3.4 Clustering SSL VPN Servers
You can cluster the high-bandwidth SSL VPN servers to provide load balancing and fault tolerance capabilities and act as a single server. Clients access the virtual IP address of the cluster presented on the L4 switch, and the L4 switch alleviates server load by balancing traffic across the cluster. Whenever a user accesses the virtual IP address (port 8080) assigned to the L4 switch, the system routes the user to one of the SSL VPN servers in the cluster, as traffic necessitates.
Clustering enables the following features:
-
Cluster configuration synchronization for all members of the cluster.
-
Each cluster member can handle sessions held by another server in the cluster. After a session is established, the same member usually handles all requests for that session. However, if that cluster member is not available to handle a request, another member processes the request.
-
Load balancing among the cluster members.
-
Transparent failover.
A cluster can be set up to function with an L4 switch or the Access Gateway to handle load balancing. A cluster can be set up to function with an L4 switch or by using the Access Gateway. You can have a cluster of servers in both HTTP and HTTPS. For more information on configuring the SSL VPN cluster by using the Access Gateway, see Clustering SSL VPNs by Using the Access Gateway without an L4 Switch
in the Novell Access Manager 3.1 SP5 SSL VPN Server Guide.
This section has the following information:
For more information about SSL VPN clusters, see Clustering the High-Bandwidth SSL VPN Servers
in the Novell Access Manager 3.1 SP5 SSL VPN Server Guide.
3.4.1 Prerequisites
-
An L4 switch is installed. The LB algorithm can be anything (hash/sticky bit), defined at the Real server level.
-
Persistence (sticky) sessions are enabled on the L4 switch. You usually define this at the virtual server level.
-
All SSL VPN servers must be running the high-bandwidth version and imported into the same administration console. The health status of all the imported servers must be green or yellow.
-
The traffic policies must be imported into the SSL VPN servers before they are clustered.
-
An SSL VPN Server configuration is created for the cluster, and all the SSL VPN servers are assigned to this configuration.
The base URL DNS name of this configuration must be the virtual IP address of the L4 server. The L4 switch balances the load between the SSL VPN servers in the cluster.
-
The following ports are open on the L4 switch for SSL VPN communication:
-
8080 (for HTTP communication)
-
8443 (for HTTPS communication)
-
7777 (for Stunnel over TCP and OpenVPN over UDP)
-
7778 (for OpenVPN over TCP)
-
-
All members of an SSL VPN cluster should belong to either an ESP-enabled Novell SSL VPN or a Traditional Novell SSL VPN.
3.4.2 Creating a Cluster of SSL VPN Servers
To create a new SSL VPN server cluster, you start by creating a cluster configuration with a primary server.
-
In the Administration Console, click > > .
-
Select the SSL VPN server that you want to add to the cluster, then click .
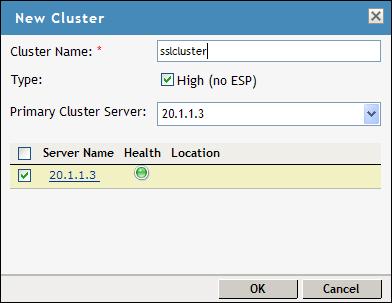
-
Specify a name for the cluster configuration. If you selected the server in the previous step, the IP address of the server is displayed in the drop-down list. If you have not selected a server in the previous step, you can now select the server or servers that you want to assign to this configuration.
-
Click .
-
Click the cluster configuration name that you created.
-
On the Cluster Details page, click .
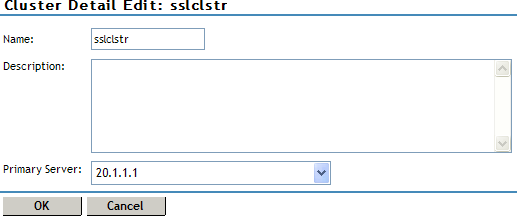
-
Fill in the following fields as required:
Name: Specifies the name of the SSL VPN server cluster configuration. You can modify the name of the cluster if you want.
Description: Specify a brief description of the SSL VPN cluster.
Primary Server: Specify the IP address of the primary server in the SSL VPN server cluster.
The section displays the IP address and other details of the SSL VPN servers that are assigned to the cluster.
-
Click .
The status icons for the configuration and the SSL VPN Server should turn green. It might take several seconds for the SSL VPN server to start and for the system to display a green light.