2.19 Configuring Stronger Ciphers for SSL Communication
You can configure Identity Manager in Suite B mode to enhance the security requirements of your Identity Manager environment.
Suite B requirement originated from the National Security Agency (NSA) to specify a cryptographic interoperability strategy. Suite B includes the following cryptographic algorithms:
-
Encryption based on the Advanced Encryption Standard (AES) using 128-bit keys or 256-bit keys
-
Digital signatures with the Elliptic Curve Digital Signature Algorithm (ECDSA) on P-256 and P-384 curves
-
Key exchange, either pre-shared or dynamic, using the Elliptic Curve Diffie-Hellman (ECDH) method on P-256 and P-384 curves
-
Hashing (digital fingerprinting) based on the Secure Hash Algorithm-2 (SHA-256 and SHA-384)
NOTE:Suite B standard is subject to change. NSA may change their recommendations in future. Suite B support in Identity Manager is based on our interpretation of the NSA recommendations. For more information about Suite B, see Suite B Cryptography.
2.19.1 Prerequisites
To configure Identity Manager in Suite B mode, your environment must meet the following conditions:
-
eDirectory 9.0.2 or later is installed as an Identity Vault
-
TLS 1.2 is enforced as a communication protocol
-
Suite B connection parameter is specified in the driver, Remote Loader, or Fan-Out configuration to enforce the Suite B specification for a secured communication
NOTE:In Suite B mode, the SSL connection is restricted to accept only Suite B supported certificates. If a certificate is expired or invalid, the handshake fails and the communication is not established. For generating Suite B certificates, see “Creating a Server Certificate Object” in the NetIQ eDirectory Administration Guide.
The following table lists the requirements as specified by Suite B:
|
Requirement |
Description |
|---|---|
|
Protocol |
TLS 1.2 is supported in Suite B mode. |
|
Public keys |
The public key for certificates must be a minimum size of EC 256 bits. |
|
Signature algorithm |
The signature algorithm for certificates must be a minimum size of ECDSA 256 bits (curve P256) and SHA256. |
|
Hash algorithm |
The hash algorithm must have the minimum size of SHA256. |
|
Cipher specification |
The following ciphers are supported for Suite B mode:
To use ciphers with stronger signature and hash algorithms, the certificates of server key file must contain similar or stronger signature and hash algorithms. Suite B supports two levels of cryptographic security: 128 bit and 192 bit. The level defines a minimum strength that all cryptographic algorithms must provide. In Suite B 192-bit processing mode, the supported cipher suite is TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384. |
2.19.2 Configuring the Settings for Suite B Mode
To meet the requirements specified by Suite B, you must specify the appropriate settings in the Identity Manager components. This section provides information about those settings.
Engine
To configure the Identity Manager engine in Suite B mode, you must set the Suite B configuration option enforceSuiteB = true in the driver configuration by using Designer or iManager.
With the use of stronger ciphers in Suite B mode, passwords managed by the engine such as named password, application password, and Remote Loader password will be re-encrypted when they are used for the first time after upgrading the engine to 4.6 version. On an upgraded engine, the existing encrypted attribute values in the driver cache file are not re-encrypted with stronger ciphers because they are removed from the TAO file when the event is processed. However, when new encrypted attributes are stored in the cache, they are encrypted with AES 256-bit keys.
Engine and Remote Loader Communication
To make the engine and Remote Loader communication compliant with Suite B mode, set the Suite B configuration option enforceSuiteB = true in the driver configuration. The Suite B communication can also be configured in the Remote Loader configuration file for a driver by setting enforceSuiteB to true. For more information, see Configuring the Remote Loader and Drivers in the NetIQ Identity Manager Driver Administration Guide.
Suite B mode is disabled by default. When you enable it, Identity Manager automatically uses TLS 1.2 or later for communication. If you try to connect a Suite B-enabled engine with a Remote Loader that does not support TLSv1.2, the handshake fails and the communication is not established. For example, Remote Loader 4.5.3, which does not support TLS v1.2.
