6.8 Modifying Trustee Rights
To perform tasks within the identity applications, users must have specific trustee rights.
6.8.1 Modifying the Trustee Rights for User Preferences
To allow user preferences to be saved, the administrator must ensure that the permissions on the srvprvUserPrefsPlus and srvprvQueryList attributes are set so that the user is able to write to these attributes. The necessary rights should be set for [This] at the tree root level, since [This] is a special alias to the object itself, causing only the user to have rights to modify its own preferences. To set the proper permissions, the administrator needs to modify the trustees for these attributes in iManager, as shown below:
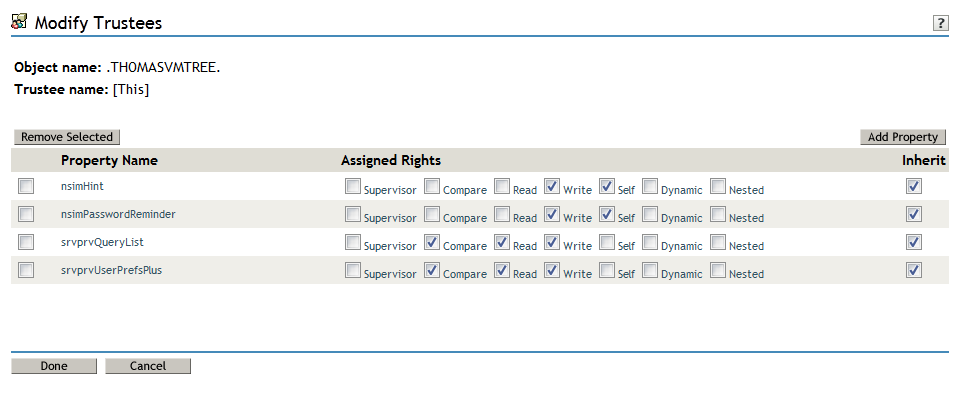
The srvprvUserPrefsPlus property has no space limitations, so it can save a large amount of user preference information. If you have used the srvprfUserPrefs property in a previous release, this property will be migrated to srvprvUserPrefsPlus the first time a user saves new preferences in the User Application.
6.8.2 Modifying the Trustee Rights for a Provisioning Request Definition
To view the details and comments associated with a task in the Task Notifications section of the Work Dashboard tab, the Domain Administrator or Delegated Administrator must have the proper rights to the provisioning request definition. In particular, the user must have the nrfAccessMgrTaskAddressee right to the provisioning request definition, with write access enabled. To set the proper permissions, the administrator needs to modify the trustees for the provisioning request definition, as described below:
-
Log into iManager as an administrator.
-
Select Modify Trustee from the Rights left-navigation menu.
-
Browse to the provisioning request definition.
-
If necessary, click Add Trustee to add the user.
-
Click on the Assign rights link.
Notice that nrfAccessMgrTaskAddressee is not listed with the write permission checked, which means that the user does not have the proper rights for the provisioning request definitiion.
-
Click the Add Property button.
-
Check the check box for Show all properties in schema.
-
Select nrfAccessMgrTaskAddresss.
-
Check the write checkbox for Assigned Rights.
-
Click Done.
-
Click OK.
6.8.3 Restricting a User from Viewing Provisioning Request Definitions and Roles in Identity Applications
Using Designer or iManager, you can restrict users from viewing roles or provisioning request definitions (PRDs) in Identity Applications for which they are not assigned as trustees. Trustee assignments can be configured for users, groups, and containers.
-
To restrict a user from viewing roles, control the users’ permission to the RoleDefs container by setting the user as a trustee of individual roles in the Identity Vault.
-
To restrict a user from viewing PRDs for which the user is not assigned as a trustee, modify the trustee assignments for the RequestDefs container.
Perform the following steps to modify the trustee assignments for the RoleDefs container in iManager:
-
In Roles and Tasks, select Rights > Modify Trustees.
-
Browse to the container whose trustee list you want to modify, and then click OK.
This opens a list of the object’s currently assigned trustees. For example, RoleDefs.AppConfig.UserApplication Driver.driverset1.system.
-
Add a trustee to the container by clicking Add Trustee, and then select [Public].
-
Click Assigned Rights to assign the trustee's rights.
-
Deselect all options under Assigned Rights for the [All Attributes Rights] property.
-
Select Browse for the [Entry Rights] property. Ensure that all assigned rights are deselected and only Inherit is selected.
-
Click Done.
To restrict a user from viewing PRDs, repeat Steps 1-7 for the RequestDefs container.