7.5 Executing Authorization Based Roles Policy During SAML 2.0 Service Provider Initiated Request
Access Manager service provider federation profiles do not currently allow control based on authorization policies. Usually the service providers enforce authorization rules. However, not all service providers have this flexibility. It is recommended not to trust the service provider to enforce such rules. You can now apply an authorization policy to a configured service provider to either allow or not to allow access to the service provider. The Identity Server will evaluate the service provider and will generate the successful/unsuccessful assertions.
Use Case: Company xyz.com uses a CRM application that is protected through the SAML 2.0 service provider. This application should only be accessible to the sales team and not to any other teams. Whenever a user accesses the application through the service provider, it redirects to the Identity Server for validating the user.
Figure 7-3 Executing Authorization Policy Based on Role
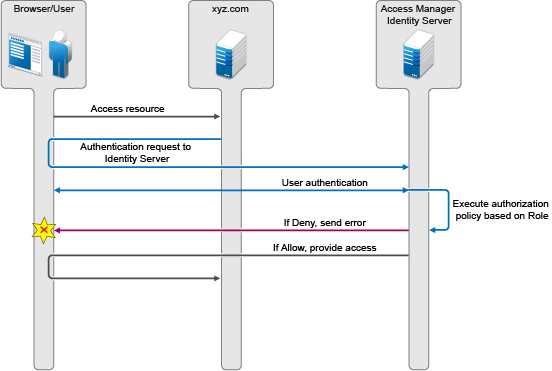
The Identity Server should authenticate the user and then check if the user is member of the sales team. If the user is a member, then the Identity Server sends a successful assertion to the service provider. Else, the Identity Server sends an error response to the service provider.
By default, the Identity Server executes these authorization policies after a user is authenticated during spsend. Adding the ALLOW_AUTH_POLICY_EXECUTION=false option in the nidp.properties file will not allow the Identity Server to execute the authorization policies.
If the authorization policy is to deny execution, the Identity Server sends the following message as part of an assertion response. <samlp:Status> <samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Responder"> <samlp:StatusCodeValue="urn:oasis:names:tc:SAML:2.0:status:RequestDenied" /> </samlp:StatusCode> <StatusMessage>Authorization is failed</StatusMessage> </samlp:Status>
For more information about, configuring a brokering for authorization of service providers see Section 12.3, Configuring a Brokering for Authorization of Service Providers.