5.5 Configuring Audit Server
The Secure Logging Server manages the flow of information to and from the auditing system. It receives incoming events and requests from the Platform Agents, logs information to the data store, monitors designated events, and provides filtering and notification services. You can configure the Secure Logging Server to automatically reset the critical system attributes according to the specified policy.
-
Log in to the Administration Console.
-
Select
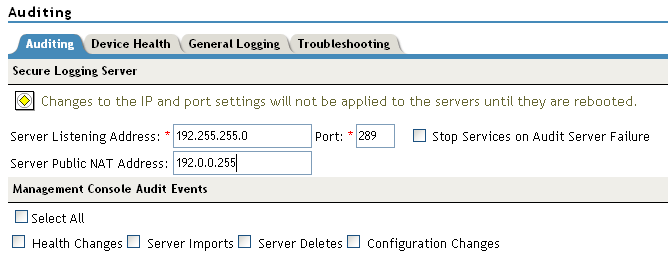
-
Fill in the following fields:
Server Listening IP Address: Specify the private listening IP address. Specify the IP address or DNS name of the audit logging server that you want to use. By default, the system uses the primary Administration Console IP address. If you want to use a different Secure Logging Server, specify the IP address of that server.
Server Public NAT IP Address: Specify the NAT IP address of the relevant server. For example, if you want to use the Sentinel private IP address on Server Listening Address 11.0.0.124, then you need to specify the NAT IP address of the Sentinel server in Server NAT IP Address to map the private address to a public address.To use a Sentinel server or a Sentinel Log Manager server instead of Novell Audit, specify the IP address or DNS name of the Sentinel Collector.
-
For more information on Sentinel, see the Sentinel 6.1 .
-
For more information on Sentinel Log Manager, see the Sentinel Log Manager 1.0 .
Port: Specify the port that the Platform Agents use to connect to the Secure Logging Server. The default port value is 289. The Sentinel servers listens on port 1289
Stop Service on Audit Server Failure: If you enable this checkbox, then audit events are always sent to audit server. If audit server is offline or not reachable, when an audit event is generated the apache services will be shut down.
If you want to use a Sentinel server or a Sentinel Log Manager server instead of the Novell Audit server, specify the port number of your Sentinel Collector.
IMPORTANT:Whenever you change the port or IP address of the Secure Logging Server, you must update all the Access Gateways, then restart the Identity Server, Administration Console, Access Gateways, SSL VPN servers, and J2EE Agents before the configuration changes take affect.
-
-
In the section, specify any or all of the following options to generate events:
Health Changes: Generates events whenever the health of server changes.
Server Imports: Generates events whenever a server is imported into the Administration Console.
Server Deletes: Generates whenever a server is deleted from the Administration Console.
Configuration Changes: Generates events whenever you change the server configuration.
Select All: Select this option to select all the audit events.
-
Click .
If you did not change the address or port of the Secure Logging Server, this completes the process. It might take up to fifteen minutes for the events you selected to start appearing in the audit files.
-
Restart all the Access Manager components imported into the Administration Console.
The Identity Server, Access Gateway, SSL VPN, and J2EE Agents do not start reporting events until they have been restarted.