4.1 Configuring for RADIUS Authentication
RADIUS enables communication between remote access servers and a central server. Secure token authentication through RADIUS is possible because Access Manager works with Novell Modular Authentication Service (NMAS) RADIUS software that can run on an existing NetWare server. Access Manager supports both PIN and challenge-and-response methods of token-based authentication. In other words, RADIUS represents token-based authentication methods used to authenticate a user, based on something the user possesses (for example, a token card). Token challenge-response is supported for two-step processes that are necessary to authenticate a user.
-
In the Administration Console, click Devices > Identity Server > Edit > Local > Classes.
-
Click New.
-
Specify a display name, then select RadiusClass or ProtectedRadiusClass from the drop-down menu.
-
Click Next.
-
Click New to add an IP address for the RADIUS server. You can add additional servers for failover purposes.
-
Click OK.
-
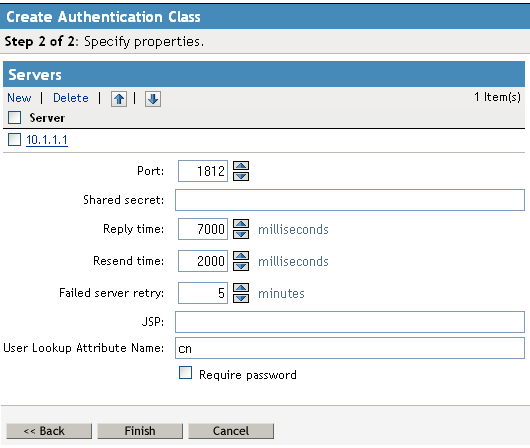
Fill in the following fields:
Port: The port of the RADIUS server.
Shared Secret: The RADIUS shared secret.
Reply Time: The total time to wait for a reply in milliseconds
Resend Time: The time to wait in milliseconds between requests.
Server Failure Retry: The time in milliseconds that must elapse before a failed server is retried.
JSP: Specify the name of the login page if you want to use something other than the default page. The filename must be specified without the JSP extension. The default page is used if nothing is specified.
User Look Attribute Name: Specify the LDAP attribute on which the user will be searched in the Radius server. CN is the default attribute.
Require Password: Select to require the user to also specify an LDAP password.
-
Click Finish.
-
Create a method for this class.
For instructions, see Section 3.3, Configuring Authentication Methods.
-
Create a contract for the method:
For instructions, see Section 3.4, Configuring Authentication Contracts.
If you want the user’s credentials available for Identity Injection policies and you did not enable the Require Password option, add the password fetch method as a second method to the contract. For more information about this class and method, see Section 4.6, Configuring Password Retrieval.
-
Update the Identity Server.