table.
-
To select a raw data file, select the check box next to the raw data file.
The and options are only enabled when you select a file from the table.
-
Click to verify the integrity of the selected files in the networked storage by comparing the hash values for the selected files in the networked storage.
If integrity verification is successful, a green icon is displayed next to the filename in the column. If it fails, a red icon is displayed.
The hash is computed and updated in database only for the files in the networked storage, but not for the local raw data files. Because the raw data files are updated until they are moved to networked storage, the hash value cannot be computed or updated for these files. It is not possible to check the integrity of the local raw data files.
-
Select the raw data file, then click to download the selected networked storage and local raw data files.
The selected files are downloaded in the form of a zip file that contains a .csv (comma separated values) file. If the networked storage files are selected, the zip file also contains a hash file corresponding to each of the networked storage files downloaded.
The SHA-256 algorithm is used to generate the file hash and the generated hash is Base64 encoded.
-
Click .