5.1 Design Constraints
In general, you install the Identity Manager components on specific servers, as described in the NetIQ Identity Manager Setup Guide for Linux or NetIQ Identity Manager Setup Guide for Windows. When configuring the identity applications, you also need to consider the following architectural constraints:
- One user container per identity applications instance
-
No instance of the identity applications can service, such as search, query, or add users to, more than one user container. Also, a user container association with the applications is meant to be permanent.
- One User Application driver per identity applications instance
-
No User Application driver can be associated with more than one instance of the identity applications, except when the applications are installed on sister nodes of the same cluster. In other words, Identity Manager does not support a one-to-many mapping of drivers to identity applications instances.
The first constraint enforces a high degree of encapsulation in User Application design. Suppose you have the following organizational structure:
Figure 5-1 Sample Organizational Structure
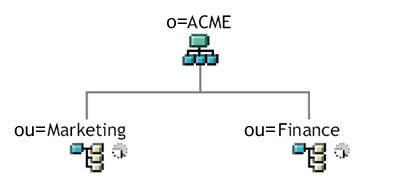
During installation of the identity applications, you are asked to specify the top-level user container that your installation looks for in the Identity Vault. In this case, you could specify ou=Marketing,o=ACME or (alternatively) ou=Finance,o=ACME identity applications. You cannot specify both. All searches and queries (and administrator logins) for the are connected to whichever container you specify.
NOTE:In theory, you could specify a scope of o=ACME in order to encompass Marketing and Finance. But in a large organization, with potentially many ou containers (rather than just two relating to Marketing and Finance), this is not likely to be practical.
It is possible to create two independent installations of the identity applications that share no resources in common: one for Marketing and another for Finance. Each installation would have its own database and its own appropriately configured User Application driver. Also, each would be administered separately, possibly having unique User Application drivers.
If you truly need to place Marketing and Finance within the same scope for one installation, you can consider one of the following tactics:
-
Insert a new container object (for example, ou=MarketingAndFinance) in the hierarchy, above the two sibling nodes; then point to the new container as the scope root.
-
Create a filtered replica (a special type of eDirectory tree) that combines the needed parts of the original ACME tree, and point the identity applications at the replica’s root container. For more information about filtered replicas, see the eDirectory Administration Guide.
If you have questions about a particular system layout, contact your NetIQ representative for assistance or advice. For more information about design constraints, see Planning Overview
and Considerations for Installing Identity Manager Components
in the NetIQ Identity Manager Setup Guide for Linux and Planning to Install the Identity Applications
in the NetIQ Identity Manager Setup Guide for Windows.