Engine and Fan-Out Agent Communication
For enabling the Suite B communication, manually include netiq.fanoutagent.connection.enforceSuiteB=true parameter in the Fan-Out Agent configuration file. You also need to specify enforceSuiteB = true in the driver configuration. Suite B configuration is supported with driver version 1.0.1.1. For more information, see the NetIQ Identity Manager Driver for JDBC Fanout Implementation Guide.
Identity Manager Drivers
Along with the configuration changes discussed in the earlier sections, additional changes have been made to these drivers to enable them for Suite B.
- eDirectory to eDirectory Driver
-
The eDir-to-eDir Driver Certificates Wizard in iManager and Designer allows the use of stronger ciphers for encrypting the data as specified by Suite B. You import the Suite B compliant certificates into the certificate store that the driver uses. For more information, see Securing Driver Communication in the NetIQ Driver for eDirectory Implementation Guide.
- Active Directory Driver
-
The driver stores the password in the Windows registry. For Suite B compliance, the driver uses AES 256-bit encryption algorithm to encrypt the new passwords.
Passwords that are already in the registry are not re-encrypted with stronger ciphers because they are cleaned up when the event is processed. However, when new passwords are stored in the registry, they are encrypted with AES 256-bit keys.
2.19.3 Enabling Stronger Ciphers for SSL Communication
By default, Identity Manager supports the 128-bit SSL communication between the engine and the Remote Loader/ Fan-Out agent. The supported ciphers include:
-
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
-
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Oracle provides a default cryptographic jurisdiction policy file that limits the strength of cryptographic algorithms. When using stronger ciphers, you must increase the strength of encryption used. Cipher suites using key lengths greater than 128 bits, such as 256-bit AES encryption, require the JCE Unlimited Strength Jurisdiction policy files that enable additional cipher suites for Java in a separate JAR file.
To enable 256-bit or higher ciphers:
-
Download and extract the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files zipped file from Oracle's Java website to a temporary folder on your computer.
For example, download Java 8 JCE files from Oracle’s download page.
-
Navigate to the JRE path of your Identity Manager installation directory and save the local.policy.jar and US_export_policy.jar files to a different directory.
For example: /opt/novell/eDirectory/lib64/nds-modules/jre/lib/security
-
Replace these policy jars with the files you extracted in Step 1.
For detailed instructions, see the steps listed in the Readme.txt file included in the zipped file.
2.19.4 Verifying the Suite B Settings
When Suite B mode is enabled, the trace shows the cipher values and the TLS version that is used in the SSL communication.
To verify whether the communication is successful in Suite B mode, include a non-EC certificate in the configuration and verify that the trace file messages indicate that the Suite B certificate is not imported. For example, when Suite B is successfully enabled, the trace file can show entries similar to this:
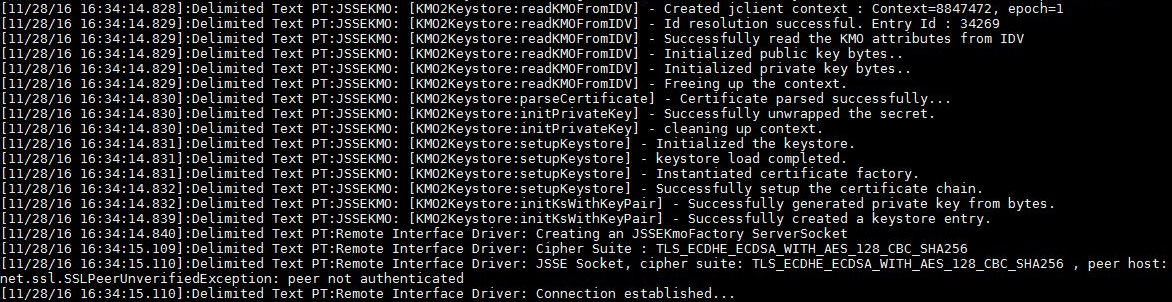
In case of an error, you will see messages similar to this:

If the certificate is not valid, the trace shows messages similar to this:
