3.2 Key Features and Benefits of Architecture
The Identity Manager architecture is flexible and scalable, and provides the following features:
3.2.1 Staged Deployment
To avoid risk to your production Identity Manager environment, you can deploy Identity Manager in separate stages. For example, deploying to a development environment, then to a test environment, and finally to production. This process allows you to apply improvements and test changes in the project in each stage. Staging provides the flexibility to validate applications in real time to ensure no data loss and uniformity across all stages. It helps you to reduce complexity in your deployment process because you can to test your Identity Manager project at multiple stages before the project is live.
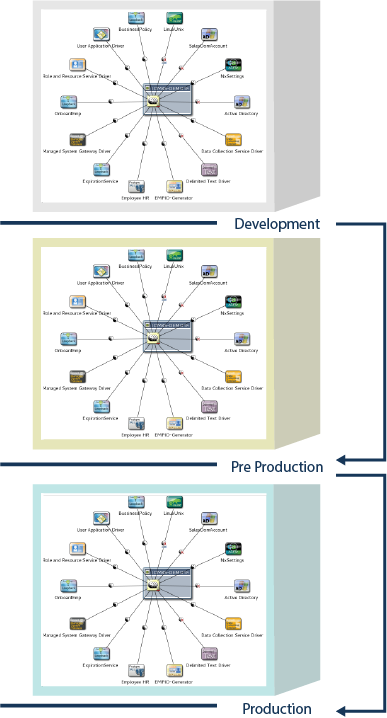
The simplest, most efficient way to stage your Identity Manager project is by using the package management functionality in Designer. Packages are configured to keep server-specific settings separate from the actual Identity Manager content. You move all of your policies, rather than your server configurations, from one stage to the next.
3.2.2 Flexibility and Extensibility
You can deploy Identity Manager to single or multiple server instances, depending on the functionality that you need. Multiple server instances provide optimal configuration options by supporting geographically dispersed users and resources for increased flexibility, performance, and control.
You can install Identity Manager in a clustered environment for achieving high availability in some environments. Clustering is supported for Identity Manager engine and Identity Applications. components. For more information about high availability implementations, see the Setup Guide.
The architecture of NetIQ Identity Manager includes a built-in Identity Vault so you do not need to create and manage a separate directory structure for identity purposes. The Identity Vault is basically an eDirectory tree. It serves as a database that contains centralized identity and access information.
Depending on the extent of data that propagates from connected system into the Identity Vault, you can customize the Identity Vault. If you are installing your first Identity Manager system, use the default settings to help you quickly set up a system. For deploying Identity Manager in large enterprises, you can install individual components on different servers and customize the settings to suit your requirements.
Due to its object-oriented design and a distributed deployment support, Identity Vault is scalable to manage billions of objects. With its powerful schema management and granular data replication, it enables each application to reference a coherent set of identity values without needlessly replicating information across systems. As with all Identity Manager components, the Identity Vault can run in a wide range of operating environments. Additionally, its deployment as a central identity repository does not limit your ability to use other credential store technologies for other application or infrastructure uses.
3.2.3 Reuse of Existing Infrastructure
Identity Manager is built on an open architecture. This allows Identity Manager to integrate with the existing IT infrastructure and leverage existing software and already running applications of an organization. For example, if your Identity Manager implementation requires integrating with an existing company portal or a user management system, you can make use of standards-based APIs, such as REST, SOAP, SPML, JDBC, LDAP, and more. This allows you to customize the Identity Manager solution to meet the specific needs of the organization. You can also create connections to other applications with Google* Web Toolkit or Microsoft* Silverlight*. Using the APIs, Identity Manager can easily integrate various end-user activities such as password changes, password challenges, and role requests into existing environments, such as a company web portal.
For users to create, modify, and request permission for roles and resources, Identity Manager provides browser-based interfaces that they can access from workstations or mobile platforms. These interfaces support single sign-on access. Administrators, managers, and resource owners can carry out operational activities such as monitoring open workflows, workflow reassignment, and role and resource management.
3.2.4 Extensive Identity Integration
Identity Manager provides an identity integration framework that connects and synchronizes identity information across the organization environment.
The identity integration infrastructure enables administrators to create and modify identity information once and then have that data propagated to all their connected systems. For fast and low-cost deployments, Identity Manager provides this level of data synchronization through its unique and extensible integration architecture and preconfigured drivers. When the drivers are deployed, Identity Vault maintains driver configurations in a set of directory objects. For information about preconfigured drivers, see the Identity Manager Driver Documentation Website.
Identity Manager also enables you to define user organizational hierarchies and user groups with the use of its built-in hierarchy and inheritance, as well as native role-based access control. Administrators can easily and quickly use simple policies and access control lists to regulate information access, manage change authorization and enable self-service without heavy credentials.
Identity Manager also helps you to manage application parameters and entitlements, and to view a history of resource allocations. In addition, it provides delegated administration with permission settings for user management.
Identity Manager contains a web-based user self-service portal that can be customized. This portal helps you extensively in user management. It gives users and business administrators the ability to perform a variety of identity self-service and roles provisioning tasks, including managing passwords and identity data, initiating and monitoring provisioning and role assignment requests, managing the approval process for provisioning requests, and verifying attestation reports. It includes the workflow engine that controls the routing of requests through the appropriate approval process. For more information, see the NetIQ Identity Manager - Administrator’s Guide to the Identity Applications.
3.2.5 Built-in Audit and Compliance
The core identity management architecture includes auditing and compliance capabilities. When you bring a resource under identity management, the connection can be leveraged for both provisioning and compliance use, avoiding duplication of integration cost. Its integrated reporting provides the visibility into user entitlements and associated activities for compliance audits, with out-of-the-box support for regulations. The audit service can optionally integrate with NetIQ Sentinel for report analysis. For more information, see the Administrator Guide to NetIQ Identity Reporting.