1.1 Access Manager Component Deployment
The components of Access Manager include the Administration Console, Identity Server, SSL VPN, Access Gateway, and J2EE Agents.
Administration Console: Manages the Identity Server, SSL VPN, and Access Gateway.
Identity Server: Provides authentication functionality for the users and it uses the back-end LDAP servers to validate the user credentials.
Access Gateway: The Access Gateway protects Web servers and contacts Identity Server for users authentication. It also gets user attributes from Identity Server and passes on to the Web servers.
SSL VPN: Provides access to non-http servers. The SSL VPN depends on the Identity Server or the Access Gateway for validating the users.
J2EE Agents: Provides fine-grained access control to Java applications. Access Manager provides JBoss, WebLogic, and IBM WebSphere server agents for Java 2 Enterprise Edition (J2EE) application servers.
Depending on the number of users, you would need to create a cluster of components such as Identity Servers, Access Gateways, and SSL VPN Servers. Even if one node is sufficient to support all the load, NetIQ recommends to have at least two nodes in each component cluster to provide the failover support.
For more information, see Clustering and Fault Tolerance
in the NetIQ Access Manager 3.2 SP3 Setup Guide.
The following diagram illustrates how the Access Manager components are integrated with each other:
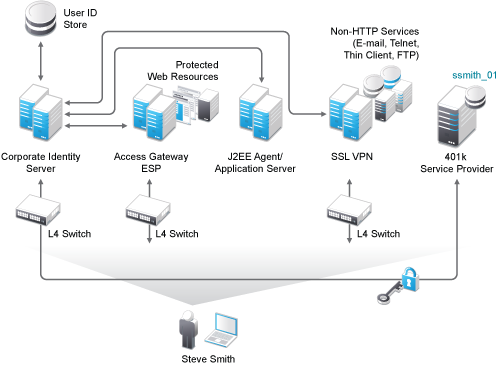
The recommended number of components nodes that are required are based on the concurrent user sessions. For more information, see Performance and Sizing Guidelines.
The following are the recommended configurations for the Access Manager components:
-
Enable Sticky-Bit on the Layer 4 (L4) switch.
Each L4 switch has a slightly different method and terminology for the sticky bit or persistence bind. This bit allows a client that has established a session to be directed to the same Identity Server or Access Gateway for all requests sent during the session. This minimizes the need to forward session information between Access Gateways or between Identity Servers and thus maximizes performance.
-
L4 health check recommendations:
-
Heartbeat URL checks should occur every 30 seconds.
-
The Access Manager devices should be removed from the service after three failures.
For more information, see
Configuration Tips for the L4 Switch
in the NetIQ Access Manager 3.2 SP3 Setup Guide.
-
-
Ensure that the LDAP time out setting in the Identity Server, Active Directory (if using it as a user store), Web servers, and the L4 switch are all set to the same value. Based on an average user session, the recommended value is 15-20 minutes.
-
To improve the performance of Identity Servers, ensure that Identity Server can perform a reverse lookup on the LDAP user store’s IP address. If the LDAP user store’s IP addresses are not part of the DNS server, make an entry in the hosts file of the Identity Server.
-
Set the TCP idle time in the Access Gateway lower than the LDAP time out to clear the connection table in the Access Gateway. If this time is not set, Linux fills the connection table making it almost impossible to login if the sessions are not cleared.