6.1 Installing and Configuring the User Application WAR
NOTE:For WebSphere 6.1, the installation program requires the Java 2 Platform Standard Edition Development Kit version 1.5 JDK from IBM. For WebSphere 7.0, the installation program requires the 1.6 JDK from IBM. If you use a different version, the installation procedure does not successfully configure the User Application WAR file. The installation appears to succeed, but you encounter errors when trying to start the User Application.
-
Navigate to the directory containing your installation files.
-
You must apply the unrestricted policy files to the IBM JDK. You can refer to your WebSphere documentation for a link to these files from IBM and instructions for applying them. Apply these files to your IBM JDK environment before proceeding any further with the installation.
Without these unrestricted policy files, an error will occur that says
Illegal key size
. The root cause of this problem is the lack of unrestricted policy files, so be sure to use the correct IBM JDK. -
Launch the installer using the IBM Java environment, as shown below:
Solaris
$ /opt/WS/IBM/WebSphere/AppServer/java/bin/java -jar IdmUserApp.jar
Windows
C:\WS\IBM\WebSphere\AppServer\java\bin\java -jar IdmUserApp.jar
When the installation program launches, you are prompted for the language.
-
Use the following information to select the language, confirm the license agreement, and select the Application Server platform:
Installation Screen
Description
Roles Based Provisioning Module (RBPM) for Novell Identity Manager
Select the language for the installation program. The default is English.
License Agreement
Read the License Agreement, then select .
Application Server Platform
Select
If the User Application WAR file is in a different directory from the installer, the installer prompts for the path to the WAR.
If the WAR is in the default location, you can click . Or, to specify the location of the WAR file, click and select a location.
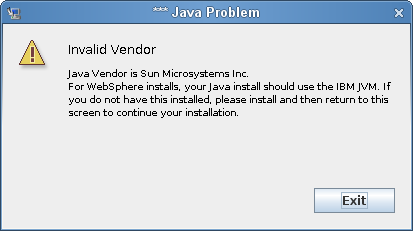
When you’re installing on WebSphere, you need to launch the installation program by using the IBM Java environment. If you select WebSphere as the application server, and do not use IBM’s Java to launch the installation, you will see a pop-up error message, and the installation will terminate:
-
Use the following information to select the installation type, choose an install folder, and configure the database:
Installation Screen
Description
Installation Type
: Select this option to install the Roles Based Provisioning Module. This is the only installation type supported with this release.
Choose Install Folder
Specify where you want the installer to put the files.
Database Platform
Select the database platform. The database and JDBC driver must already be installed. For WebSphere, the options include the following:
-
MySQL
-
Oracle (supports Oracle 10g and 11g only; support for Oracle 9i has been removed)
-
Microsoft SQL Server
-
IBM DB2 (supports version 9.5 only; support for version 9.1 has been removed)
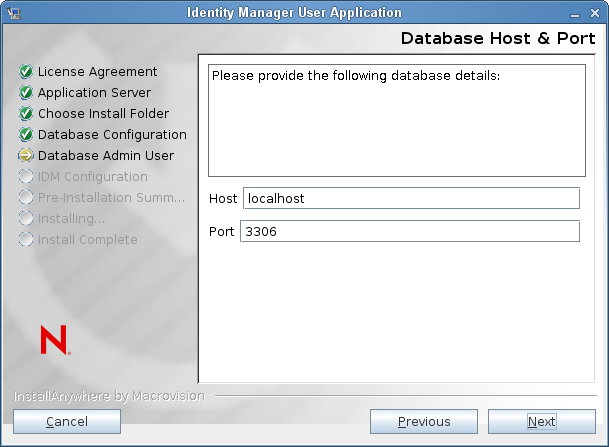
Database Host and Port
: Specify the database server’s hostname or IP address. For a cluster, specify the same hostname or IP address for each member of the cluster.
: Specify the database’s listener port number. For a cluster, specify the same port for each member of the cluster.
