13.2 Deciding When to Install SLM for IGA
Sentinel is the preferred audit event destination for Identity Manager. Identity Manager provides event forwarding capabilities to Sentinel by configuring Sentinel Link using Sentinel Event Source Management (ESM).
If you are already using Sentinel for auditing or as an integration framework for tracking identities, you might choose to use your existing Sentinel for auditing events instead of installing SLM for IGA. Regardless of whether you choose to reuse your existing installation or perform a new installation of SLM for IGA shipped with Identity Manager, you must create a synchronization policy on the Sentinel server for auditing events. The Identity Reporting installation directory includes Data Synchronization utility. The utility creates a synchronization policy on Sentinel that synchronizes events to an external SQL database. For more information, see Creating the Data Synchronization Policy.
NOTE:Sentinel Log Management for IGA does not support all features of Sentinel, such as Correlation, Distributed Search, Scalable Storage Routing, Security Intelligence, and all collectors that are not related to Novell and NetIQ products.
13.2.1 Overview of Changes
The following list includes the important changes made to the auditing framework:
-
SLM for IGA 8.0.1 replaces Event Auditing Service (EAS) as an event auditing service for Identity Reporting.
-
The Data Synchronization utility sets up a data synchronization policy in SLM for IGA or an existing Sentinel server.
-
The Data Synchronization policy synchronizes the filtered event data from a Sentinel server or SLM for IGA with the Identity Reporting database.
-
The Data Synchronization utility synchronizes data to a new table, sentinel_events, in the public schema of the PostgresSQL Reporting database. This table is located in IDM_RPT_DATA user in the Oracle database.
-
The synchronization utility provides an option to delete the existing Report Data Definitions (RDD) on a SLM for IGA server. However, you must not delete RDDs on an external Sentinel server or on an identity tracking solution.
Also, the Reporting views have been simplified. The following list includes the important changes made to Identity Reporting:
-
The following new views have been created:
-
idmrpt_auth_by_serv_v
-
idmrpt_auth_by_user_v
-
idmrpt_events_v2
-
idmrpt_self_pass_change_v
-
-
The following views are modified:
-
idmrpt_identity_cs_v
-
idmrpt_identity_v
-
idmrpt_idv_acct_v
-
idmrpt_res_trust_v
-
idmrpt_user_parameter_v
-
-
Reporting data (excluding event data) migrated from Identity Manager 4.5 can be used with the reports supported with this version of Identity Manager.
-
This version of Identity Reporting uses sentinel_events table. Therefore, it does not use audit data from a prior version of Identity Manager.
13.2.2 Recommended Installation Scenarios
The following scenarios help you evaluate if a new installation of SLM for IGA is required for your environment:
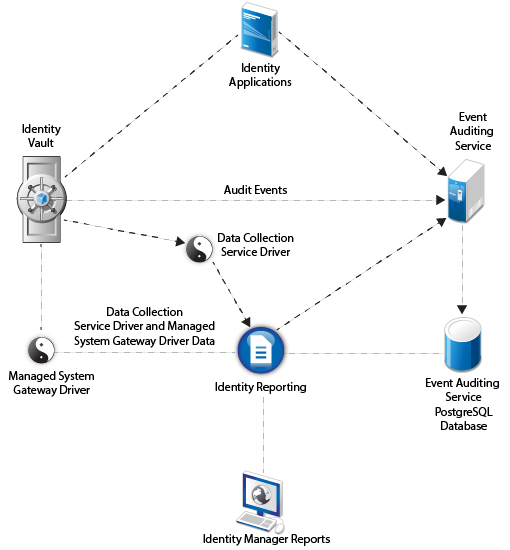
Scenario I: Environment with Event Auditing Service and Identity Reporting
This is the most common scenario where you have only EAS installed and you do not have an existing installation of Sentinel or an identity tracking solution in your environment. The following figure illustrates this scenario:
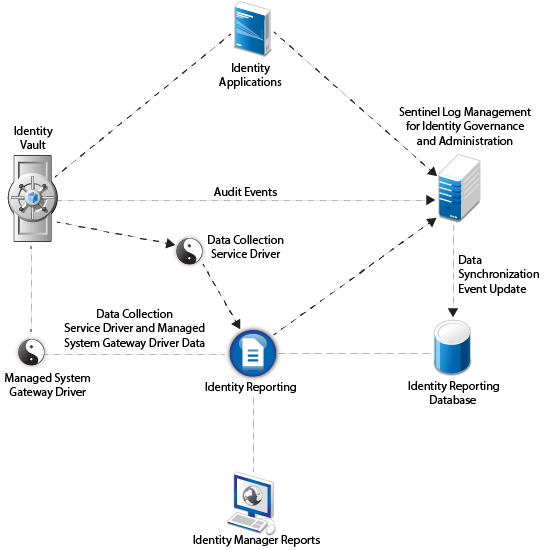
You must install SLM for IGA that ships with Identity Manager because EAS is not supported with this version of Identity Manager as depicted in the following figure:
Follow these high-level steps to configure auditing in this environment:
-
Migrate the existing Reporting data to another standalone PostgreSQL instance. For more information, see Migrating from Event Auditing Service to Sentinel Log Management for IGA.
-
To generate reports in Identity Manager, perform a new installation of Identity Reporting. For more information, see Section XIII, Installing Identity Reporting.
