1.1 Identity Manager and You
NetIQ Identity Manager is a system software product that your organization uses to securely manage the access needs of its user community. If you are a member of that user community, you benefit from Identity Manager in a number of ways. For example, Identity Manager enables your organization to:
-
Give users access to the information (such as group org charts, department white pages, or employee lookup), as well as roles and resources (such as equipment or accounts on internal systems) that they need, right from day one
-
Synchronize multiple passwords into a single login for all your systems
-
Modify or revoke access rights instantly when necessary (such as when someone transfers to a different group or leaves the organization)
-
Support compliance with government regulations
To bring these benefits directly to you and your team, the Identity Manager User Application provides a user interface that you can use from your Web browser.
1.1.1 Introducing the Identity Manager User Application
The Identity Manager User Application is your view into the information, roles, resources, and capabilities of Identity Manager. Your system administrator determines the details of what you can see and do in the User Application. Typically, this includes:
-
Identity self-service, which enables you to:
-
Display organization charts
-
Report applications associated with a user if you are an administrator (requires the Roles Based Provisioning Module for Identity Manager)
-
Edit the information in your profile
-
Search a directory
-
Change your password, password challenge response, and password hint
-
Review your password policy status and password synchronization status
NOTE:Identity Manager provides these features for administrators only. They are not meant for end users.
-
Create accounts for new users or groups (if you are authorized)
-
-
Roles, which enable you to:
-
Request role assignments and manage the approval process for role assignment requests
-
Check the status of your role requests
-
Define roles and role relationships
-
Define separation of duties (SoD) constraints and manage the approval process in situations where a user requests an override to a constraint
-
Browse the Role Catalog
-
Look at detailed reports that list the roles and separation of duties constraints defined in the catalog, as well as the current state of role assignments, separation of duties exceptions, and user entitlements
-
-
Resources, which enable you to:
-
Request resource assignments and manage the approval process for resource assignment requests
-
Check the status of your resource requests
-
Browse the Resource Catalog
-
-
Workflow processes, which enable you to:
-
Request custom workflow processes
-
Check the approval of your role, resource, and process requests
-
Work on tasks assigned to you for approving other requests
-
Perform process requests and approvals as a proxy or delegate for someone else
-
Assign someone else to be your proxy or delegate (if you are authorized)
-
Manage all of these request and approval features for your team (if you are authorized)
-
-
Compliance, which enables you to:
-
Request user profile attestation processes
-
Request separation of duties (SoD) attestation processes
-
Request role assignment attestation processes
-
Request user assignment attestation processes
-
IMPORTANT:The User Application is an application and not a framework. The areas within the User Application that are supported to be modified are outlined within the product documentation. Modifications to areas not outlined within the product documentation are not supported.
1.1.2 The Big Picture
Figure 1-1 The Identity Manager User Application Provides the User Interface to Identity Manager
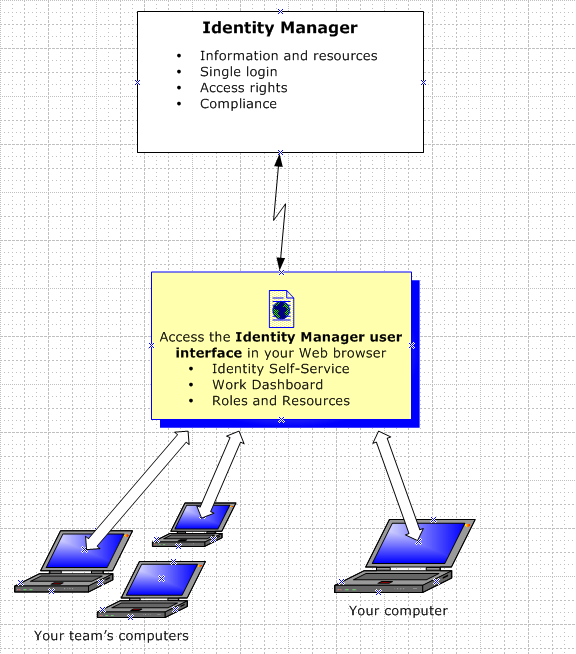
1.1.3 Typical Uses
Here are some examples of how people typically use the Identity Manager User Application within an organization.
Working with Identity Self-Service
-
Ella (an end user) recovers her forgotten password through the identity self-service features when logging in.
By default, Identity Manager uses Self Service Password Reset (SSPR) to allow users to modify their passwords. However, the identity applications can use other methods for managing forgotten passwords. For more information, see
Configuring Forgotten Password Management
in the NetIQ Identity Manager Setup Guide. -
Erik (an end user) performs a search for all employees who speak German at his location.
-
Eduardo (an end user) browses the organization chart, finds Ella, and clicks the e-mail icon to send a message to her.
