7.5 Configuring Communication Security
The communication security settings control the direct communication between the Identity Server and a trusted provider across the SOAP back channel. You can secure this channel with one of three methods:
Message Signing: This is the default method, and the Identity Server comes with a test signing certificate that is used to sign the back-channel messages. We recommend replacing this test signing certificate with a certificate from a well-known certificate authority. This method is secure, but it is CPU intensive. For information about replacing the default certificate, see Section 1.4.4, Managing the Keys, Certificates, and Trust Stores.
Mutual SSL: This method is probably the fastest method, and if you are fine-tuning your system for performance, you should select this method. However, it requires the exchange of trusted root certificates between the Identity Server and the trusted provider. This exchange of certificates is a requirement for setting up the trust relationship between the two providers. To verify that you have exchanged certificates, see Section 1.4.4, Managing the Keys, Certificates, and Trust Stores.
Basic Authentication: This method is as fast as mutual SSL and the least expensive because it doesn’t require any certificates. However, it does require the exchange of usernames and passwords with the administrator of the trusted provider, which might or might not compromise the security of the trusted relationship.
If your trusted provider is another Identity Server, you can use any of these methods, as long as your Identity Server and the trusted Identity Server use the same method. If you are setting up a trusted relationship with a third-party provider, you need to select a method supported by that provider.
For configuration information, see the following sections:
7.5.1 Configuring Communication Security for Liberty and SAML 1.1
Liberty and SAML 1.1 have the same security options for the SOAP back channel for both identity and service providers. You cannot configure the trust relationship of the SOAP back channel for the Identity Server and its Embedded Service Providers.
-
In the Administration Console, click Devices > Identity Servers > Edit > [Protocol].
For the protocol, select either Liberty or SAML 1.1.
-
Click the name of a provider.
-
On the Trust page, fill in the following field:
Name: Specify the display name for this trusted provider. The default name is the name you entered when creating the trusted provider.
For an Embedded Service Provider, the Name option is the only available option on the Trust page.
The Security section specifies how to validate messages received from trusted providers over the SOAP back channel. Both the identity provider and the service provider in the trusted relationship must be configured to use the same security method.
-
Select one of the following security methods:
Message Signing: Relies upon message signing using a digital signature.
Mutual SSL: Specifies that this trusted provider provides a digital certificate (mutual SSL) when it sends a SOAP message.
SSL communication requires only the client to trust the server. For mutual SSL, the server must also trust the client. For the client to trust the server, the server’s certificate authority (CA) certificate must be imported into the client trust store. For the server to trust the client, the client’s CA certificate must be imported into the server trust store.
Basic Authentication: Specifies standard header-based authentication. This method assumes that a name and password for authentication are sent and received over the SOAP back channel.
-
Send: The name and password to be sent for authentication to the trusted partner. The partner expects this password for all SOAP back-channel requests, which means that the name and password must be agreed upon.
-
Verify: The name and password used to verify data that the trusted provider sends.
-
-
Click OK twice.
-
Update the Identity Server.
7.5.2 Configuring Communication Security for a SAML 2.0 Identity Provider
The security settings control the direct communication between the Identity Server and the identity provider across the SOAP back channel.
-
In the Administration Console, click Devices > Identity Servers > Edit > SAML 2.0.
-
Click the name of an identity provider.
-
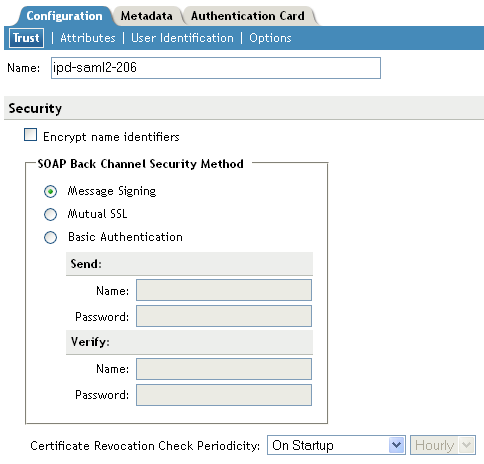
On the Trust page, fill in the following fields:
Name: Specify the display name for this trusted provider. The default name is the name you entered when creating the trusted provider.
