3.4 Configuring Full Tunneling
Novell SSL VPN is configured for split tunneling by default. This means that only the traffic that is enabled to go through the protected network, such as items meant for the corporate network, goes through the VPN tunnel. Traffic to public networks does not go through the tunnel. However, if you want all traffic in the client machine to go through the tunnel, you must configure SSL VPN for full tunneling.
When you configure SSL VPN for full tunneling, all traffic to the protected network as well as the public network passes through the tunnel, thereby making the SSL VPN connection more secure. Any session management information between the client and the Identity server, Linux Access Gateway -- (for Traditional SSL VPN), and the SSL VPN server is exchanged outside the SSL VPN tunnel. You can configure full tunneling for both Kiosk mode as well as Enterprise mode.
You must configure traffic policies for both split tunneling and full tunneling in your organization in order to permit access to specific internal hosts as well as prevent a hacker from controlling the machine via a connection external to the tunnel. The split tunneling policies must be ordered at the top of the policy list and the full tunneling policy must be placed as the last policy.
3.4.1 Creating a Full Tunneling Policy
-
In the Administration Console, click > .
-
Click to create a new traffic policy.
-
Specify a name for the traffic policy.
-
Select .
-
Select to allow the service in encrypted form.
-
Click.
-
Select from the section.
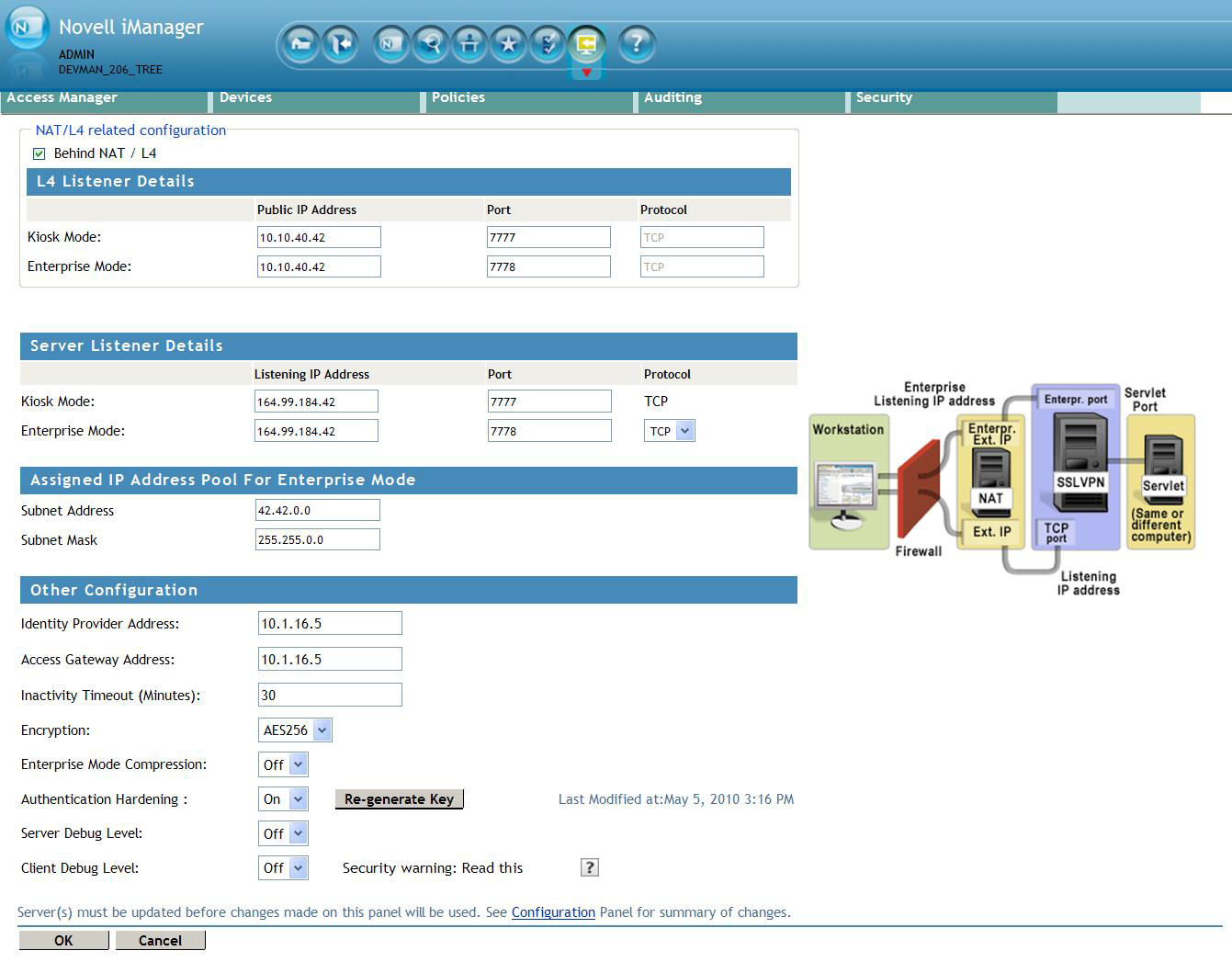
-
Specify the following information in the section:
Identity Provider Address: Specify the public IP addresses or the public DNS name of the Identity Server if you are configuring SSL VPN for the full tunneling mode. This configuration is required to split the management traffic from the tunneled traffic.
Access Gateway Address: Specify the IP address or DNS name of the Access Gateway if your server is accelerated by the Access Gateway. This field is not present if you have installed the ESP-enabled SSL VPN.This configuration is required to split the management traffic from the tunneled traffic.
NOTE:This server requires a split DNS if a DNS address is used.
-
To save your modifications, click , then click on the Configuration page.