2.2 Administrator and Manager Categories
Following are the general categories of administrators and managers used in identity applications:
- Domain Administrator
-
An administrator who has the full range of capabilities within a particular domain, and is able to perform all operations on all objects within the domain for all users.
- Domain Manager
-
A delegated administrator who has the ability to perform selected operations for a subset of authorized objects within the domain for all users.
- Team Manager
-
A business line manager who can perform selected operations for a subset of authorized objects within the domain, but only for a designated set of users (team members).
The following diagram illustrates the scope of identity applications administrators and managers:
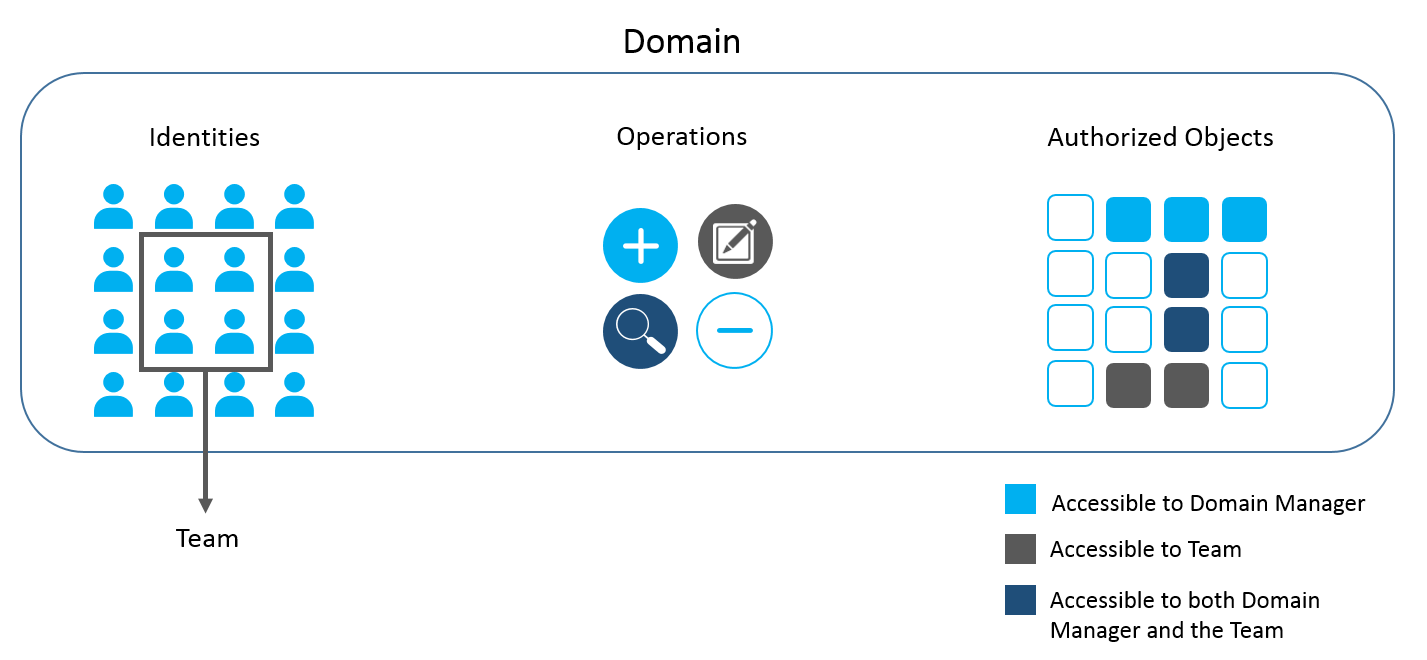
In this example, a Domain Administrator can perform all operations (create, modify, search, or delete) on all the authorized objects for all identities. A Domain Manager can perform the selected operations (create or search) on the selected authorized objects for all identities. A Team Manager can perform the selected operations (edit or search) on the selected objects for the set of identities that forms the team.
The identity applications do not restrict a Team Manager and a Domain Manager from accessing the same operations or authorized objects in the domain. In this example, the Team Manager and the Domain Manager have an access to search operations and some authorized objects.
2.2.1 Understanding Domain Administrators and Managers
The installation process initializes the Domain Administrators and Domain Managers system roles for the identity applications. However, during installation, you can specify only identity applications Administrator and allow all other assignments to default to this user. After installation, you can assign accounts to the roles.
All identity applications domains have respective administrator and manager to perform the operations on all objects within the domain. You must assign a user account to each administrators.
Following are the different administrators and managers used in identity applications:
- Provisioning Administrator
-
Required
A Domain Administrator who can perform all possible actions for all objects within the Provisioning domain.
- Provisioning Manager
-
A Domain Manager who can perform only allowed actions for a subset of objects within the Provisioning domain.
- Resource Administrator
-
Required
A Domain Administrator who can perform all possible actions for all objects within the Resource domain.
- Resource Manager
-
A Domain Manager who can perform only allowed actions for a subset of objects within the Resource domain.
- Role Administrator
-
Required
A Domain Administrator who can perform all possible actions for all objects (except for the System Roles) within the Role domain.
- Role Manager
-
A Domain Manager who can perform only allowed actions for a subset of objects within the Role domain.
- Security Administrator
-
Required
A Domain Administrator who can perform all possible actions for all objects within the Security domain. The Security domain allows the Security Administrator to configure access permissions for all objects in all domains within the Roles Based Provisioning Module.
The Security Administrator can configure s, and also assign domain administrators, delegated administrators, and other Security Administrators.
NOTE:For testing purposes, NetIQ does not lock down the security model in Standard Edition. Therefore, the Security Administrator is able to assign all domain administrators, delegated administrators, and also other Security Administrators. However, the use of these advanced features is not supported in production. In production environments, all administrator assignments are restricted by licensing. NetIQ collects monitoring data in the audit database to ensure that production environments comply. Furthermore, NetIQ recommends that only one user be given the permissions of the Security Administrator.
- Team Manager
-
A user designated for a team who can perform provisioning requests and approval tasks associated with the team. Team manager is allowed to request or revoke permissions of team members. An administrator can configure a Team Manager capabilities to delegate tasks for team members.
Although a team might match a group that exists in the user directory, teams are not the same thing as groups. A group or a member of a group cannot perform team capabilities except when assigned to a team. For more information, see Managing Users in NetIQ Identity Manager - User’s Guide to the Identity Applications.
For more information about:
-
Assigning administrators, see Section 7.0, Assigning the Identity Applications Administrators.
-
Managing teams and team managers, see Managing Teams in NetIQ Identity Manager - User’s Guide to the Identity Applications.