Working with Roles and Resources
-
Maxine (a Role Manager) creates the Nurse and Doctor business roles and the Administer Drugs and Write Prescriptions IT roles. Maxine creates several resources that are needed for these roles, and associates the resources with the roles.
-
Maxine (a Role Manager) defines a relationship between the Nurse and Administer Drugs roles, specifying that the Nurse role contains the Administer Drugs role. Max also defines a relationship between the Write Prescriptions and Doctor roles, specifying that the Doctor role contains the Write Prescriptions role.
-
Chester (a Security Officer) defines a separation of duties constraint that specifies that a potential conflict exists between the Doctor and Nurse roles. This means that ordinarily the same user should be not assigned to both roles at the same time. In some circumstances, an individual who requests a role assignment may want to override this constraint. To define a separation of duties exception, the individual who requests the assignment must provide a justification.
-
Ernest (an end user) browses a list of roles available to him, and requests assignment to the Nurse role.
-
Amelia (an approver) receives notification of an approval request via e-mail (which contains a URL). She clicks the link, is presented with an approval form, and approves it.
-
Arnold (a Role Manager) requests that Ernest be assigned to the Doctor role. He is notified that a potential conflict exists between the Doctor role and Nurse role, to which Ernest has already been assigned. He provides a justification for making an exception to the separation of duties constraint.
-
Edward (a separation of duties approver) receives notification of a separation of duties conflict via e-mail. He approves Arnold’s request to override the separation of duties constraint.
-
Amelia (an approver) receives notification of an approval request for the Doctor role via e-mail. She approves Arnold’s request to assign Ernest to the Doctor role.
-
Bill (a Role Auditor) looks at the SoD Violations and Exceptions Report and sees that Ernest has been assigned to both the Doctor and Nurse roles. In addition, he sees that Ernest has been assigned the resources associated with these roles.
Working with Process Requests
-
Ernie (an end user) browses a list of resources available to him, and requests access to the Siebel* system.
-
Amy (an approver) receives notification of an approval request via e-mail (which contains a URL). She clicks the link, is presented with an approval form, and approves it.
-
Ernie checks on the status of his previous request for Siebel access (which has now gone to a second person for approval). He sees that it is still in progress.
-
Amy is going on vacation, so she indicates that she is temporarily unavailable. No new approval tasks are assigned to her while she is unavailable.
-
Amy opens her approval task list, sees that there are too many for her to respond to in a timely manner, and reassigns several to co-workers.
-
Pat (an administrative assistant, acting as a proxy user for Amy) opens Amy’s task list and performs an approval task for her.
-
Max (a manager) views the task lists of people in his department. He knows that Amy is on vacation, so he reassigns tasks to others in his department.
-
Max initiates a request for a database account for someone in his department who reports directly to him.
-
Max assigns Dan to be an authorized delegate for Amy.
-
Dan (now a delegated approver) receives Amy’s tasks when she is unavailable.
-
Max engages an unpaid intern, who should not be entered into the HR system. The system administrator creates the user record for this intern and requests that he be given access to Notes, Active Directory*, and Oracle*.
Working with Compliance
-
Maxine (a Role Manager) creates the Nurse and Doctor business roles and the Administer Drugs and Write Prescriptions IT roles.
-
Maxine (a Role Manager) defines a relationship between the Nurse and Administer Drugs roles, specifying that the Nurse role contains the Administer Drugs role. Max also defines a relationship between the Write Prescriptions and Doctor roles, specifying that the Doctor role contains the Write Prescriptions role.
-
Chester (a Security Officer) defines a separation of duties constraint that specifies that a potential conflict exists between the Doctor and Nurse roles. This means that ordinarily the same user should be not assigned to both roles at the same time. In some circumstances, an individual who requests a role assignment may want to override this constraint. To define a separation of duties exception, the individual who requests the assignment must provide a justification.
-
Arnold (a Role Manager) requests that Ernest be assigned to the Doctor role. He is notified that a potential conflict exists between the Doctor role and Nurse role, to which Ernest has already been assigned. He provides a justification for making an exception to the separation of duties constraint.
-
Philip (a Compliance Module Administrator) initiates a role assignment attestation process for the Nurse role.
-
Fiona (an attester) receives notification of the attestation task via e-mail (which contains a URL). She clicks the link and is presented with an attestation form. She provides an affirmative answer to the attestation question, thereby giving her consent that the information is correct.
-
Philip (a Compliance Module Administrator) initiates a new request for a user profile attestation process for users in the Human Resources group.
-
Each user in the Human Resources group receives notification of the attestation task via e-mail (which contains a URL). Each user clicks the link and is presented with an attestation form. The form gives the user an opportunity to review the values for various user profile attributes. After reviewing the information, each user answers the attestation question.