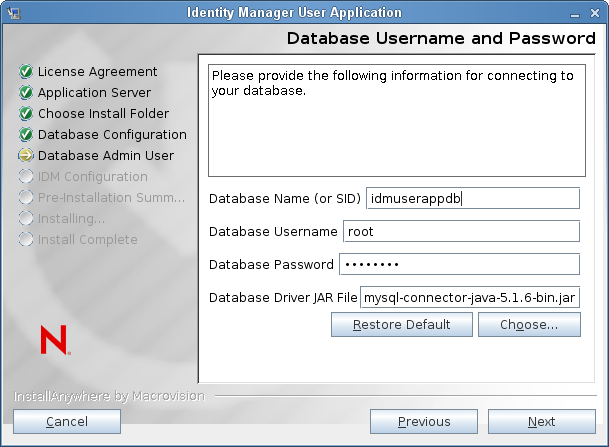
Database Username and Password
(or SID): For MySQL, MS SQL Server, or PostgreSQL provide the name of your preconfigured database. For Oracle, provide the Oracle System Identifier (SID) that you previously created. For a cluster, specify the same database name or SID for each member of the cluster.
name: Specify the database user. For a cluster, specify the same database user for each member of the cluster.
: Specify the database password. For a cluster, specify the same database password for each member of the cluster.
Provide the Thin Client JAR for the Database Server. This is required.
IMPORTANT:The browse button for the field allows you to select only one (1) jar. For DB2, you must provide two (2) jars:
-
db2jcc.jar
-
db2jcc_license_cu.jar
Therefore, you can select one JAR, but will have to manually enter the second one using the correct file separator for the operating system that the install program is running on. Alternatively, you can manually enter both entries.
For example, on Windows:
c:\db2jars\db2jcc.jar;c:\db2jars\db2jcc_license_cu.jar
For example, on Solaris and Linux:
/home/lab/db2jars/db2jcc.jar:/home/lab/db2jcc_license_cu.jar
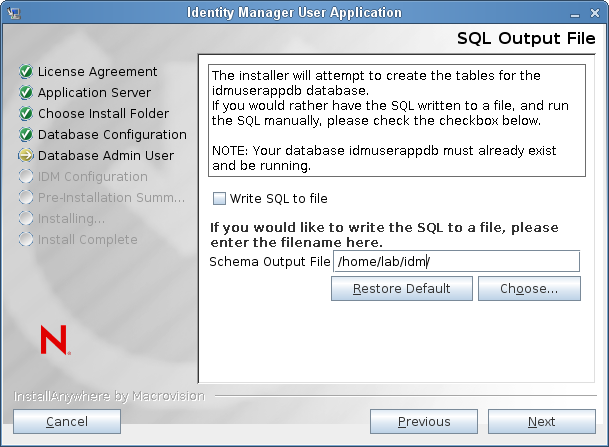
SQL Output File
In this release, the database tables can be created during the User Application installation, rather than when the Application Server starts (as in previous releases).
The SQL Output File screen gives you the option to create a schema file, which the Database Administrator can use to create the tables, instead of having the Installation program create the tables.
If you want to generate a schema file, select the checkbox and provide a name for the file in the field.
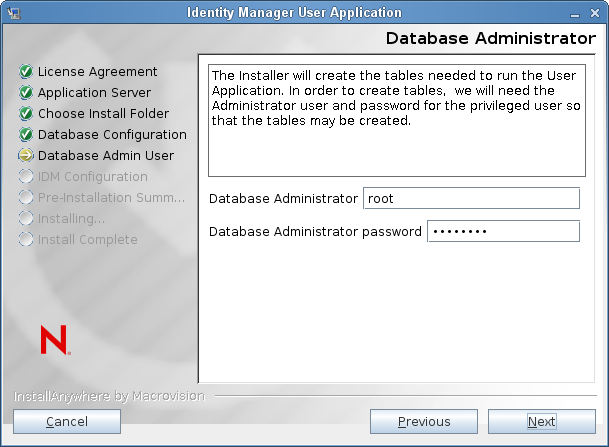
Database Administrator
This screen is pre-populated with the same username and password from the Database Username and Password page. If the database user that was specified earlier does not have enough permissions to create tables in the Database Server, then a different user ID that has the necessary rights needs to be entered.