-
Run the data synchronization utility to create a policy in SLM for IGA that synchronizes the Identity Manager events with the Identity Reporting database. For more information, see Creating the Data Synchronization Policy.
Scenario II: Environment with Event Auditing Service, an existing Sentinel server, and Identity Reporting
This configuration includes EAS, an existing installation of Sentinel or an identity tracking solution, and Identity Reporting. The following figure illustrates this scenario:
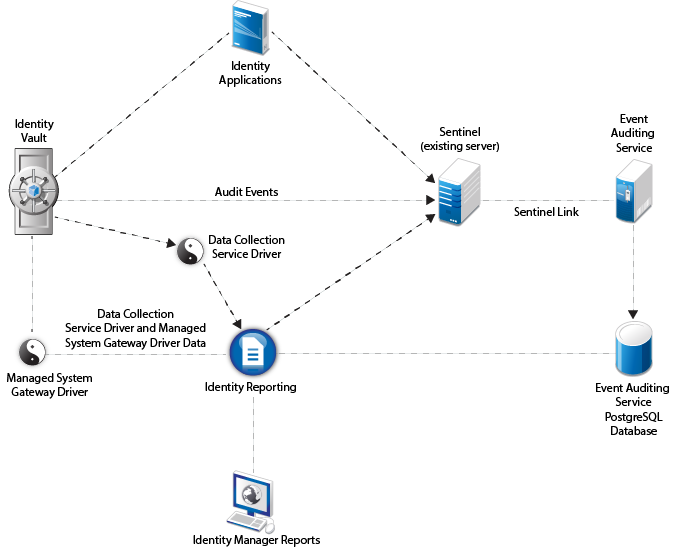
If you choose to use the existing Sentinel server, configure this server as a source of audit data instead of EAS as depicted in the following figure:
Follow these high-level steps to configure auditing in this environment:
-
Migrate the existing Reporting data to another standalone PostgreSQL instance. For more information, see Migrating from Event Auditing Service to Sentinel Log Management for IGA.
-
To generate reports in Identity Manager, perform a new installation of Identity Reporting. For more information, see Section XIII, Installing Identity Reporting.
-
Create a policy in the existing Sentinel server to synchronize the audit data from the Identity Manager components with the Identity Reporting database. You must use it as a source of audit data instead of EAS. For more information, see Creating the Data Synchronization Policy.
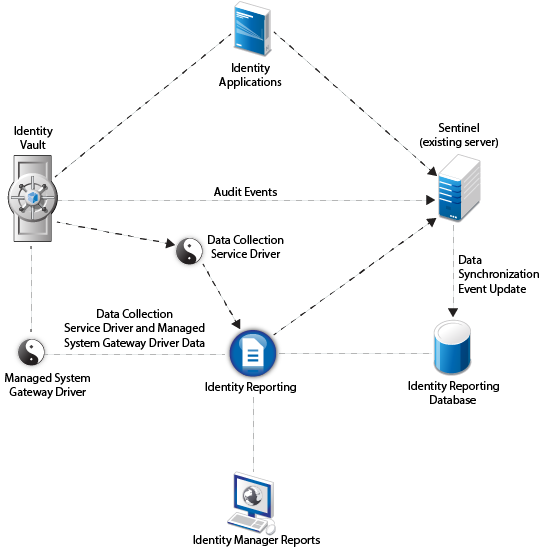
If you want to use SLM for IGA instead of an existing Sentinel server, install SLM for IGA that ships with Identity Manager and then configure it as the source of audit data as depicted in the following figure:
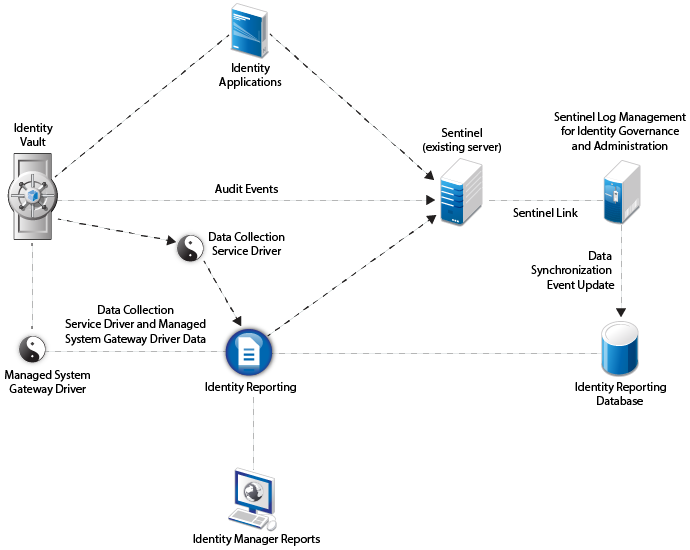
Follow these high-level steps to configure auditing in this environment:
-
Migrate the existing reporting data to another standalone PostgreSQL instance. For more information, see Migrating from Event Auditing Service to Sentinel Log Management for IGA.
-
To generate reports in Identity Manager, perform a new installation of Identity Reporting. For more information, see Section XIII, Installing Identity Reporting.
-
Forward Identity Manager events from SLM for IGA to the existing Sentinel server by configuring Sentinel Link between these servers. For more information on configuring Sentinel Link, see the Sentinel Link Overview Guide.
-
Create a policy in the SLM for IGA server to synchronize the audit data from Identity Manager components with the Identity Reporting database. For more information, see Creating the Data Synchronization Policy.