1.1 Product Overview
LDAP Proxy is designed to analyze the network traffic from various interfaces and regulate requests and responses among LDAP server directories, based on policies. LDAP Proxy has the following features:
-
Load Balancing: LDAP Proxy uses dynamic load balancing algorithms to distribute the load across various servers. The load balancing algorithms use different parameters such as active connections, server response time, and capability. Balance is achieved by grouping at least two back-end servers with the same tree structure into a back-end server group.
-
Failover Mechanism: LDAP Proxy performs periodic health checks to detect unavailable or slow back-end servers.
A server is marked unavailable or slow based on any of the following conditions:
-
The connection attempt returns an error
-
The connection has timed out
-
The directory server is unhealthy
-
The proxy receives a connection error on an active connection while sending a request
When a back-end server is unavailable, LDAP Proxy switches active connections to an available back-end server in the server group. Requests that are partially serviced are also routed to a new back-end server, and an LDAP busy result code (51) is sent for the partially serviced requests.
Backing up of LDAP Proxy is achieved by configuring high availability for the LDAP Proxy. For more information, see Section A.0, Configuring a Linux High Availability Cluster for NetIQ Ldap Proxy.
-
-
Identity-based Policies: LDAP Proxy provides a simple but powerful set of policies that allows you to implement a greater level of access control over incoming LDAP requests.
-
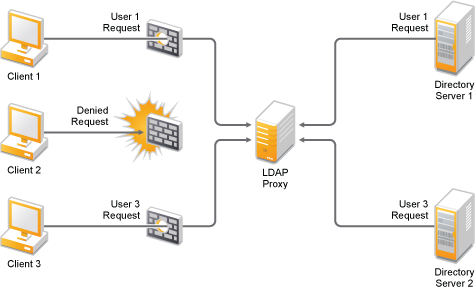
The Network Restriction policy allows you to configure the proxy server as a firewall. You can use this policy to restrict requests based on clients’ network parameters, such as IP address and network address.
Figure 1-1 LDAP Proxy as a Directory Firewall
-
The Connection Route policy enables you to route an incoming connection to an appropriate back-end server group. It also determines the identity of an incoming connection and applies required policies before forwarding the processed connection to the associated server group.
-
The Search Restriction policy facilitates re-encoding of incoming search requests. This helps to implement actions such as hiding containers, restricting search attributes, and restricting the search filter (such as CN=*).
-
The Operation Restriction policy allows you to restrict LDAP operations such as Bind, Search, Add, Modify, Delete, Modify DN, and Compare. This restriction helps to achieve read-only and search-only functionality for a server group.
-
The Map Schema policy enables schema compatibility. This helps an application to work with any LDAP directory and allows you to obtain multiple views of the same Directory Information Tree, based on identity.
For more information about each of these policies, refer to NetIQ LDAP Proxy 1.6 Administration Guide.
-
-
Live Monitoring: LDAP Proxy uses an Eclipse-based client tool to provide a graphical view of the activities on the proxy server and back-end directory servers. This helps you to monitor the live LDAP traffic, load, and performance of different LDAP operations.
For more information about configuring the events to be monitored by using the NetIQ LDAP Proxy GUI, refer to Configuring Monitoring and Trending Activities.
-
Trending: LDAP Proxy uses an Eclipse-based client tool to analyze and view the trends of LDAP traffic. It also helps you to analyze the load and performance of the proxy server and back-end directory servers. You can analyze this historical trend data for any given time duration for different LDAP operations. The analyzed data is generated and displayed in an informative and customizable graph.
For more information about configuring the log files for trending, refer to Configuring Monitoring and Trending Activities.
-
Auditing: LDAP Proxy allows you to audit the activities on the proxy and back-end directory servers. This helps you to track session details, LDAP policies, and back-end activities. It supports the traditional method of auditing as well as the XDAS-standards based auditing.
-
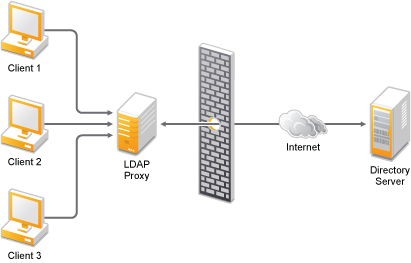
Forward Proxy: LDAP Proxy allows you to configure the proxy server as a forward proxy. For instance, there might be a legacy LDAP application that communicates directly to the back-end LDAP server over a clear text channel, compromising security. LDAP Proxy overcomes this limitation by securing the connection between the proxy server and back-end directory servers.
Figure 1-2 LDAP Proxy as a Forward Proxy
-
Chaining: LDAP Proxy provides a chaining feature that can be leveraged by a back-end server or LDAP client that does not support chaining. This feature also ensures the security of back-end server information.
-
Request Routing: LDAP Proxy provides you with the latest data for any directory server. In a distributed directory environment, all servers might not have the latest copy of the data because of a network failure or synchronization delay. LDAP Proxy overcomes this limitation by tracking data modifications across different servers.