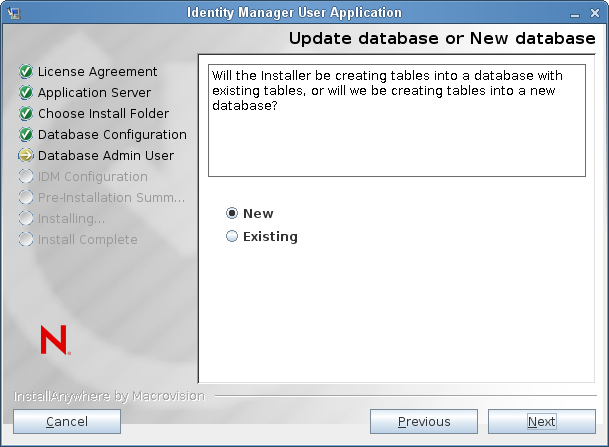
Update database or New database
If the database that will be used is new or empty, then select the button. If the database is an existing one from a previous installation, select the button.
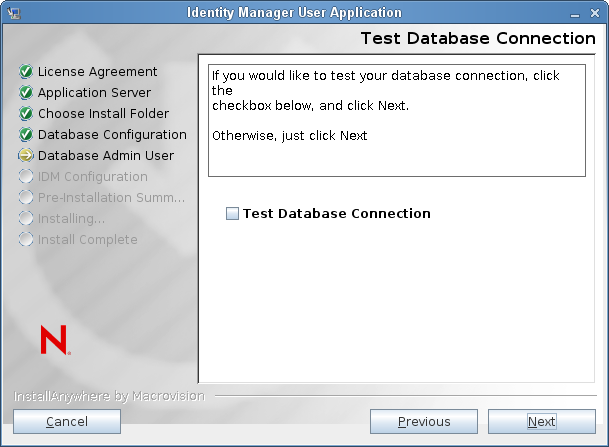
Test Database Connection
To confirm that the information provided in the previous screens was correct, you can test the database connection by selecting the checkbox:
-
-
Use the following information to configure Java and IDM, as well as audit settings and security.
Installation Screen
Description
Java Install
Specify the Java root install folder. The Java Install provides the path to Java based on your JAVA_HOME environment variable and gives you the option to correct it:
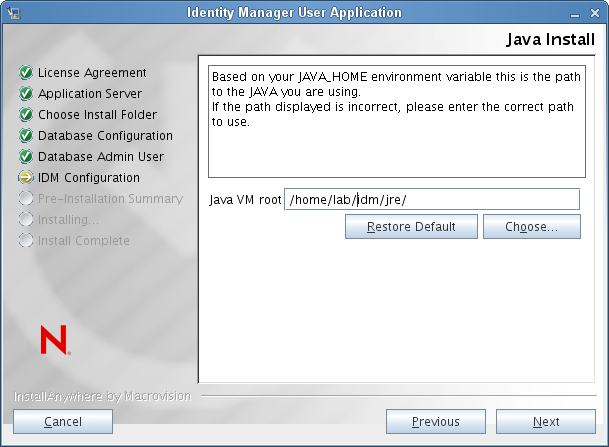
At this point, the Installation program also validates that the Java selected is the correct one for the Application Server selected. In addition, it validates that it can write to the cacerts in the JRE that was specified.
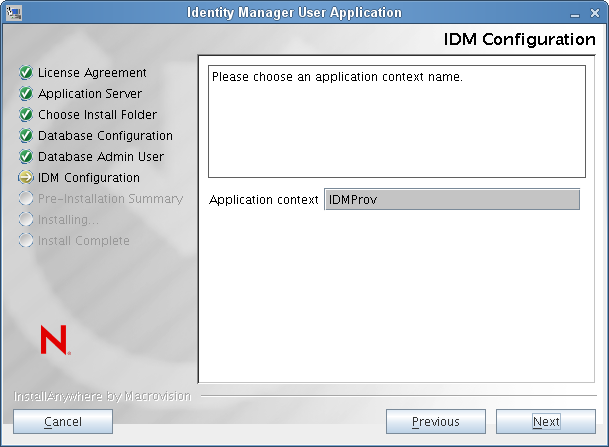
IDM Configuration
Select the type of application server configuration:
-
Select if this installation is on a single node that is not part of a cluster
If you select and decide you need a cluster later, then you must reinstall the User Application.
-
Select if this installation is part of a cluster
: The name of the application server configuration, the name of the application WAR file, and the name of the URL context. The installation script creates a server configuration and by default names the configuration based on . Make a note of the application name and include it in the URL when you start the User Application from a browser.
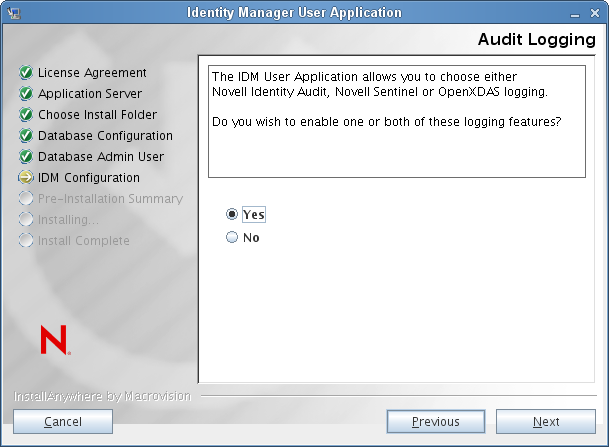
Audit Logging
To enable logging, click . To disable logging, click .
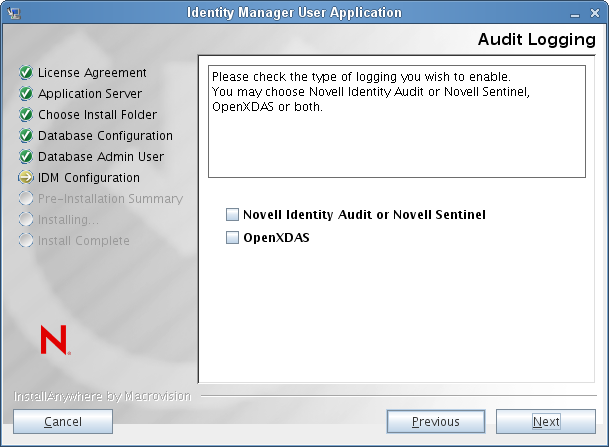
The next panel prompts you to specify the type of logging. Choose from the following options:
-
: Enables Novell® Audit Logging for the User Application.
-
: Events are logged to your OpenXDAS logging server.
For more information on setting up logging, see the .
Novell Audit
: If you enable logging, specify the hostname or IP address for the server. If you turn logging off, this value is ignored.
: Specify the directory for the logging cache.
Security - Master Key
: Allows you to Import an existing master key. If you choose to import an existing encrypted master key, cut and paste the key into the install procedure window.
: Creates a new master key. After you finish the installation, you must manually record the master key as described in Section 9.1, Recording the Master Key.
The installation procedure writes the encrypted master key to the master-key.txt file in the installation directory.
Reasons to import an existing master key include:
-
You are moving your installation from a staging system to a production system and want to keep access to the database you used with the staging system.
-
You installed the User Application on the first member of a cluster and are now installing on subsequent members of the cluster (they require the same master key).
-
Because of a failed disk, you need to restore your User Application. You must reinstall the User Application and specify the same encrypted master key that the previous installation used. This gives you access to the previously stored encrypted data.
-
-
Click to display the Roles Based Provisioning Module Configuration panel. (If you are not prompted for this information, you might not have completed the steps outlined in Section 2.5, Installing the Java Development Kit.)
The default view of the Roles Based Provisioning Module Configuration panel shows these six fields:
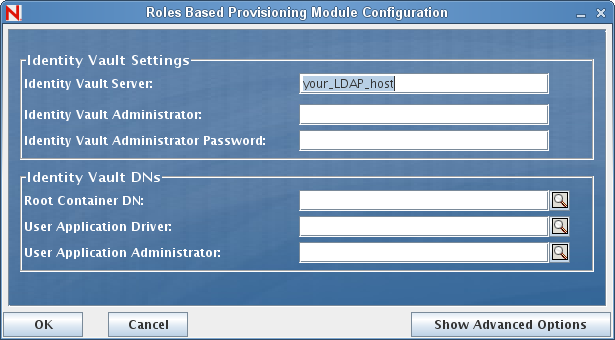
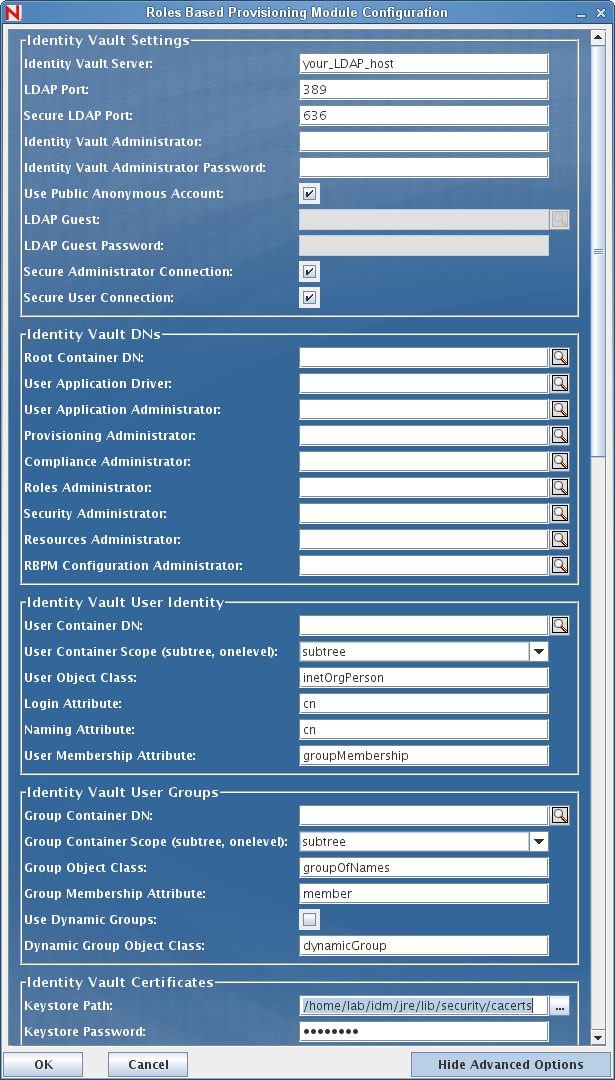
The Installation program will take the value from the Root Container DN and apply it to the following values:
-
User Container DN
-
Group Container DN
The Installation program will take the value from the User Application Administrator fields and apply it to the following values:
-
Provisioning Administrator
-
Compliance Administrator
-
Roles Administrator
-
Security Administrator
-
Resources Administrator
-
RBPM Configuration Administrator
If you want to be able to specify these values explicitly, you can click the button and change them:
-
-
Use the following information to complete the installation.
Installation Screen
Description
User Application Configuration
The User Application install enables you to set User Application configuration parameters. Most of these parameters are also editable with configupdate.sh or configupdate.bat after installation; exceptions are noted in the parameter descriptions.
For a cluster, specify identical User Application configuration parameters for each member of the cluster.
See Section A.0, IDM User Application Configuration Reference for a description of each option.
Pre-Installation Summary
Read the Pre-Installation Summary page to verify your choices for the installation parameters.
If necessary, use to return to earlier installation pages to change installation parameters.
The User Application configuration page does not save values, so after you re-specify earlier pages in the installation, you must re-enter the User Application configuration values. When you are satisfied with your installation and configuration parameters, return to the Pre-Install Summary page and click .
Install Complete
Indicates that the installation is finished.
6.1.1 Viewing Installation Log Files
If your installation completed without error, continue with Section 6.2.1, Adding User Application Configuration Files and JVM System Properties.
If the installation issued errors or warnings, review the log files to determine the problems:
-
Identity_Manager_User_Application_InstallLog.log holds results of the basic installation tasks.
-
Novell-Custom-Install.log holds information about the User Application configuration done during installation.