1.2 Identity Manager Reporting Architecture
The following diagram shows the components of the Identity Manager reporting architecture:
Figure 1-1 Reporting Architecture
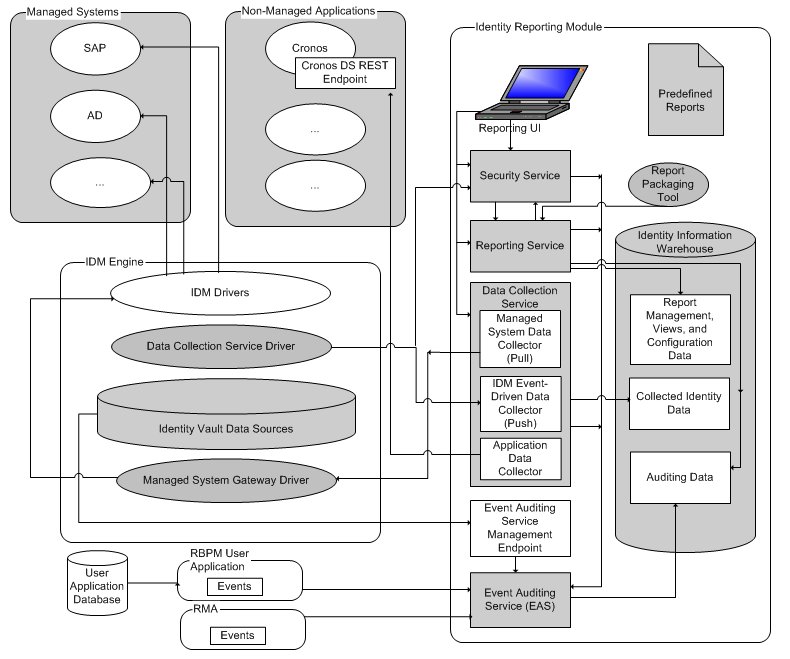
Each of the major components is described below:
Table 1-1 Major Components of the IDM Reporting Architecture
|
Component |
Description |
|---|---|
|
Identity Reporting Module |
Browser-based application that generates reports by making calls to the Reporting Service. |
|
Predefined Reports |
Set of predefined report definitions you can use to generate reports. You can also import custom reports you define in a third-party tool. For details about the predefined reports, see Using Identity Manager Reports. |
|
Report Packaging Tool |
Facilitates the process of creating new reports. You can customize reports in iReport and use the Report Packaging Tool to package them for use within the Reporting Module. |
|
Reporting Service |
Service that retrieves the data needed to generate reports from the Identity Information Warehouse, which contains all report management information (such as report definitions and schedules), database views, and configuration information required for reporting To produce reports, the Reporting Service invokes the JasperReports engine, which compiles and executes report definitions according to schedules that the Report Administrator defines. |
|
Identity Information Warehouse |
Repository for the following kinds of information:
The Identity Information Warehouse stores its data in the Security Information and Event Management (SIEM) database. |
|
Data Collection Service |
Service that collects information from various sources within an organization. The Data Collection Service includes three subservices:
|
|
Data Collection Service Driver |
Driver that captures changes to objects stored in an Identity Vault, such as accounts, roles, resources, groups, and team memberships. The Data Collection Service Driver registers itself with the Data Collection Service and pushes change events (such as data synchronization, add, modify, and delete events) to the Data Collection Service. The information that the driver captures records changes to these objects:
|
|
Managed System Gateway Driver |
Driver that collects information from managed systems. To retrieve the managed system data, the driver queries the Identity Vault. The driver retrieves the following information:
|
|
Security Service |
Service that controls access to all other services within the Reporting Module. The Security Service includes these key components:
|
|
Event Auditing Service (EAS) |
Captures log events associated with actions performed in several NetIQ products, including the Reporting Module, the Roles Based Provisioning Module (RBPM), Catalog Administrator, and eDirectory. These events are stored in the public schema within the warehouse. You have the option to forward these events to Sentinel. If you choose to forward events, you can then use Sentinel to create a more holistic view of all the activity within your enterprise. Sentinel lets you assimilate logs and other security information from various heterogeneous input sources, giving you visibility and accountability into the various activities within the enterprise. |
|
Identity Vault Data Sources |
Repositories for identity information. The Reporting Module allows you to report on state information in the Identity Vault, such as which users have been provisioned with particular resources, or which users have been assigned to particular roles. You can report on current and past data from the Identity Vault. The Identity Vault Data Sources page allows you to specify which Identity Vaults you want to report on, and provide information about where the Reporting Module can find these vaults. You can include data sources for one or more Identity Vaults on the Identity Vault Data Sources page. |
|
Managed Systems |
A system in an enterprise that is connected to the Identity Vault with an Identity Manager driver. The Reporting Module allows you to report on state information about the managed systems. For example, the reports allow you to determine that a particular user known to the Identity Vault exists in Active Directory. The Reporting Module allows you to report on current and past data from managed systems. |
|
Applications |
Any non-managed application running in an enterprise. A non-managed application is an application that is not connected to the Identity Vault. To include information from a non-managed application, implement a REST endpoint as outlined in the REST API documentation. Also configure a custom data source for the application on the Non-Managed Application Data Sources page within the Reporting Module, as described in the REST API documentation. The Reporting installation program deploys a special API WAR file, rptdoc.war, which contains the documentation of REST services needed for reporting. For more information accessing the REST API documentation, see Section 12.0, REST Services for Reporting. |
The following diagram shows the components of the EAS architecture:
Figure 1-2 EAS Architecture
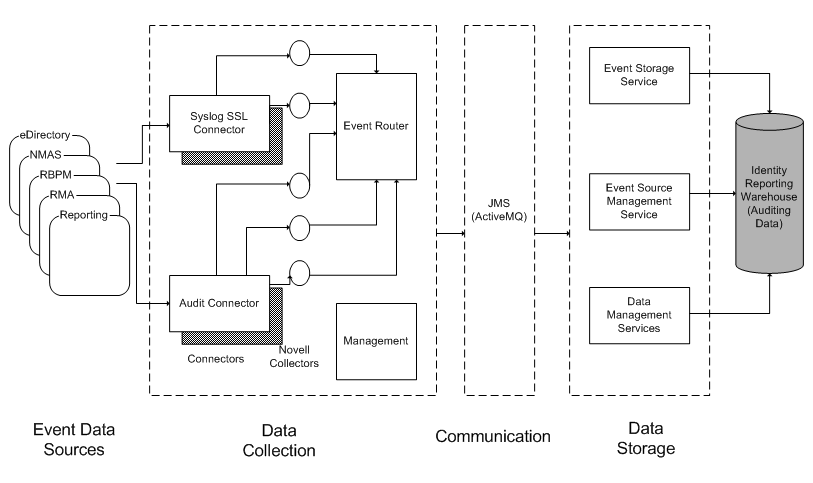
EAS provides these connectors for capturing events from various NetIQ data sources:
-
Syslog SSL Connector
-
Syslog UDP Connector
-
Audit Connector
Different NetIQ applications use different connectors:
-
You can configure the Catalog Administrator to use the Audit Connector or the Syslog SSL Connector.
-
You can configure Identity Manager and eDirectory to use the Audit Connector or the Syslog SSL Connector.
-
The RBPM uses the Audit Connector.
When you configure EAS to work with the Reporting Module, provide ports for these connectors on the Auditing page within the user interface for the Reporting Module.