1.0 Overview for Securing Identity Manager Components
Most organizations have their identity data stored on multiple systems. In this case, managing identities and monitoring user activity on physical and virtual environments are important. Identity Manager solution provides an automated environment to synchronize the identity data across multiple connected systems. It also ensures that users have access to the resources required for their jobs. As Identity Manager creates and stores a lot of user data, it is important to ensure that the data is protected from unauthorized use, access, and modification. To protect your data, we recommend a few security best practice guidelines for deploying and securing the Identity Manager system.
Figure 1-1 Securing the Identity Manager Components between Firewalls
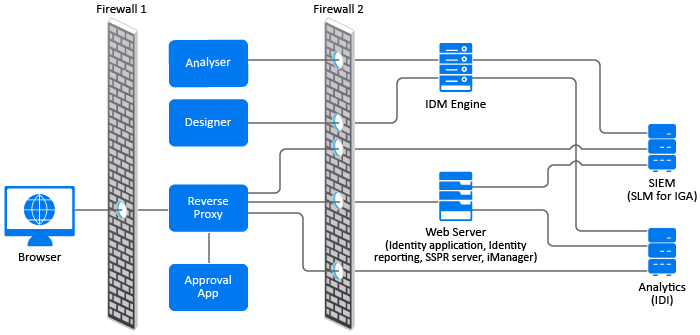
First Firewall: If you place a firewall between browsers and Analyser, Designer, Reverse Proxy, and Approval App you need to open ports so that browsers can communicate with these components. For more information on ports, see Understanding Identity Manager Communication.
Second Firewall: The second firewall separates IDM Engine, web servers, SIEM and Analytics Server from Analyser, Designer, Reverse Proxy and Approval App. For more information on security best practices, see Section 2.0, Security Best Practices.