The Security section specifies how to validate messages received from trusted providers over the SOAP back channel. Both the identity provider and the service provider in the trusted relationship must be configured to use the same security method.
Encrypt name identifiers: Specifies whether you want the name identifiers encrypted on the wire.
Select one of the following security methods:
-
Message Signing: Relies upon message signing using a digital signature.
-
Mutual SSL: Specifies that this trusted provider provides a digital certificate (mutual SSL) when it sends a SOAP message.
SSL communication requires only the client to trust the server. For mutual SSL, the server must also trust the client. For the client to trust the server, the server’s certificate authority (CA) certificate must be imported into the client trust store. For the server to trust the client, the client’s CA certificate must be imported into the server trust store.
-
Basic Authentication: Specifies standard header-based authentication. This method assumes that a name and password for authentication are sent and received over the SOAP back channel.
Send: The name and password to be sent for authentication to the trusted partner. The partner expects this password for all SOAP back-channel requests, which means that the name and password must be agreed upon.
Verify: The name and password used to verify data that the trusted provider sends.
Certificate Revocation Check Periodicity: Specifies if the certificate is valid or not. You can define periodicity to validate on start up, on assertion level, or set frequency to hourly/daily.
-
-
Click OK twice.
-
Update the Identity Server.
7.5.3 Configuring Communication Security for a SAML 2.0 Service Provider
The security settings control the direct communication between the Identity Server and the service provider across the SOAP back channel.
-
In the Administration Console, click Devices > Identity Servers > Edit > SAML 2.0.
-
Click the name of a service provider.
-
On the Trust page, fill in the following fields:
Name: Specify the display name for this trusted provider. The default name is the name you entered when creating the trusted provider.
The Security section specifies how to validate messages received from trusted providers over the SOAP back channel. Both the identity provider and the service provider in the trusted relationship must be configured to use the same security method.
Encrypt assertions: Specifies whether you want the assertions encrypted on the wire.
Encrypt name identifiers: Specifies whether you want the name identifiers encrypted on the wire.
Certificate Settings: All service providers use the default signing and encryption certificates of the identity provider. Specify custom certificates for a service provider as follows:
-
Identity Provider Signing Certificate: Select a certificate from the keystore and assign it to the service provider.
-
Identity Provider Encryption Certificate: Select a certificate from the keystore and assign it to the service provider.
NOTE:When you assign custom certificates to each service provider while configuring the identity server, ensure that you export these certificates and custom metadata to the service provider. To retrieve the metadata, click on the metadata link. (This link is available in the note on the Trust page).
For example, the default certificates will have the following default metadata URL: <IDP URL>/nidp/saml2/metadata.
The custom certificates will have the following custom metadata URL for a service provider: <IDP URL>/nidp/saml2/metadata?PID=<SP Entity ID >
-
Certificate Revocation Check Periodicity: Specifies if the certificate is valid or not. You can define periodicity to validate on start up, on assertion level, or set frequency to hourly/daily.
SOAP Back Channel Security Method: Select one of the following security methods.
-
Message Signing: Relies upon message signing using a digital signature.
-
Mutual SSL: Specifies that this trusted provider provides a digital certificate (mutual SSL) when it sends a SOAP message.
SSL communication requires only the client to trust the server. For mutual SSL, the server must also trust the client. For the client to trust the server, the server’s certificate authority (CA) certificate must be imported into the client trust store. For the server to trust the client, the client’s CA certificate must be imported into the server trust store.
-
Basic Authentication: Specifies standard header-based authentication. This method assumes that a name and password for authentication are sent and received over the SOAP back channel.
Send: The name and password to be sent for authentication to the trusted partner. The partner expects this password for all SOAP back-channel requests, which means that the name and password must be agreed upon.
Verify: The name and password used to verify data that the trusted provider sends.
-
-
Click OK twice.
-
Update the Identity Server.